Developing next-gen AI agents, exploring new modalities, and pioneering foundational learning Source: Read MoreÂ
Development
Introducing a new AI model developed by Google DeepMind and Isomorphic Labs. Source: Read MoreÂ
Announcing our novel watermarking method for AI-generated text and video, and how we’re bringing SynthID to key Google products Source:…
We’re introducing Veo, our most capable model for generating high-definition video, and Imagen 3, our highest quality text-to-image model. We’re…
We’re introducing a series of updates across the Gemini family of models, including the new 1.5 Flash, our lightweight model…
Our approach to analyzing and mitigating future risks posed by advanced AI models Source: Read MoreÂ
How summits in Seoul, France and beyond can galvanize international cooperation on frontier AI safety Source: Read MoreÂ
Video-to-audio research uses video pixels and text prompts to generate rich soundtracks Source: Read MoreÂ
Exploring AGI, the challenges of scaling and the future of multimodal generative AI Source: Read MoreÂ
Breakthrough models AlphaProof and AlphaGeometry 2 solve advanced reasoning problems in mathematics Source: Read MoreÂ
Announcing a comprehensive, open suite of sparse autoencoders for language model interpretability. Source: Read MoreÂ
New research analyzes the misuse of multimodal generative AI today, in order to help build safer and more responsible technologies.…
Using deep learning to solve fundamental problems in computational quantum chemistry and explore how matter interacts with light Source: Read…
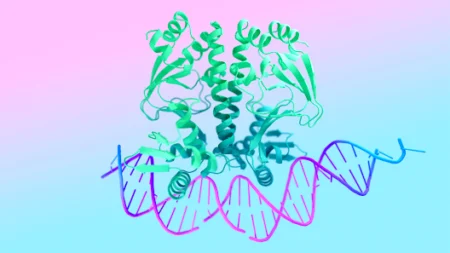
New AI system designs proteins that successfully bind to target molecules, with potential for advancing drug design, disease understanding and…
Two new AI systems, ALOHA Unleashed and DemoStart, help robots learn to perform complex tasks that require dexterous movement Source:…
New video generation technology in YouTube Shorts will help millions of people realize their creative vision Source: Read MoreÂ
We’re releasing two updated production-ready Gemini models Source: Read MoreÂ
Our AI method has accelerated and optimized chip design, and its superhuman chip layouts are used in hardware around the…
The award recognizes their work developing AlphaFold, a groundbreaking AI system that predicts the 3D structure of proteins from their…
Our latest AI music technologies are now available in MusicFX DJ, Music AI Sandbox and YouTube Shorts Source: Read MoreÂ