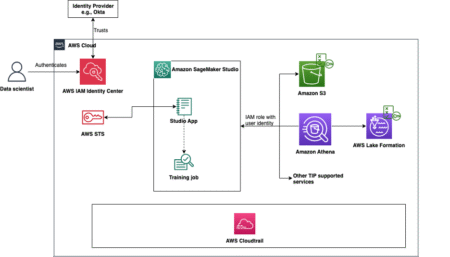
AWS supports trusted identity propagation, a feature that allows AWS services to securely propagate a user’s identity across service boundaries.…
Development
Qwen3 is the cutting-edge series of large language models developed by Alibaba Cloud’s Qwen team. The LLM is known for…
The ability to track what happens with API requests is an important aspect of monitoring, tracing and debugging back-end applications.…
If you are a web developer who doesn’t know about App Development (like me!), then this article is for you.…
High performance and privacy are at the heart of most successful software systems. No one wants to use a software…
Tailwind CSS has revolutionized modern front-end development by offering a utility-first approach. It’s fast, flexible, and makes styling a breeze.…
What is the Content SDK? If you’re familiar with Sitecore’s JSS SDK and have been building sites using it, you…
Success at Perficient is powered by our people who shatter boundaries and make the impossible happen. Our global culture is…
Can you tell the difference between legitimate marketing and deepfake scam ads? It’s not always as easy as you may…
The maintainers of the Python Package Index (PyPI) repository have announced that the package manager now checks for expired domains…
After two decades of developing increasingly mature security architectures, organizations are running up against a hard truth: tools and technologies…
The U.K. government has apparently abandoned its plans to force Apple to weaken encryption protections and include a backdoor that…
TPG Telecom confirms that a cyber incident affecting its iiNet subsidiary exposed the personal data of approximately 280,000 customers, marking…
A new exploit combining two critical, now-patched security flaws in SAP NetWeaver has emerged in the wild, putting organizations at…
In episode 64 of The AI Fix, AI discovers new physics, a robot crab looks for love on the beaches…
The Cyber Express, in collaboration with Suraksha Catalyst, has kicked off the Black Hat USA 2025 CISO Series Podcast with…
Financial institutions like trading and brokerage firms are the target of a new campaign that delivers a previously unreported remote…
A hack of the Netherlands’ Public Prosecution Service has had an unusual side effect – causing some speed cameras to…
Threat actors are exploiting a nearly two-year-old security flaw in Apache ActiveMQ to gain persistent access to cloud Linux systems…
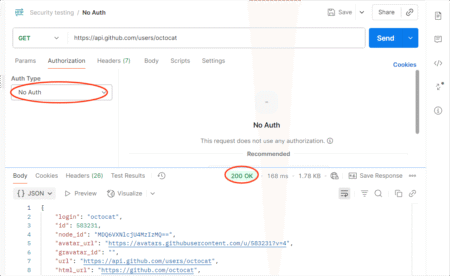
APIs (Application Programming Interfaces) have become the lifeblood of digital transformation. From mobile banking apps to enterprise SaaS platforms, APIs power the seamless flow of data between applications, services, and devices. However, with this power comes an equally significant risk: security vulnerabilities. A single exposed API can lead to massive data leaks, unauthorized access, and
The post Postman API Security Testing: A Complete Guide appeared first on Codoid.