It may seem like an oxymoron when the words “LeetCode” and “meditation” are used together – after all, one thing…
Development
Salesforce Agentforce Empowers Teams With AI-Driven Sales, Service, and Marketing Customer expectations are higher than ever in an always-on, always-connected…
Cybersecurity researchers have taken the wraps off an unusual cyber attack that leveraged malware with corrupted DOS and PE headers,…
In a bold pivot toward modern warfare, the UK Ministry of Defence (MOD) has announced a £1 Billion (approximately $1.35B)…
Fake installers for popular artificial intelligence (AI) tools like OpenAI ChatGPT and InVideo AI are being used as lures to…
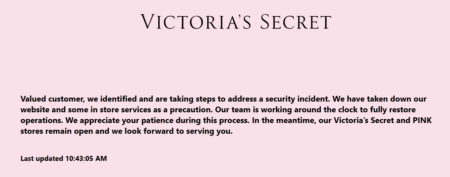
The U.S. website of Victoria’s Secret is down after an unspecified security incident, the latest in a series of cyber…
Join Namik Hrle, VP of Z Data Strategy, IBM, Samantha Buhler, Product Manager, Broadcom, and Chile Hidalgo, Broadcom’s Data Management…
We’re excited to announce that MongoDB Atlas Stream Processing now supports Session Windows! This powerful feature lets you build streaming…
As AI image generation becomes increasingly central to modern business workflows, organizations are seeking practical ways to implement this technology…
AI image generation has emerged as one of the most transformative technologies in recent years, revolutionizing how you create and…
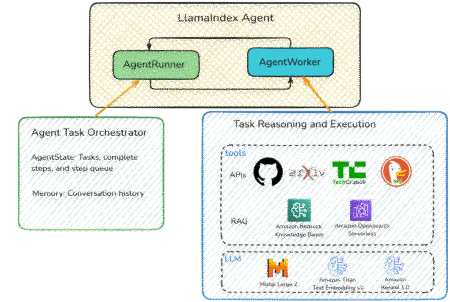
Agentic Retrieval Augmented Generation (RAG) applications represent an advanced approach in AI that integrates foundation models (FMs) with external knowledge…
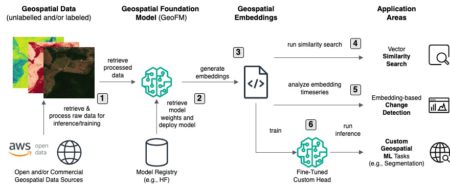
Emerging transformer-based vision models for geospatial data—also called geospatial foundation models (GeoFMs)—offer a new and powerful technology for mapping the…
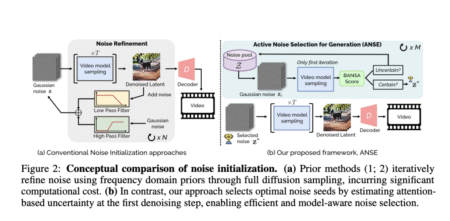
Video generation models have become a core technology for creating dynamic content by transforming text prompts into high-quality video sequences.…
In this tutorial, we will explore how to create a sophisticated Self-Improving AI Agent using Google’s cutting-edge Gemini API. This…
With the increasing integration of speech front-ends and large language models (LLM), there is a need to explore architectures that…
CVE ID : CVE-2020-36846
Published : May 30, 2025, 1:15 a.m. | 27 minutes ago
Description : A buffer overflow, as described in CVE-2020-8927, exists in the embedded Brotli library. Versions of IO::Compress::Brotli prior to 0.007 included a version of the brotli library prior to version 1.0.8, where an attacker controlling the input length of a “one-shot” decompression request to a script can trigger a crash, which happens when copying over chunks of data larger than 2 GiB. It is recommended to update your IO::Compress::Brotli module to 0.007 or later. If one cannot update, we recommend to use the “streaming” API as opposed to the “one-shot” API, and impose chunk size limits.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-31199
Published : May 29, 2025, 10:15 p.m. | 2 hours, 48 minutes ago
Description : A logging issue was addressed with improved data redaction. This issue is fixed in iOS 18.4 and iPadOS 18.4, visionOS 2.4, macOS Sequoia 15.4. An app may be able to access sensitive user data.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-31198
Published : May 29, 2025, 10:15 p.m. | 2 hours, 48 minutes ago
Description : This issue was addressed with improved validation of symlinks. This issue is fixed in macOS Ventura 13.7.5, macOS Sequoia 15.4, macOS Sonoma 14.7.5. A path handling issue was addressed with improved validation.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-30466
Published : May 29, 2025, 10:15 p.m. | 2 hours, 48 minutes ago
Description : This issue was addressed through improved state management. This issue is fixed in Safari 18.4, iOS 18.4 and iPadOS 18.4, visionOS 2.4, macOS Sequoia 15.4. A website may be able to bypass Same Origin Policy.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-31189
Published : May 29, 2025, 10:15 p.m. | 2 hours, 48 minutes ago
Description : A file quarantine bypass was addressed with additional checks. This issue is fixed in macOS Ventura 13.7.5, macOS Sequoia 15.4, macOS Sonoma 14.7.5. An app may be able to break out of its sandbox.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…