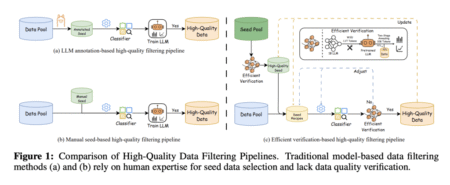
The data quality used in pretraining LLMs has become increasingly critical to their success. To build information-rich corpora, researchers have…
Development
In this tutorial, we demonstrate how to construct an automated Knowledge Graph (KG) pipeline using LangGraph and NetworkX. The pipeline…
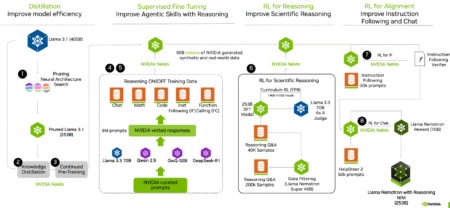
Today, MarkTechPost had the pleasure of interviewing Joey Conway from NVIDIA to discuss their exciting work on open-source large language…
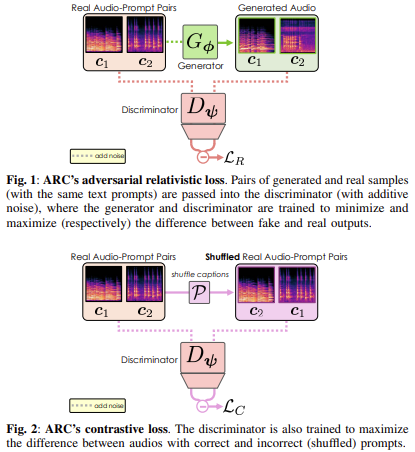
Text-to-audio generation has emerged as a transformative approach for synthesizing sound directly from textual prompts, offering practical use in music…
Hugging Face has released a free/open-source course on the Model Context Protocol (MCP), an open approach developed by Anthropic to…
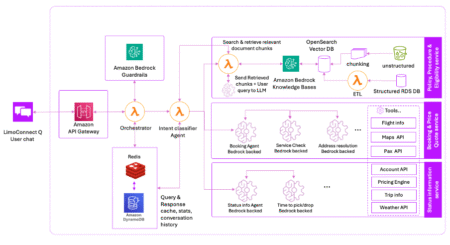
Vxceed delivers SaaS solutions across industries such as consumer packaged goods (CPG), transportation, and logistics. Its modular environments include Lighthouse…
This post is co-authored by Jay Kshirsagar and Ronald Quan from Qualtrics. The content and opinions in this post are…
This post is co-written with Ken Tsui, Edward Tsoi and Mickey Yip from Apoidea Group. The banking industry has long…
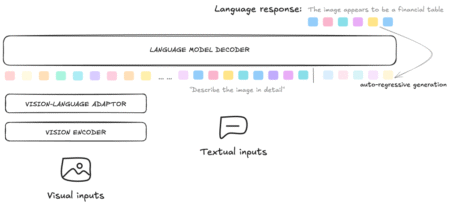
VLMs have become central to building general-purpose AI systems capable of understanding and interacting in digital and real-world settings. By…
CVE ID : CVE-2025-47785
Published : May 15, 2025, 8:16 p.m. | 3 hours, 6 minutes ago
Description : Emlog is an open source website building system. In versions up to and including 2.5.9, SQL injection occurs because the $origContent parameter in admin/article_save.php is not strictly filtered. Since admin/article_save.php can be accessed by ordinary registered users, this will cause SQL injection to occur when the registered site is enabled, resulting in the injection of the admin account and password, which is then exploited by the backend remote code execution. As of time of publication, it is unknown whether a fix exists.
Severity: 8.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47928
Published : May 15, 2025, 8:16 p.m. | 4 hours, 41 minutes ago
Description : Spotipy is a Python library for the Spotify Web API. As of commit 4f5759dbfb4506c7b6280572a4db1aabc1ac778d, using `pull_request_target` on `.github/workflows/integration_tests.yml` followed by the checking out the head.sha of a forked PR can be exploited by attackers, since untrusted code can be executed having full access to secrets (from the base repo). By exploiting the vulnerability is possible to exfiltrate `GITHUB_TOKEN` and secrets `SPOTIPY_CLIENT_ID`, `SPOTIPY_CLIENT_SECRET`. In particular `GITHUB_TOKEN` which can be used to completely overtake the repo since the token has content write privileges. The `pull_request_target` in GitHub Actions is a major security concern—especially in public repositories—because it executes untrusted code from a PR, but with the context of the base repository, including access to its secrets. Commit 9dfb7177b8d7bb98a5a6014f8e6436812a47576f reverted the change that caused the issue.
Severity: 9.1 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4715
Published : May 15, 2025, 8:16 p.m. | 4 hours, 41 minutes ago
Description : A vulnerability was found in Campcodes Sales and Inventory System 1.0. It has been declared as critical. Affected by this vulnerability is an unknown functionality of the file /pages/view_application.php. The manipulation of the argument cid leads to sql injection. The attack can be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4716
Published : May 15, 2025, 8:16 p.m. | 4 hours, 41 minutes ago
Description : A vulnerability was found in Campcodes Sales and Inventory System 1.0. It has been rated as critical. Affected by this issue is some unknown functionality of the file /pages/credit_transaction_add.php. The manipulation of the argument prod_name leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4717
Published : May 15, 2025, 8:16 p.m. | 4 hours, 41 minutes ago
Description : A vulnerability, which was classified as critical, was found in PHPGurukul Company Visitor Management System 2.0. Affected is an unknown function of the file /visitors-form.php. The manipulation of the argument fullname leads to sql injection. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-1138
Published : May 15, 2025, 9:15 p.m. | 3 hours, 42 minutes ago
Description : IBM InfoSphere Information Server 11.7 could disclose sensitive information to an authenticated user that could aid in further attacks against the system through a directory listing.
Severity: 4.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47929
Published : May 15, 2025, 9:15 p.m. | 3 hours, 42 minutes ago
Description : DumbDrop, a file upload application that provides an interface for dragging and dropping files, has a DOM cross-site scripting vulnerability in the upload functionality prior to commit db27b25372eb9071e63583d8faed2111a2b79f1b. A user could be tricked into uploading a file with a malicious payload. Commit db27b25372eb9071e63583d8faed2111a2b79f1b fixes the vulnerability.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4719
Published : May 15, 2025, 9:15 p.m. | 3 hours, 42 minutes ago
Description : A vulnerability was found in Campcodes Sales and Inventory System 1.0 and classified as critical. Affected by this issue is some unknown functionality of the file /pages/cash_transaction.php. The manipulation of the argument cid leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4720
Published : May 15, 2025, 9:15 p.m. | 3 hours, 42 minutes ago
Description : A vulnerability was found in SourceCodester Student Result Management System 1.0. It has been declared as critical. This vulnerability affects unknown code of the file academic/core/drop_student.php. The manipulation of the argument img leads to path traversal. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 5.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4721
Published : May 15, 2025, 9:15 p.m. | 3 hours, 42 minutes ago
Description : A vulnerability was found in itsourcecode Placement Management System 1.0. It has been rated as critical. This issue affects some unknown processing of the file /drive.php. The manipulation of the argument ID leads to sql injection. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4718
Published : May 15, 2025, 9:15 p.m. | 3 hours, 42 minutes ago
Description : A vulnerability has been found in Campcodes Sales and Inventory System 1.0 and classified as critical. Affected by this vulnerability is an unknown functionality of the file /pages/customer_add.php. The manipulation of the argument last leads to sql injection. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. Other parameters might be affected as well.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…