Understanding AI Agents’ Role in Insurance How Does Rigorous Software Testing Help Avoid Such Issues? Use Cases of AI Agents in Insurance Key Benefits of AI Agents in Insurance How can Tx Help You Improve Your AI Agents Quality? Summary In the rapidly evolving insurance ecosystem, balancing regulatory changes with dynamic customer needs is one … Top 5 Use Cases for AI Agents in the Insurance Industry
The post Top 5 Use Cases for AI Agents in the Insurance Industry first appeared on TestingXperts.
Development
OpenTelemetry integration for laravel Source: Read MoreÂ
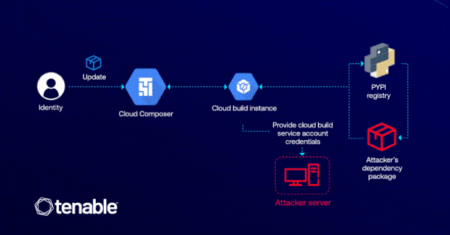
Cybersecurity researchers have detailed a now-patched vulnerability in Google Cloud Platform (GCP) that could have enabled an attacker to elevate…
MongoDB regularly collaborates with open source innovators like David Bekker, a Drupal core contributor with over 600 commit credits. David’s…
OpenAI CEO Sam Altman has revealed that merely being polite to ChatGPT might be costing “tens of millions of dollars”…
Latest PECL Releases: brotli 0.16.0 – change: brotli.state resource in brotli_uncompress_{init,add}() to BtorliUnCompressContext class change: brotli.state resource in brotli_compress_{init,add}() to…
Comments Source: Read MoreÂ
JavaScript is single-threaded. That means it runs one task at a time, on one core. But then how does it…
The Syntech Firebase Cloud Messaging (FCM) package for Laravel makes it easy to use Laravel’s notification system to send Firebase…
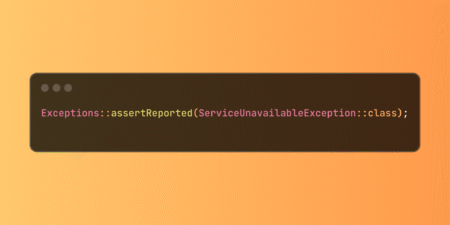
Master Laravel’s assertReported method from the Exceptions facade to effectively test that your application correctly captures and reports exceptions during…
The Moroccan authorities have warned users of a critical vulnerability in the popular WordPress plugin, InstaWP Connect. The General Directorate…
Microsoft on Monday announced that it has moved the Microsoft Account (MSA) signing service to Azure confidential virtual machines (VMs)…
MITRE has officially unveiled its highly anticipated D3FEND CAD tool as part of the D3FEND 1.0 release. This new Cyber…
In what has been described as an “extremely sophisticated phishing attack,” threat actors have leveraged an uncommon approach that allowed…
As SaaS and cloud-native work reshape the enterprise, the web browser has emerged as the new endpoint. However, unlike endpoints,…
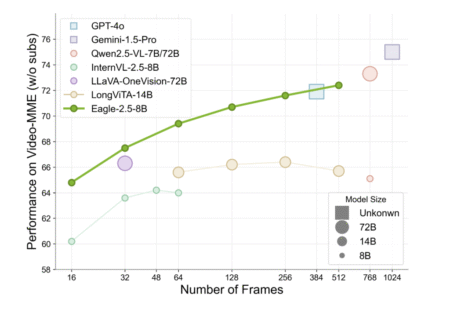
In recent years, vision-language models (VLMs) have advanced significantly in bridging image, video, and textual modalities. Yet, a persistent limitation…
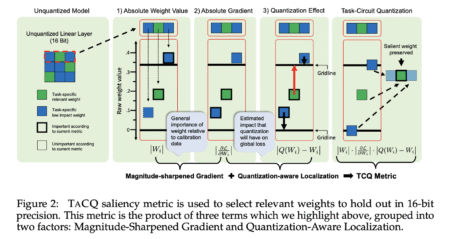
LLMs show impressive capabilities across numerous applications, yet they face challenges due to computational demands and memory requirements. This challenge…
HPE Performance Cluster Manager Vulnerability Allow Remote Attacker to Bypass Authentication
A critical vulnerability in Hewlett Packard Enterprise‘s Performance Cluster Manager has been identified, enabling attackers to remotely bypass authentication safeguards.
The flaw, formally documented …
Read more
Published Date:
Apr 22, 2025 (3 hours, 49 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-27086
Critical Windows Update Stack Vulnerability Allows Code Execution & Privilege Escalation
A security flaw has been identified in the Windows Update Stack, exposing millions of Windows systems to the risk of unauthorized code execution and privilege escalation.
Tracked as CVE-2025-21204, th …
Read more
Published Date:
Apr 22, 2025 (3 hours, 44 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-29824
CVE-2025-21204
Google’s email spoofed by cunning phisherfolk who re-used DKIM creds
Infosec In Brief Email security outfit EasyDMARC recently spotted a phishing campaign that successfully spoofed Google with a sophisticated attack.
As explained in a technical breakdown, the attackers …
Read more
Published Date:
Apr 22, 2025 (3 hours, 41 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-25234
CVE-2025-25230
CVE-2025-31201
CVE-2025-31200
CVE-2021-20035