In the ever-evolving world of software development, efficiency and speed are key. As projects grow in complexity and deadlines tighten, AI-powered tools have become vital for streamlining workflows and improving productivity. One such game-changing tool is JetBrains AI Assistant a powerful feature now built directly into popular JetBrains IDEs like IntelliJ IDEA, PyCharm, and WebStorm.
The post JetBrains AI Assistant : Revolutionizing Tech Solutions appeared first on Codoid.
Development
When some commuter trains arrive at the end of the line, they must travel to a switching platform to be…
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
The U.S. government funding for non-profit research giant MITRE to operate and maintain its Common Vulnerabilities and Exposures (CVE) program…
Comments Source: Read MoreÂ
April 10–11, 2025, marked an exciting milestone for Perficient India as we hosted our very first hackathon – Perfathon 2025.…
Academic institutions have a unique set of characteristics that makes them attractive to bad actors. What’s the right antidote to…
Natural language interface to databases is a growing focus within artificial intelligence, particularly because it allows users to interact with…
Tabular data is widely utilized in various fields, including scientific research, finance, and healthcare. Traditionally, machine learning models such as…
On May 21, we’re heading to the Agentforce World Tour in New York — and bringing the future of AI…
The COVID-19 pandemic has left an indelible mark on global health, with one of the most pressing concerns being the…
Enable or disable Xdebug extension for Laravel Herd The post Herd Xdebug Toggler for Visual Studio Code appeared first on…
Cybersecurity researchers have disclosed a malicious package uploaded to the Python Package Index (PyPI) repository that’s designed to reroute trading…
A critical security vulnerability has been disclosed in the Apache Roller open-source, Java-based blogging server software that could allow malicious…
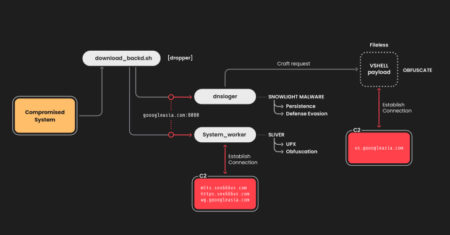
The China-linked threat actor known as UNC5174 has been attributed to a new campaign that leverages a variant of a…
In episode 46 of The AI Fix, China trolls US tariffs, a microscopic pogoing flea-bot makes a tiny leap forward…
RansomHouse is a cybercrime operation that follows a Ransomware-as-a-Service (RaaS) business model, where affiliates (who do not require technical skills…
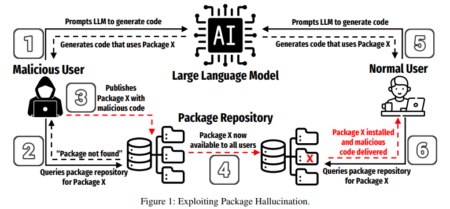
Code-generating large language models (LLMs) have introduced a new security issue into software development: Code package hallucinations. Package hallucinations occur…
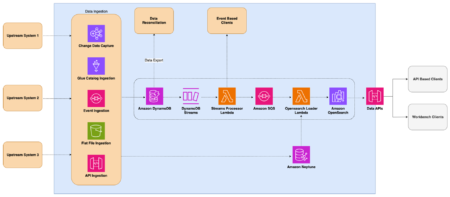
Amazon Finance Automation (FinAuto) is the tech organization of Amazon Finance Operations (FinOps). Its mission is to enable FinOps to…