#730 — April 4, 2025 Read on the Web JavaScript Weekly Bare: A New Lightweight Runtime for Modular JS Apps…
Development
Driven by advancements in vehicle connectivity, autonomous systems, and electrification, the automotive and mobility industry is currently undergoing a significant…
This post is co-written with Paul Pagnan from Lumi. Lumi is a leading Australian fintech lender empowering small businesses with…
Large language models (LLMs) can be used to perform natural language processing (NLP) tasks ranging from simple dialogues and information…
Due to the inherent ambiguity in medical images like X-rays, radiologists often use words like “may” or “likely” when describing…
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
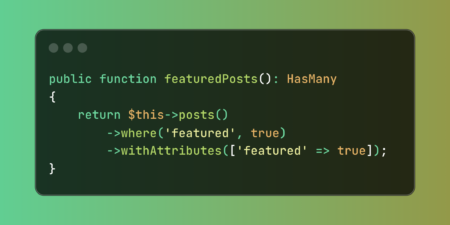
Maintain data consistency in your Laravel application with the withAttributes relationship method. This feature ensures newly created models automatically inherit…
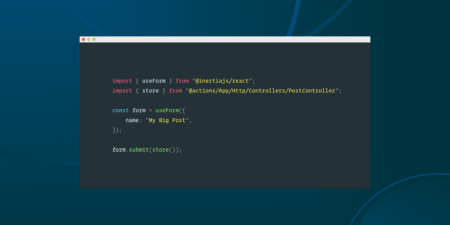
The Laravel team released Laravel Wayfinder, a new first-party package that bridges your routes between the frontend and backend. The…
Laravel Subscriptions is a flexible plans and subscription management system for Laravel, with the required tools to run your SAAS…
A maximum severity security vulnerability has been disclosed in Apache Parquet’s Java Library that, if successfully exploited, could allow a…
The Computer Emergency Response Team of Ukraine (CERT-UA) has revealed that no less than three cyber attacks were recorded against…
A novice cybercrime actor has been observed leveraging the services of a Russian bulletproof hosting (BPH) provider called Proton66 to…
Ivanti has disclosed details of a now-patched critical security vulnerability impacting its Connect Secure that has come under active exploitation…
A series of cyberattack have impacted some of Australia’s largest superannuation funds, likely compromising over 20,000 member accounts. The authorities…
There’s a virtuous cycle in technology that pushes the boundaries of what’s being built and how it’s being used. A…
The cascading supply chain attack that initially targeted Coinbase before becoming more widespread to single out users of the “tj-actions/changed-files”…
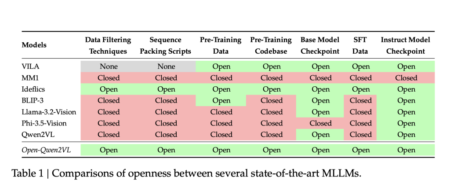
Multimodal Large Language Models (MLLMs) have advanced the integration of visual and textual modalities, enabling progress in tasks such as…
It’s rare for legal reports, government consultations, and anime-styled selfies to feel part of the same story – but the…
Renewable power sources have seen unprecedented levels of investment in recent years. But with political uncertainty clouding the future of…