Join Perficient at Kscope25 in Grapevine, Texas, from June 15-19, 2025! As a premier educational conference for Oracle technology users,…
Development
Salesforce’s acquisition of Informatica is a big move and a smart one. It brings together the world’s #1 AI CRM…
This Laravel Blade + Apline.js starter kit emphasizes simplicity by offering a lightweight, Blade-only kit. The post A Blade-Only Starter…
The UK’s Ministry of Defence has revealed that it was the target of a sophisticated cyber attack that saw Russia-linked…
A new malware campaign is distributing a novel Rust-based information stealer dubbed EDDIESTEALER using the popular ClickFix social engineering tactic…
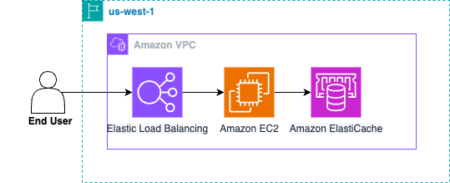
As companies expand globally, they must be able to architect highly available and fault-tolerant systems across multiple AWS Regions. With…
“Managing heat generated by data centers will become progressively more challenging – and, at the same time, necessary.” Chris Frye,…
As diffusion models dominating visual content generation, efforts have been made to adapt these models for multi-view image generation to…
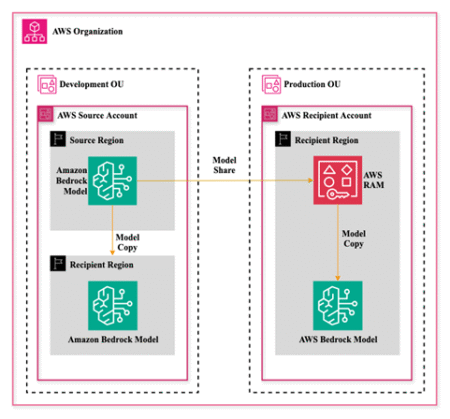
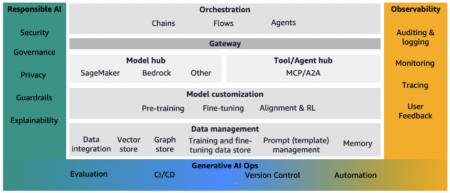
In the landscape of generative AI, organizations are increasingly adopting a structured approach to deploy their AI applications, mirroring traditional…
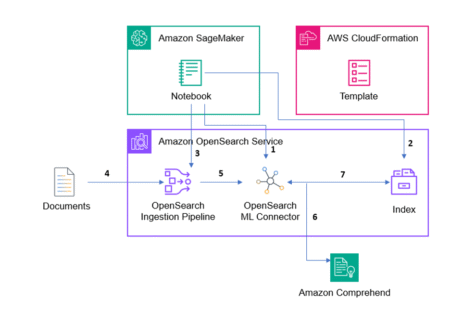
When ingesting data into Amazon OpenSearch, customers often need to augment data before putting it into their indexes. For instance,…
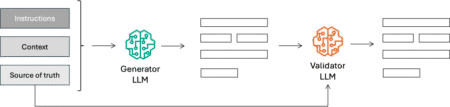
Generative AI applications seem simple—invoke a foundation model (FM) with the right context to generate a response. In reality, it’s…
Generative AI revolutionizes business operations through various applications, including conversational assistants such as Amazon’s Rufus and Amazon Seller Assistant. Additionally,…
ZURU Tech is on a mission to change the way we build, from town houses and hospitals to office towers,…
Amazon SageMaker Projects empower data scientists to self-serve Amazon Web Services (AWS) tooling and infrastructure to organize all entities of the…
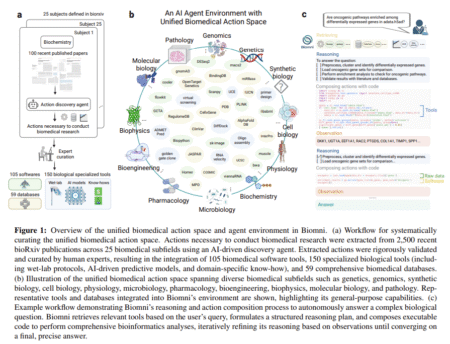
Biomedical research is a rapidly evolving field that seeks to advance human health by uncovering the mechanisms behind diseases, identifying…
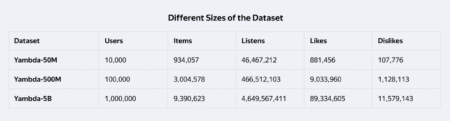
Yandex has recently made a significant contribution to the recommender systems community by releasing Yambda, the world’s largest publicly available…
I’m working with Java and REST Assured to test REST APIs. I was trying the example with JSON schema validation but it throws this error:
java.lang.IllegalArgumentException: Schema to use cannot be null
at io.restassured.module.jsv.JsonSchemaValidator.validateSchemaIsNotNull(JsonSchemaValidator.java:270)
at io.restassured.module.jsv.JsonSchemaValidator.access$300(JsonSchemaValidator.java:75)
at io.restassured.module.jsv.JsonSchemaValidator$JsonSchemaValidatorFactory.create(JsonSchemaValidator.java:281)
at io.restassured.module.jsv.JsonSchemaValidator.matchesJsonSchema(JsonSchemaValidator.java:166)
at io.restassured.module.jsv.JsonSchemaValidator.matchesJsonSchemaInClasspath(JsonSchemaValidator.java:117)
at suites.SchemaFollowupTest.ContractFollowUpTestSuccess(SchemaFollowupTest.java:44)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
My test code is:
given()
.header(“Content-Type”, ContentType.JSON)
//.header(“Authorization”, “Bearer ” + ConfigEnvironments.TOKEN_K8S)
.body(jsonBody)
.when()
.post(ConfigEnvironments.BASE_URL_CLAIMENGINE +”/api/v1/FollowUp”)
.then().log().all()
.statusCode(202)
.and()
.body(matchesJsonSchemaInClasspath(“src/test/resource/followup-schema.json”));
My strucuture folder is here:
[1]: https://i.sstatic.net/K9m2UjGy.png
CVE ID : CVE-2025-5364
Published : May 30, 2025, 10:15 p.m. | 3 hours, 26 minutes ago
Description : A vulnerability was found in Campcodes Online Hospital Management System 1.0 and classified as critical. Affected by this issue is some unknown functionality of the file /doctor/add-patient.php. The manipulation of the argument patname leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2018-25111
Published : May 31, 2025, 1:15 a.m. | 26 minutes ago
Description : django-helpdesk before 1.0.0 allows Sensitive Data Exposure because of os.umask(0) in models.py.
Severity: 5.1 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5365
Published : May 31, 2025, 1:15 a.m. | 26 minutes ago
Description : A vulnerability was found in Campcodes Online Hospital Management System 1.0. It has been classified as critical. This affects an unknown part of the file /admin/patient-search.php. The manipulation of the argument searchdata leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…