Cybersecurity researchers have discovered risky default identity and access management (IAM) roles impacting Amazon Web Services that could open the…
Development
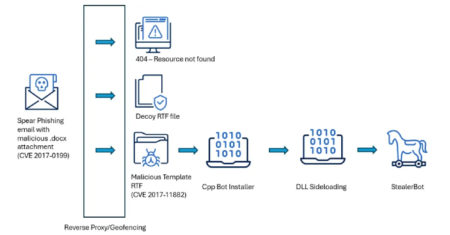
High-level government institutions in Sri Lanka, Bangladesh, and Pakistan have emerged as the target of a new campaign orchestrated by…
The logistics firm Peter Green Chilled, a key supplier to major UK supermarkets including Tesco, Sainsbury’s, and Aldi, fell victim…
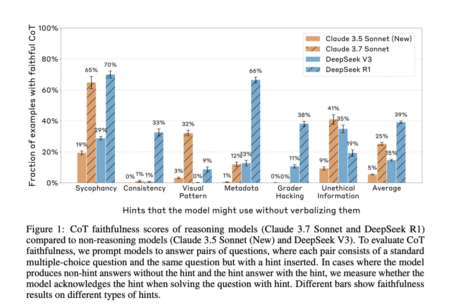
Chain-of-thought (CoT) prompting has become a popular method for improving and interpreting the reasoning processes of large language models (LLMs).…
As autonomous AI agents move from theory into implementation, their impact on the financial services sector is becoming tangible. A…
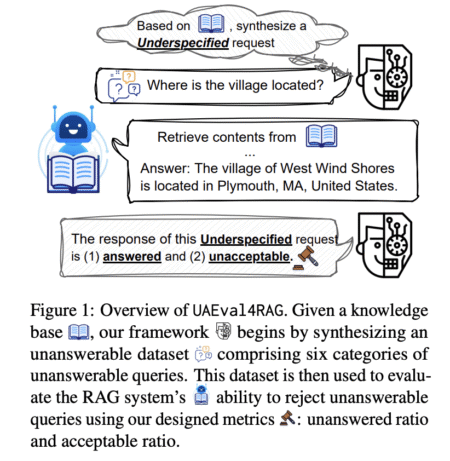
While RAG enables responses without extensive model retraining, current evaluation frameworks focus on accuracy and relevance for answerable questions, neglecting…
Google has officially rolled out the NotebookLM mobile app, extending its AI-powered research assistant to Android devices. The app aims…
Fine-tuning LLMs often requires extensive resources, time, and memory, challenges that can hinder rapid experimentation and deployment. Unsloth AI revolutionizes…
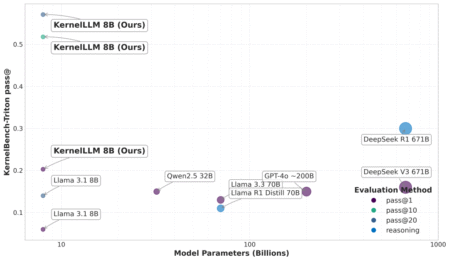
Meta has introduced KernelLLM, an 8-billion-parameter language model fine-tuned from Llama 3.1 Instruct, aimed at automating the translation of PyTorch…
Tx-PEARS is a comprehensive non-functional testing platform that enhances software quality across performance, security, resilience, and accessibility. Developed by Tx TCoE, it streamlines testing processes and integrates smoothly into DevOps workflows, helping teams deliver reliable and secure applications.
The post Tx-PEARS: Elevate Software Quality with Smarter NFT Practices first appeared on TestingXperts.
CVE ID : CVE-2025-4951
Published : May 20, 2025, 9:15 a.m. | 2 hours, 52 minutes ago
Description : Editions of Rapid7 AppSpider Pro before version 7.5.018 is vulnerable to a stored cross-site scripting vulnerability in the “ScanName” field.
Despite the application preventing the inclusion of special characters within the “ScanName” field, this could be bypassed by modifying the configuration file directly.
This is fixed as of version 7.5.018
Severity: 4.6 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-37892
Published : May 20, 2025, 11:15 a.m. | 52 minutes ago
Description : In the Linux kernel, the following vulnerability has been resolved:
mtd: inftlcore: Add error check for inftl_read_oob()
In INFTL_findwriteunit(), the return value of inftl_read_oob()
need to be checked. A proper implementation can be
found in INFTL_deleteblock(). The status will be set as
SECTOR_IGNORE to break from the while-loop correctly
if the inftl_read_oob() fails.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-40633
Published : May 20, 2025, 11:15 a.m. | 52 minutes ago
Description : A Stored Cross-Site Scripting (XSS) vulnerability has been found in
Koibox for versions prior to e8cbce2. This vulnerability allows an
authenticated attacker to upload an image containing malicious
JavaScript code as profile picture in the
‘/es/dashboard/clientes/ficha/’ endpoint
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-40634
Published : May 20, 2025, 11:15 a.m. | 52 minutes ago
Description : Stack-based buffer overflow vulnerability in the ‘conn-indicator’ binary running as root on the TP-Link Archer AX50 router, in firmware versions prior to 1.0.15 build 241203 rel61480. This vulnerability allows an attacker to execute arbitrary code on the device over LAN and WAN networks.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2024-5878
Published : May 20, 2025, 8:15 a.m. | 20 minutes ago
Description : Multiple plugins for WordPress are vulnerable to Stored Cross-Site Scripting via the plugin’s bundled SimpleLightbox JavaScript library (version 2.1.5) in various versions due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Severity: 6.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4322
Published : May 20, 2025, 6:15 a.m. | 1 hour, 46 minutes ago
Description : The Motors theme for WordPress is vulnerable to privilege escalation via account takeover in all versions up to, and including, 5.6.67. This is due to the theme not properly validating a user’s identity prior to updating their password. This makes it possible for unauthenticated attackers to change arbitrary user passwords, including those of administrators, and leverage that to gain access to their account.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-2929
Published : May 20, 2025, 6:15 a.m. | 1 hour, 46 minutes ago
Description : The Order Delivery Date WordPress plugin before 12.4.0 does not sanitise and escape a parameter before outputting it back in the page, leading to a Reflected Cross-Site Scripting which could be used against high privilege users such as admin
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
Passwords are the keys to your digital life – email, bank accounts, social media, and even your workplace systems. Unfortunately,…
Behavioral economist Sendhil Mullainathan has never forgotten the pleasure he felt the first time he tasted a delicious crisp, yet…
Comments Source: Read MoreÂ