Latest PEAR Releases: Crypt_GPG 1.6.11 Source: Read MoreÂ
Development
Laravel’s existsOr method enables elegant handling of non-existent model queries by executing closures when no results are found. This feature…
Volet is an extensible customer feedback widget for Laravel The post Volet is a Customer Feedback Widget for Laravel appeared…
Five major banking associations have formally petitioned the U.S. Securities and Exchange Commission (SEC) to repeal a rule that mandates…
Cyber threats don’t show up one at a time anymore. They’re layered, planned, and often stay hidden until it’s too…
Are your web privacy controls protecting your users, or just a box-ticking exercise? This CISO’s guide provides a practical roadmap…
Nova Scotia Power has confirmed it was the victim of a ransomware attack, weeks after initially alerting customers to a…
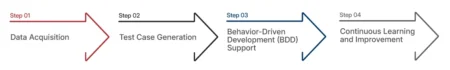
Tx-GPT is an in-house AI Agent by Txlabs that up-scales software testing by converting user stories into detailed, actionable test cases. Designed for QA modernization, it enhances test coverage, automates repetitive tasks, and integrates seamlessly with ALM tools like Azure Test Plans.
The post Tx-GPT: Turning User Stories into QA Action Using AI first appeared on TestingXperts.
CVE ID : CVE-2025-41654
Published : May 26, 2025, 9:15 a.m. | 1 hour, 59 minutes ago
Description : An unauthenticated remote attacker can access information about running processes via the SNMP protocol. The amount of returned data can trigger a reboot by the watchdog.
Severity: 8.2 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-1985
Published : May 26, 2025, 9:15 a.m. | 2 hours, 52 minutes ago
Description : Due to improper neutralization of input during web page generation (XSS) an unauthenticated remote attacker can inject HTML code into the Web-UI in the affected device.
Severity: 6.1 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-41655
Published : May 26, 2025, 9:15 a.m. | 2 hours, 52 minutes ago
Description : An unauthenticated remote attacker can access a URL which causes the device to reboot.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-35003
Published : May 26, 2025, 10:15 a.m. | 1 hour, 52 minutes ago
Description : Improper Restriction of Operations within the Bounds of a Memory Buffer and Stack-based Buffer Overflow vulnerabilities were discovered in Apache NuttX RTOS Bluetooth Stack (HCI and UART components) that may result in system crash, denial of service, or arbitrary code execution, after receiving maliciously crafted packets.
NuttX’s Bluetooth HCI/UART stack users are advised to upgrade to version 12.9.0, which fixes the identified implementation issues.
This issue affects Apache NuttX: from 7.25 before 12.9.0.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-40671
Published : May 26, 2025, 10:15 a.m. | 1 hour, 52 minutes ago
Description : SQL injection vulnerability in AES Multimedia’s Gestnet v1.07. This vulnerability allows an attacker to retrieve, create, update and delete databases via the ‘fk_remoto_central’ parameter on the ‘/webservices/articles.php’ endpoint.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-40672
Published : May 26, 2025, 10:15 a.m. | 1 hour, 52 minutes ago
Description : A Privilege Escalation vulnerability has been found in ProactivaNet v3.24.0.0 from Grupo Espiral MS. This vulnerability allows any user to override the file panLoad.exe that will be executed by SYSTEM user via a programmed task.
This would allow an attacker to obtain administrator permissions to
perform whatever activities he/she wants, shuch as accessing sensitive
information, executing code remotely, and even causing a denial of
service (DoS).
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4053
Published : May 26, 2025, 10:15 a.m. | 1 hour, 52 minutes ago
Description : The data stored in Be-Tech Mifare Classic card is stored in cleartext. An attacker having access to a Be-Tech hotel guest Mifare Classic card can create a master key card that unlocks all the locks in the building.
This issue affects all Be-Tech Mifare Classic card systems. To fix the vulnerability, it is necessary to replace the software, encoder, cards, and PCBs in the locks.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4057
Published : May 26, 2025, 10:15 a.m. | 1 hour, 52 minutes ago
Description : A flaw was found in ActiveMQ Artemis. The password generated by activemq-artemis-operator does not regenerate between separated CR dependencies.
Severity: 5.5 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5177
Published : May 26, 2025, 10:15 a.m. | 1 hour, 52 minutes ago
Description : A vulnerability was found in Realce Tecnologia Queue Ticket Kiosk up to 20250517. It has been rated as problematic. This issue affects some unknown processing of the file /adm/index.php of the component Admin Login Page. The manipulation of the argument Usuário leads to cross site scripting. The attack may be initiated remotely. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 4.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5178
Published : May 26, 2025, 10:15 a.m. | 1 hour, 52 minutes ago
Description : A vulnerability classified as critical has been found in Realce Tecnologia Queue Ticket Kiosk up to 20250517. Affected is an unknown function of the file /adm/ajax.php of the component Image File Handler. The manipulation of the argument files[] leads to unrestricted upload. It is possible to launch the attack remotely. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5179
Published : May 26, 2025, 10:15 a.m. | 1 hour, 52 minutes ago
Description : A vulnerability classified as problematic was found in Realce Tecnologia Queue Ticket Kiosk up to 20250517. Affected by this vulnerability is an unknown functionality of the file /adm/index.php of the component Cadastro de Administrador Page. The manipulation of the argument Name/Usuário leads to cross site scripting. The attack can be launched remotely. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 2.4 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5180
Published : May 26, 2025, 10:15 a.m. | 1 hour, 52 minutes ago
Description : A vulnerability, which was classified as critical, has been found in Wondershare Filmora 14.5.16. Affected by this issue is some unknown functionality in the library CRYPTBASE.dll of the file NFWCHK.exe of the component Installer. The manipulation leads to uncontrolled search path. Attacking locally is a requirement. The complexity of an attack is rather high. The exploitation is known to be difficult. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 7.0 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…