Welcome to Part 2 of this blog series! In Part 1, we discussed the high-level architecture and use case for…
Development
Building Bridges Through Executive Allyship to Support LGBTQ+ Inclusion Perficient’s PRISM Employee Resource Group (ERG) launched an initiative to engage…
This blog shows you how to install and set up the Flow application as part of the Total.js IoT platform,…
Total.js Tables is a no-code tool for designing and managing database tables on top of PostgreSQL. Source: Read More
Workday, a California-based human resource and financial management service provider, disclosed last week that it was recently targeted in a…
Calling out the cybersecurity community to mark their calendars! The Cyber Express is all set to release, this week, its…
In a forward-looking proposal introduced last week, the Australian Competition and Consumer Commission (ACCC) has invited public submissions on a…
Organizations handling various forms of sensitive data or personally identifiable information (PII) require adherence to regulatory compliance standards and frameworks.…
Cybersecurity researchers have discovered a malicious package in the Python Package Index (PyPI) repository that introduces malicious behavior through a…
Colt Technology Services, a major UK-based telecommunications provider, continues to experience service disruptions following a serious cyberattack that began on…
Power doesn’t just disappear in one big breach. It slips away in the small stuff—a patch that’s missed, a setting…
Toronto-based Bragg Gaming Group, a provider of content and technology solutions for the online gaming sector, announced that it was…
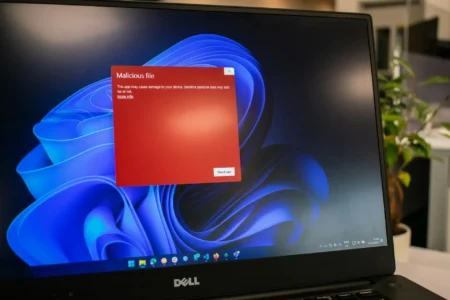
Cybersecurity researchers have lifted the lid on the threat actors’ exploitation of a now-patched security flaw in Microsoft Windows to…
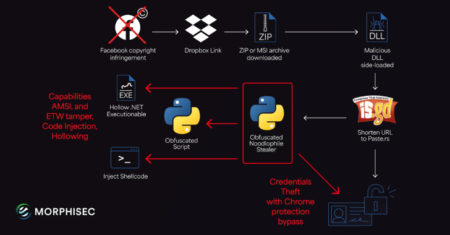
The threat actors behind the Noodlophile malware are leveraging spear-phishing emails and updated delivery mechanisms to deploy the information stealer…
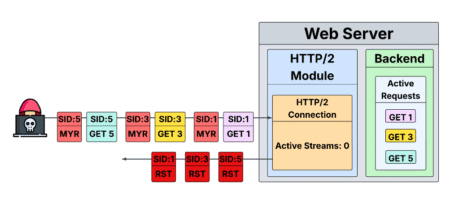
A new HTTP/2 denial of service (DoS) vulnerability that circumvents mitigations put in place after 2023’s “Rapid Reset” vulnerability is…
Most AI pilots stall after early wins, not because of weak models, but fragile architecture. This blog explores how scalable AI design, cloud and edge integration, and proven principles turn experiments into enterprise-ready systems, driving faster deployment, cost efficiency, and reliable performance across business units.
The post From Pilots to Production: Building AI Architectures That Scale first appeared on TestingXperts.
I see that it is standard to initialize and close the driver in Cucumber in Hooks class using @Before and @After hooks. However, what if you use Cucumber with Page Object model? Such design pattern also initializes drivers. For that you use the Base class, which all Page classes extend
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
CVE ID : CVE-2025-6625
Published : Aug. 18, 2025, 7:15 a.m. | 18 hours, 47 minutes ago
Description : CWE-20: Improper Input Validation vulnerability exists that could cause a Denial Of Service when specific
crafted FTP command is sent to the device.
Severity: 8.7 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…