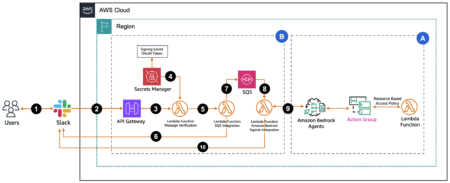
Russian cyber threat actors have been attributed to a state-sponsored campaign targeting Western logistics entities and technology companies since 2022.…
Development
In 2025, agentic AI is transforming the insurance industry, enabling autonomous systems to perceive, reason, and act independently to achieve…
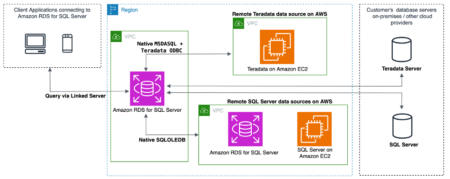
Amazon Relational Database Service (Amazon RDS) for SQL Server now enables you to use Teradata databases as external data sources…
Training manipulation policies for humanoid robots with diverse data enhances their robustness and generalization across tasks and platforms. However, learning…
We consider indoor 3D object detection with respect to a single RGB(-D) frame acquired from a commodity handheld device. We…
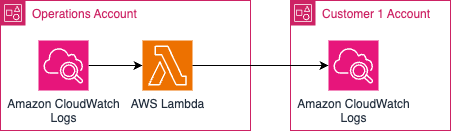
Data privacy is a critical issue for software companies that provide services in the data management space. If they want…
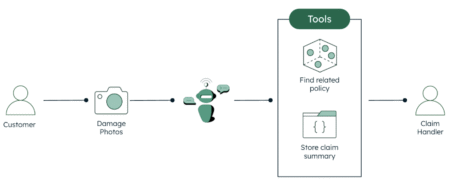
As companies increasingly adopt generative AI applications, AI agents capable of delivering tangible business value have emerged as a crucial…
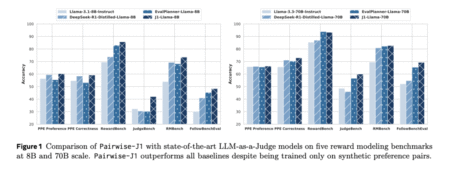
Large language models are now being used for evaluation and judgment tasks, extending beyond their traditional role of text generation.…
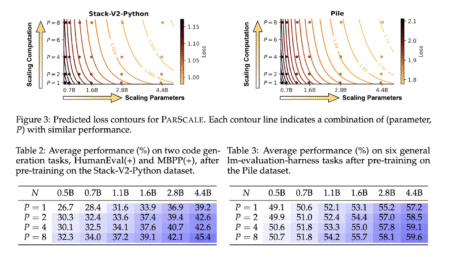
Over time, the pursuit of better performance of language models has pushed researchers to scale them up, which typically involves…
Marktechpost AI Media has unveiled its most comprehensive publication—The Agentic AI and AI Agents Report for 2025—delivering a technically rigorous…
In this tutorial, we provide a practical guide for implementing LangGraph, a streamlined, graph-based AI orchestration framework, integrated seamlessly with…
CVE ID : CVE-2025-27997
Published : May 21, 2025, 4:15 p.m. | 6 hours, 36 minutes ago
Description : An issue in Blizzard Battle.net v2.40.0.15267 allows attackers to escalate privileges via placing a crafted shell script or executable into the C:ProgramData directory.
Severity: 8.4 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-27998
Published : May 21, 2025, 4:15 p.m. | 6 hours, 36 minutes ago
Description : An issue in Valvesoftware Steam Client Steam Client 1738026274 allows attackers to escalate privileges via a crafted executable or DLL.
Severity: 8.4 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44040
Published : May 21, 2025, 9:16 p.m. | 1 hour, 35 minutes ago
Description : An issue in OrangeHRM v.5.7 allows an attacker to escalate privileges via the UserService.php and the checkFOrOldHash function
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-45753
Published : May 21, 2025, 9:16 p.m. | 1 hour, 35 minutes ago
Description : A vulnerability in Vtiger CRM Open Source Edition v8.3.0 allows an attacker with admin privileges to execute arbitrary PHP code by exploiting the ZIP import functionality in the Module Import feature.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5052
Published : May 21, 2025, 9:16 p.m. | 1 hour, 35 minutes ago
Description : A vulnerability classified as critical was found in FreeFloat FTP Server 1.0. Affected by this vulnerability is an unknown functionality of the component LS Command Handler. The manipulation leads to buffer overflow. The attack can be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5053
Published : May 21, 2025, 9:16 p.m. | 1 hour, 35 minutes ago
Description : A vulnerability, which was classified as critical, has been found in FreeFloat FTP Server 1.0. Affected by this issue is some unknown functionality of the component MDIR Command Handler. The manipulation leads to buffer overflow. The attack may be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-34026
Published : May 21, 2025, 10:15 p.m. | 35 minutes ago
Description : The Versa Concerto SD-WAN orchestration platform is vulnerable to an authentication bypass in the Traefik reverse proxy configuration, allowing at attacker to access administrative endpoints. The internal Actuator endpoint can be leveraged for access to heap dumps and trace logs.This issue is known to affect Concerto from 12.1.2 through 12.2.0. Additional versions may be vulnerable.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-34027
Published : May 21, 2025, 10:15 p.m. | 35 minutes ago
Description : The Versa Concerto SD-WAN orchestration platform is vulnerable to an authentication bypass in the Traefik reverse proxy configuration, allowing at attacker to access administrative endpoints. The Spack upload endpoint can be leveraged for a Time-of-Check to Time-of-Use (TOCTOU) write in combination with a race condition to achieve remote code execution via path loading manipulation, allowing an unauthenticated actor to achieve remote code execution (RCE).This issue is known to affect Concerto from 12.1.2 through 12.2.0. Additional versions may be vulnerable.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47942
Published : May 21, 2025, 10:15 p.m. | 35 minutes ago
Description : The Open edX Platform is a learning management platform. Prior to commit 6740e75c0fdc7ba095baf88e9f5e4f3e15cfd8ba, edxapp has no built-in protection against downloading the python_lib.zip asset from courses, which is a concern since it often contains custom grading code or answers to course problems. This potentially affects any course using custom Python-graded problem blocks. The openedx/configuration repo has had a patch since 2016 in the form of an nginx rule, but this was only intended as a temporary mitigation. As the configuration repo has been deprecated and we have not been able to locate any similar protection in Tutor, it is likely that most deployments have no protection against python_lib.zip being downloaded. The recommended mitigation, implemented in commit 6740e75c0fdc7ba095baf88e9f5e4f3e15cfd8ba, restricts python_lib.zip downloads to just the course team and site staff/superusers.
Severity: 5.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…