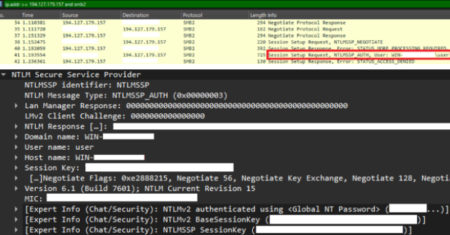
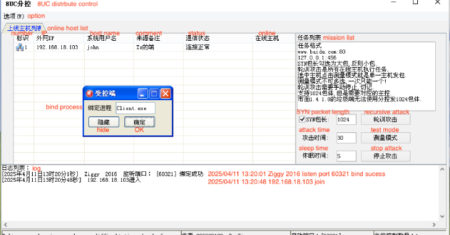
A new multi-stage attack has been observed delivering malware families like Agent Tesla variants, Remcos RAT, and XLoader. “Attackers increasingly…
Development
It’s official. China has just taken a step straight out of science fiction and plunged it into the depths of…
Programmers can now use large language models (LLMs) to generate computer code more quickly. However, this only makes programmers’ lives…
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a medium-severity security flaw impacting Microsoft Windows to its…
Cybersecurity researchers are warning of continued risks posed by a distributed denial-of-service (DDoS) malware known as XorDDoS, with 71.3 percent…
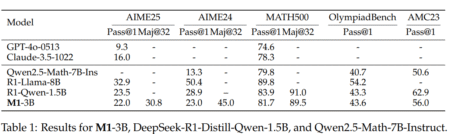
Effective reasoning is crucial for solving complex problems in fields such as mathematics and programming, and LLMs have demonstrated significant…
Evaluating LLMs has emerged as a pivotal challenge in advancing the reliability and utility of artificial intelligence across both academic…
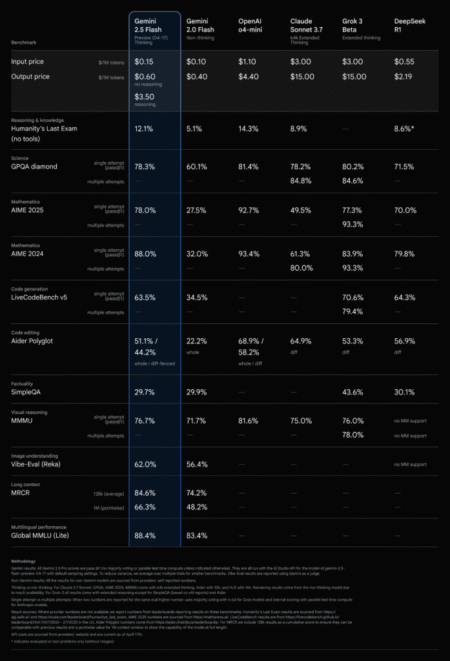
Google has introduced Gemini 2.5 Flash, an early-preview AI model accessible via the Gemini API through Google AI Studio and…
OpenAI has published a detailed and technically grounded guide, A Practical Guide to Building Agents, tailored for engineering and product…
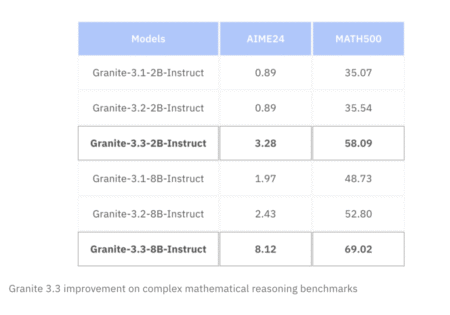
As artificial intelligence continues to integrate into enterprise systems, the demand for models that combine flexibility, efficiency, and transparency has…
In this tutorial, you’ll learn about copying objects in Python using the copy module. We’ll cover how to use the…
Modern data pipelines are the backbone of data engineering, enabling organizations to collect, process, and leverage massive volumes of information…
Laravel is a popular PHP web development framework known for its elegant syntax, developer-friendly tools, and built-in features for routing,…
Model Context Protocol makes it incredibly easy to integrate powerful tools directly into modern IDEs like Cursor, dramatically boosting productivity.…
Part 1: Uploading a Dataset to Hugging Face Hub Introduction This part of the tutorial walks you through the process…
AI systems are becoming increasingly dependent on real-time interactions with external data sources and operational tools. These systems are now…
Think about it: you’re sitting there enjoying your morning coffee, reading the headlines when again another data breach is making…
If you have a solar inverter setup, one thing you would agree on with me is that data from your…