The Russia-aligned threat actor known as TAG-110 has been observed conducting a spear-phishing campaign targeting Tajikistan using macro-enabled Word templates…
Development
The U.S. Federal Bureau of Investigation (FBI) has warned of social engineering attacks mounted by a criminal extortion actor known…
Threat hunters have exposed a novel campaign that makes use of search engine optimization (SEO) poisoning techniques to target employee…
Artificial intelligence is driving a massive shift in enterprise productivity, from GitHub Copilot’s code completions to chatbots that mine internal knowledge…
Microsoft has shed light on a previously undocumented cluster of threat activity originating from a Russia-affiliated threat actor dubbed Void…
In Memory of A. Harry Williams, Past SHARE President SHARE President, Art Gutowski, has shared the news of the sudden…
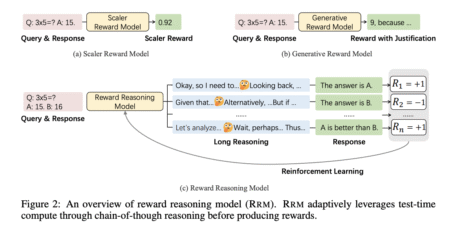
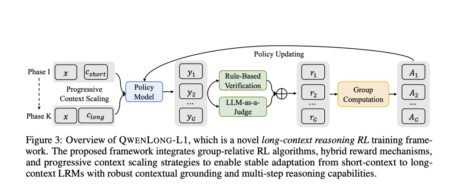
Reinforcement learning (RL) has emerged as a fundamental approach in LLM post-training, utilizing supervision signals from human feedback (RLHF) or…
Chaotic systems, such as fluid dynamics or brain activity, are highly sensitive to initial conditions, making long-term predictions difficult. Even…
While large reasoning models (LRMs) have shown impressive capabilities in short-context reasoning through reinforcement learning (RL), these gains do not…
This blog discusses how voice AI and conversational interfaces transform insurance by enabling faster, more personalized customer interactions. From claim filing to 24/7 support, these tools enhance customer satisfaction and reduce operational burdens.
The post Voice AI and Conversational Interfaces: The Next Frontier in Insurance CX first appeared on TestingXperts.
CVE ID : CVE-2025-47660
Published : May 23, 2025, 1:15 p.m. | 4 days ago
Description : Deserialization of Untrusted Data vulnerability in Codexpert, Inc WC Affiliate allows Object Injection. This issue affects WC Affiliate: from n/a through 2.9.1.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47663
Published : May 23, 2025, 1:15 p.m. | 4 days ago
Description : Unrestricted Upload of File with Dangerous Type vulnerability in mojoomla Hospital Management System allows Upload a Web Shell to a Web Server. This issue affects Hospital Management System: from 47.0(20 through 11.
Severity: 9.9 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47670
Published : May 23, 2025, 1:15 p.m. | 4 days ago
Description : Improper Control of Filename for Include/Require Statement in PHP Program (‘PHP Remote File Inclusion’) vulnerability in miniOrange WordPress Social Login and Register allows PHP Local File Inclusion. This issue affects WordPress Social Login and Register: from n/a through 7.6.10.
Severity: 8.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-41652
Published : May 27, 2025, 9:15 a.m. | 4 hours, 5 minutes ago
Description : The devices are vulnerable to an authentication bypass due to flaws in the authorization mechanism. An unauthenticated remote attacker could exploit this weakness by performing brute-force attacks to guess valid credentials or by using MD5 collision techniques to forge authentication hashes, potentially compromising the device.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-41650
Published : May 27, 2025, 9:15 a.m. | 4 hours, 5 minutes ago
Description : An unauthenticated remote attacker can exploit input validation in cmd services of the devices, allowing them to disrupt system operations and potentially cause a denial-of-service.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-41649
Published : May 27, 2025, 9:15 a.m. | 4 hours, 5 minutes ago
Description : An unauthenticated remote attacker can exploit insufficient input validation to write data beyond the bounds of a buffer, potentially leading to a denial-of-service condition for the devices.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-41651
Published : May 27, 2025, 9:15 a.m. | 4 hours, 5 minutes ago
Description : Due to missing authentication on a critical function of the devices an unauthenticated remote attacker can execute arbitrary commands, potentially enabling unauthorized upload or download of configuration files and leading to full system compromise.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-41653
Published : May 27, 2025, 9:15 a.m. | 4 hours, 5 minutes ago
Description : An unauthenticated remote attacker can exploit a denial-of-service vulnerability in the device’s web server functionality by sending a specially crafted HTTP request with a malicious header, potentially causing the server to crash or become unresponsive.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4412
Published : May 27, 2025, 10:15 a.m. | 3 hours, 5 minutes ago
Description : On macOS systems, by utilizing a Launch Agent and loading the viscosity_openvpn process from the application bundle, it is possible to load a dynamic library with Viscosity’s TCC (Transparency, Consent, and Control) identity. The acquired resource access is limited without entitlements such as access to the camera or microphone. Only user-granted permissions for file resources apply. Access to other resources beyond granted-permissions requires user interaction with a system prompt asking for permission.
This issue was fixed in version 1.11.5 of Viscosity.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5117
Published : May 27, 2025, 12:15 p.m. | 1 hour, 5 minutes ago
Description : The Property plugin for WordPress is vulnerable to Privilege Escalation due to a missing capability check on the use of the property_package_user_role metadata in versions 1.0.5 to 1.0.6. This makes it possible for authenticated attackers, with Author‐level access and above, to elevate their privileges to that of an administrator by creating a package post whose property_package_user_role is set to administrator and then submitting the PayPal registration form.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…