This post is co-written with Rudra Kannemadugu and Shravan K S from Indegene Limited. In today’s digital-first world, healthcare conversations…
Development
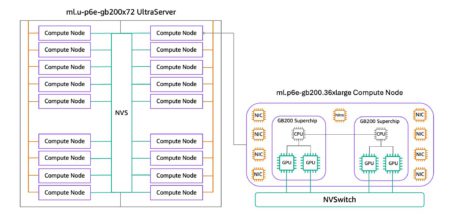
Imagine harnessing the power of 72 cutting-edge NVIDIA Blackwell GPUs in a single system for the next wave of AI…
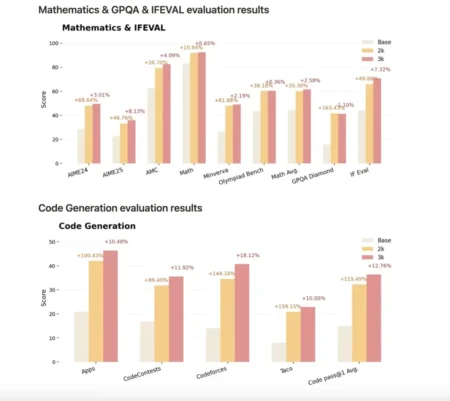
Table of contents What Is ProRLv2? Key Innovations in ProRLv2 How ProRLv2 Expands LLM Reasoning Why It Matters Using Nemotron-Research-Reasoning-Qwen-1.5B-v2…
Learn the essential concepts of DevSecOps and why integrating security throughout the software development lifecycle is more important than ever.…
Deep dive into Insurify’s insurance marketplace technology: 400+ carrier API connections, sub-10-second quote delivery, and intelligent matching algorithms. Continue reading…
Ready to go from “meh” to “whoa” with your AI coding assistant? Here’s how to get started. You’ve installed GitHub…
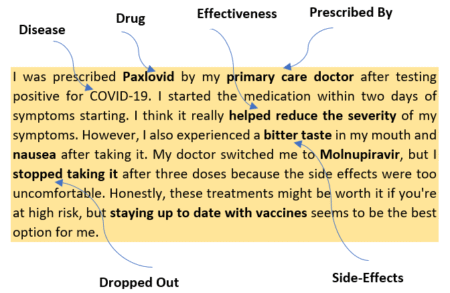
The pressure is on for healthcare organizations to deliver more—more value, more equity, more impact. That’s where a well-known approach…
Perficient is delighted to announce that Pradeep Jain, Senior Solution Architect, has been honored by Microsoft as a FastTrack Recognized…
In today’s fast-moving world of software development, keeping our code clean, secure, and efficient is more important. While manual code…
ESET Research discovered a zero-day vulnerability in WinRAR being exploited in the wild in the guise of job application documents;…
The attacks used spearphishing campaigns to target financial, manufacturing, defense, and logistics companies in Europe and Canada, ESET research finds…
The U.S. authorities have secured the extradition of three Ghanaian nationals accused of running a fraud operation that stole over…
The Dutch National Cyber Security Centre (NCSC-NL) has warned of cyber attacks exploiting a recently disclosed critical security flaw impacting…
The Dutch National Cyber Security Centre (NCSC) has confirmed that a serious vulnerability in Citrix NetScaler systems, identified as CVE-2025-6543,…
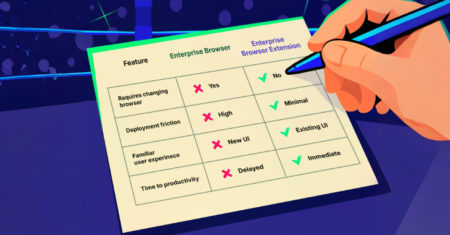
Most security tools can’t see what happens inside the browser, but that’s where the majority of work, and risk, now…
A previously undocumented threat actor dubbed Curly COMrades has been observed targeting entities in Georgia and Moldova as part of…
In episode 63 of The AI Fix, Unitree Robotics looks to Black Mirror episode “Metalhead” for tips on marketing its…
The United States Department of Justice has revealed that the recent takedown of the BlackSuit ransomware gang’s servers, domains, and…
An ongoing data extortion campaign targeting Salesforce customers may soon turn its attention to financial services and technology service providers,…
Cybersecurity researchers are warning of a “significant spike” in brute-force traffic aimed at Fortinet SSL VPN devices. The coordinated activity,…