A 20-year-old member of the notorious cybercrime gang known as Scattered Spider has been sentenced to ten years in prison…
Development
How often do you hear people talking about issues of legacy systems—especially in critical infrastructure environments? Here’s another example of…
A newly discovered technique, dubbed DOM-based extension clickjacking, has raised serious concerns about the security of browser-based password managers. Despite…
Apple on Wednesday released iPadOS/iOS 18.6.2, as a security update addressing a zero-day vulnerability— tracked as CVE-2025-43300. The company said,…
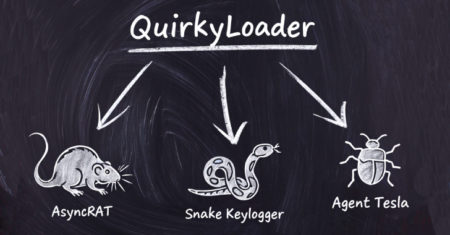
Cybersecurity researchers have disclosed details of a new malware loader called QuirkyLoader that’s being used to deliver via email spam…
As security professionals, it’s easy to get caught up in a race to counter the latest advanced adversary techniques. Yet…
A severe security vulnerability identified as CVE-2025-9074 has been discovered in Docker Desktop, exposing users to critical risks where malicious…
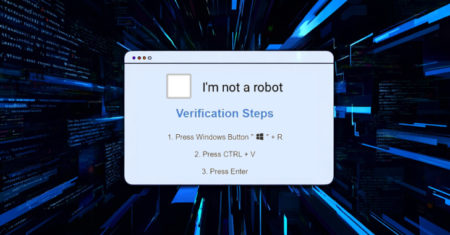
Threat actors have been observed leveraging the deceptive social engineering tactic known as ClickFix to deploy a versatile backdoor codenamed…
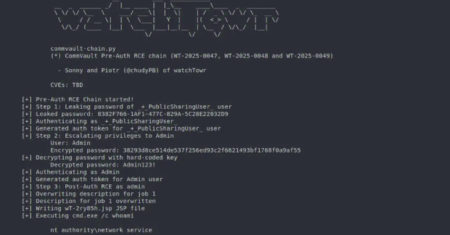
Commvault has released updates to address four security gaps that could be exploited to achieve remote code execution on susceptible…
MongoDB stores data in a Database → Collection → Document structure. Database → Like a container for collections (similar to…
For companies running Node.js applications, hidden inefficiencies can quietly drive up costs, slow down innovation, and increase risk. Source: Read…
CVE ID : CVE-2025-52352
Published : Aug. 21, 2025, 6:15 p.m. | 7 hours, 4 minutes ago
Description : Aikaan IoT management platform v3.25.0325-5-g2e9c59796 provides a configuration to disable user sign-up in distributed deployments by hiding the sign-up option on the login page UI. However, the sign-up API endpoint remains publicly accessible and functional, allowing unauthenticated users to register accounts via APIs even when the feature is disabled. This leads to authentication bypass and unauthorized access to admin portals, violating intended access controls.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7051
Published : Aug. 21, 2025, 6:15 p.m. | 7 hours, 4 minutes ago
Description : On N-central, it is possible for any authenticated user to read, write and modify syslog configuration across customers on an N-central server. This vulnerability is present in all deployments of N-central prior to 2025.2.
Severity: 8.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2010-10015
Published : Aug. 21, 2025, 8:15 p.m. | 5 hours, 4 minutes ago
Description : AOL versions up to and including 9.5 includes an ActiveX control (Phobos.dll) that exposes a method called Import() via the Phobos.Playlist COM object. This method is vulnerable to a stack-based buffer overflow when provided with an excessively long string argument. Exploitation allows remote attackers to execute arbitrary code in the context of the user, but only when the malicious HTML file is opened locally, due to the control not being marked safe for scripting or initialization. AOL remains an active and supported brand offering services like AOL Mail and AOL Desktop Gold, but the legacy AOL 9.5 desktop software—specifically the version containing the vulnerable Phobos.dll ActiveX control—is long discontinued and no longer maintained.
Severity: 8.4 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2010-20109
Published : Aug. 21, 2025, 8:15 p.m. | 5 hours, 4 minutes ago
Description : Barracuda products, confirmed in Spam & Virus Firewall, SSL VPN, and Web Application Firewall versions prior to October 2010, contain a path traversal vulnerability in the view_help.cgi endpoint. The locale parameter fails to properly sanitize user input, allowing attackers to inject traversal sequences and null-byte terminators to access arbitrary files on the underlying system. By exploiting this flaw, unauthenticated remote attackers can retrieve sensitive configuration files such as /mail/snapshot/config.snapshot, potentially exposing credentials, internal settings, and other critical data.
Severity: 8.7 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2010-20111
Published : Aug. 21, 2025, 8:15 p.m. | 5 hours, 4 minutes ago
Description : Digital Music Pad v8.2.3.3.4 contains a stack-based buffer overflow vulnerability in its playlist file parser. When opening a .pls file containing an excessively long string in the File1 field, the application fails to properly validate input length, resulting in corruption of the Structured Exception Handler (SEH) on the stack. This flaw may allow an attacker to control execution flow when the file is opened, potentially leading to arbitrary code execution.
Severity: 8.4 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2010-20112
Published : Aug. 21, 2025, 8:15 p.m. | 5 hours, 4 minutes ago
Description : Amlib’s NetOpacs webquery.dll contains a stack-based buffer overflow vulnerability triggered by improper handling of HTTP GET parameters. Specifically, the application fails to enforce bounds on input supplied to the app parameter, allowing excessive data to overwrite memory structures including the Structured Exception Handler (SEH). Additionally, malformed parameter names followed by an equals sign may result in unintended control flow behavior. This vulnerability is exposed through IIS and affects legacy Windows deployments
Severity: 9.3 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2010-20119
Published : Aug. 21, 2025, 8:15 p.m. | 5 hours, 4 minutes ago
Description : CommuniCrypt Mail versions up to and including 1.16 contains a stack-based buffer overflow vulnerability in its ANSMTP.dll and AOSMTP.dll ActiveX controls, specifically within the AddAttachments() method. This method fails to properly validate the length of input strings, allowing data to exceed the bounds of a fixed-size stack buffer. When invoked with an overly long string, the control can corrupt adjacent memory structures, including exception handlers, leading to potential control flow disruption.
Severity: 8.6 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2010-20121
Published : Aug. 21, 2025, 8:15 p.m. | 5 hours, 4 minutes ago
Description : EasyFTP Server versions up to 1.7.0.11 contain a stack-based buffer overflow vulnerability in the FTP command parser. When processing the CWD (Change Working Directory) command, the server fails to properly validate the length of the input string, allowing attackers to overwrite memory on the stack. This flaw enables remote code execution without authentication, as EasyFTP allows anonymous access by default. The vulnerability was resolved in version 1.7.0.12, after which the product was renamed “UplusFtp.”
Severity: 9.3 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-27721
Published : Aug. 21, 2025, 8:15 p.m. | 5 hours, 4 minutes ago
Description : Unauthorized users can access INFINITT PACS System Manager without proper authorization,
which could lead to unauthorized access to system resources.
Severity: 8.7 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…