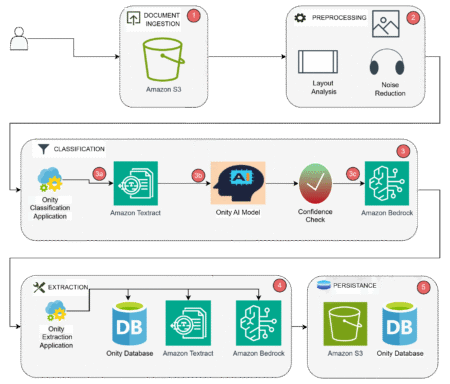
In the mortgage servicing industry, efficient document processing can mean the difference between business growth and missed opportunities. This post…
Development
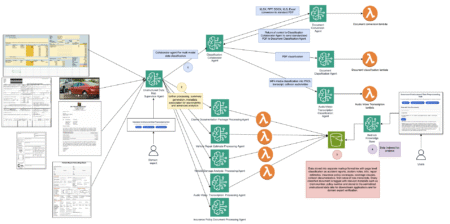
Enterprises—especially in the insurance industry—face increasing challenges in processing vast amounts of unstructured data from diverse formats, including PDFs, spreadsheets,…
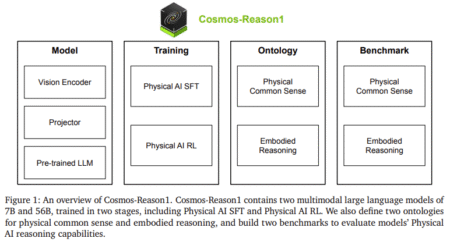
AI has advanced in language processing, mathematics, and code generation, but extending these capabilities to physical environments remains challenging. Physical…
At Google I/O 2025, Google introduced MedGemma, an open suite of models designed for multimodal medical text and image comprehension.…
CVE ID : CVE-2025-44898
Published : May 20, 2025, 9:15 p.m. | 2 hours, 18 minutes ago
Description : FW-WGS-804HPT v1.305b241111 was discovered to contain a stack overflow via the theauthName parameter in the web_aaa_loginAuthlistEdit function.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4998
Published : May 20, 2025, 9:15 p.m. | 2 hours, 18 minutes ago
Description : A vulnerability has been found in H3C Magic R200G up to 100R002 and classified as problematic. Affected by this vulnerability is the function Edit_BasicSSID/Edit_BasicSSID_5G/SetAPWifiorLedInfoById/SetMobileAPInfoById/Asp_SetTimingtimeWifiAndLed/AddMacList/EditMacList/AddWlanMacList/EditWlanMacList of the file /goform/aspForm of the component HTTP POST Request Handler. The manipulation of the argument param leads to denial of service. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 6.5 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44880
Published : May 20, 2025, 9:15 p.m. | 2 hours, 18 minutes ago
Description : A command injection vulnerability in the component /cgi-bin/adm.cgi of Wavlink WL-WN579A3 v1.0 allows attackers to execute arbitrary commands via a crafted input.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44897
Published : May 20, 2025, 9:15 p.m. | 2 hours, 18 minutes ago
Description : FW-WGS-804HPT v1.305b241111 was discovered to contain a stack overflow via the bytftp_srvip parameter in the web_tool_upgradeManager_post function.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44894
Published : May 20, 2025, 9:15 p.m. | 2 hours, 18 minutes ago
Description : FW-WGS-804HPT v1.305b241111 was discovered to contain a stack overflow via the radDftParamKey parameter in the web_radiusSrv_dftParam_post function.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44896
Published : May 20, 2025, 9:15 p.m. | 2 hours, 18 minutes ago
Description : FW-WGS-804HPT v1.305b241111 was discovered to contain a stack overflow via the bindEditMACName parameter in the web_acl_bindEdit_post function.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44882
Published : May 20, 2025, 9:15 p.m. | 2 hours, 18 minutes ago
Description : A command injection vulnerability in the component /cgi-bin/firewall.cgi of Wavlink WL-WN579A3 v1.0 allows attackers to execute arbitrary commands via a crafted input.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44891
Published : May 20, 2025, 9:15 p.m. | 2 hours, 18 minutes ago
Description : FW-WGS-804HPT v1.305b241111 was discovered to contain a stack overflow via the host_ip parameter in the web_snmp_v3host_add_post function.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44883
Published : May 20, 2025, 9:15 p.m. | 2 hours, 18 minutes ago
Description : FW-WGS-804HPT v1.305b241111 was discovered to contain a stack overflow via the tacIp parameter in the web_tacplus_serverEdit_post function.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5000
Published : May 20, 2025, 9:15 p.m. | 2 hours, 18 minutes ago
Description : A vulnerability was found in Linksys FGW3000-AH and FGW3000-HK up to 1.0.17.000000. It has been classified as critical. This affects the function control_panel_sw of the file /cgi-bin/sysconf.cgi of the component HTTP POST Request Handler. The manipulation of the argument filename leads to command injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4999
Published : May 20, 2025, 9:15 p.m. | 2 hours, 18 minutes ago
Description : A vulnerability was found in Linksys FGW3000-AH and FGW3000-HK up to 1.0.17.000000 and classified as critical. Affected by this issue is the function sub_4153FC of the file /cgi-bin/sysconf.cgi of the component HTTP POST Request Handler. The manipulation of the argument supplicant_rnd_id_en leads to command injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5001
Published : May 20, 2025, 10:15 p.m. | 1 hour, 18 minutes ago
Description : A vulnerability was found in GNU PSPP 82fb509fb2fedd33e7ac0c46ca99e108bb3bdffb. It has been declared as problematic. This vulnerability affects the function calloc of the file pspp-convert.c. The manipulation of the argument -l leads to integer overflow. Local access is required to approach this attack. The exploit has been disclosed to the public and may be used.
Severity: 3.3 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5002
Published : May 20, 2025, 10:15 p.m. | 1 hour, 18 minutes ago
Description : A vulnerability, which was classified as critical, was found in SourceCodester Client Database Management System 1.0. This affects an unknown part of the file /user_proposal_update_order.php. The manipulation of the argument order_id leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5003
Published : May 20, 2025, 10:15 p.m. | 1 hour, 18 minutes ago
Description : A vulnerability has been found in projectworlds Online Time Table Generator 1.0 and classified as critical. This vulnerability affects unknown code of the file /semester_ajax.php. The manipulation of the argument ID leads to sql injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4436
Published : May 20, 2025, 11:15 p.m. | 18 minutes ago
Description : Rejected reason: This CVE ID has been rejected or withdrawn by its CVE Numbering Authority.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5007
Published : May 20, 2025, 11:15 p.m. | 18 minutes ago
Description : A vulnerability was found in Part-DB up to 1.17.0. It has been declared as problematic. Affected by this vulnerability is the function handleUpload of the file src/Services/Attachments/AttachmentSubmitHandler.php of the component Profile Picture Feature. The manipulation of the argument attachment leads to cross site scripting. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. Upgrading to version 1.17.1 is able to address this issue. The identifier of the patch is 2c4f44e808500db19c391159b30cb6142896d415. It is recommended to upgrade the affected component.
Severity: 3.5 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…