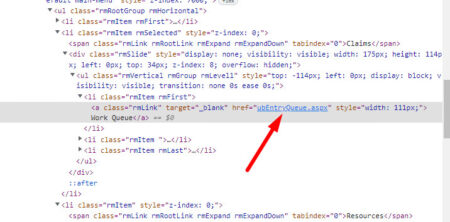
I’m working on a mobile automation task where I need to run test suites in parallel for 3 different iOS apps. Each test suite has its own testng.xml with a section configured to run on a device.
I tried mvn clean test -Dthreads=3 -Dsuites=full path 1 to the suite, full path 2 to the suite, full path 3 to the suite
Here threads and suites are properties defined in pom.xml.
It looks like the suiteXMLFile in pom.xml cannot take absolute path. It works fine, when I do: mvn clean test -Dthreads=1 -Dsuites=src/test/resources/testng.xml.
How do I run the suites on all 3 devices in parallel with the test suites lying in 3 different folders pointing to 3 different devices?
Appreciate help.


![[error]Cmd.exe exited with code ‘1’ in Azure Pipeline](https://devstacktips.com/wp-content/uploads/2024/08/k86Aa-m3ATCF-450x180.jpg)
