We have been hearing about AI in many different ways and technology pioneers have been slowly introducing AI in our…
Development
Something incredible just happened: Filament now runs natively inside an Android app thanks to you. The post Filament Is Now…
A multinational law enforcement operation has resulted in the takedown of an online cybercrime syndicate that offered services to threat…
State-of-the-art models show human-competitive accuracy on AIME, GPQA, MATH-500, and OlympiadBench, solving Olympiad-level problems. Recent multimodal foundation models have advanced…
In this tutorial, we implement the Agent Communication Protocol (ACP) through building a flexible, ACP-compliant messaging system in Python, leveraging…
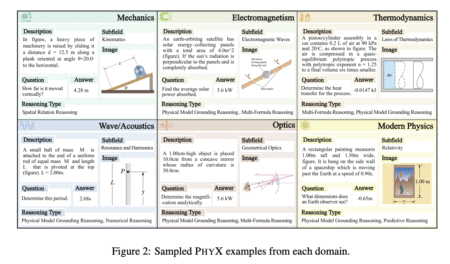
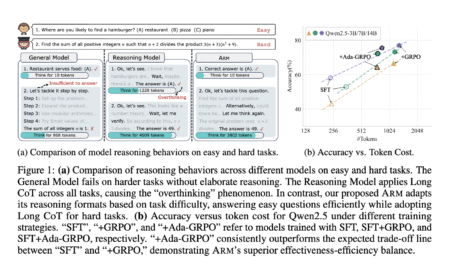
Reasoning tasks are a fundamental aspect of artificial intelligence, encompassing areas like commonsense understanding, mathematical problem-solving, and symbolic reasoning. These…
CVE ID : CVE-2025-5374
Published : May 31, 2025, 10:15 a.m. | 3 hours, 28 minutes ago
Description : A vulnerability was found in PHPGurukul Online Birth Certificate System 2.0 and classified as critical. This issue affects some unknown processing of the file /admin/all-applications.php. The manipulation of the argument del leads to sql injection. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5375
Published : May 31, 2025, 11:15 a.m. | 2 hours, 28 minutes ago
Description : A vulnerability was found in PHPGurukul HPGurukul Online Birth Certificate System 2.0. It has been classified as critical. Affected is an unknown function of the file /admin/registered-users.php. The manipulation of the argument del leads to sql injection. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4691
Published : May 31, 2025, 12:15 p.m. | 1 hour, 28 minutes ago
Description : The Free Booking Plugin for Hotels, Restaurants and Car Rentals – eaSYNC Booking plugin for WordPress is vulnerable to Insecure Direct Object Reference in all versions up to, and including, 1.3.21 via the ‘view_request_details’ due to missing validation on a user controlled key. This makes it possible for unauthenticated attackers to view the details of any booking request. The vulnerability was partially patched in versions 1.3.18 and 1.3.21.
Severity: 5.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4857
Published : May 31, 2025, 12:15 p.m. | 1 hour, 28 minutes ago
Description : The Newsletters plugin for WordPress is vulnerable to Local File Inclusion in all versions up to, and including, 4.9.9.9 via the ‘file’ parameter. This makes it possible for authenticated attackers, with Administrator-level access and above, to include and execute arbitrary files on the server, allowing the execution of any PHP code in those files. This can be used to bypass access controls, obtain sensitive data, or achieve code execution in cases where images and other “safe” file types can be uploaded and included.
Severity: 7.2 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5376
Published : May 31, 2025, 12:15 p.m. | 1 hour, 28 minutes ago
Description : A vulnerability was found in SourceCodester Health Center Patient Record Management System 1.0. It has been declared as critical. Affected by this vulnerability is an unknown functionality of the file /patient.php. The manipulation of the argument itr_no leads to sql injection. The attack can be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5377
Published : May 31, 2025, 1:15 p.m. | 28 minutes ago
Description : A vulnerability was found in Astun Technology iShare Maps 5.4.0. It has been rated as problematic. Affected by this issue is some unknown functionality of the file historic1.asp. The manipulation of the argument Zoom leads to cross site scripting. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 4.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5378
Published : May 31, 2025, 1:15 p.m. | 28 minutes ago
Description : A vulnerability classified as problematic has been found in Astun Technology iShare Maps 5.4.0. This affects an unknown part of the file mycouncil2.aspx. The manipulation of the argument atTxtStreet leads to cross site scripting. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 4.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
Kritieke beveiligingslekken in forumsoftware vBulletin actief misbruikt
Aanvallers maken actief misbruik van twee kritieke kwetsbaarheden in de populaire forumsoftware vBulletin, zo melden het Amerikaanse National Institute of Standards and Technology (NIST), Qualys en KE …
Read more
Published Date:
May 31, 2025 (3 hours, 2 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-48828
CVE-2025-48827
CVE ID : CVE-2025-5370
Published : May 31, 2025, 6:15 a.m. | 3 hours, 27 minutes ago
Description : A vulnerability classified as critical was found in PHPGurukul News Portal 4.1. Affected by this vulnerability is an unknown functionality of the file /admin/forgot-password.php. The manipulation of the argument Username leads to sql injection. The attack can be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4103
Published : May 31, 2025, 7:15 a.m. | 44 minutes ago
Description : The WP-GeoMeta plugin for WordPress is vulnerable to Privilege Escalation due to a missing capability check on the wp_ajax_wpgm_start_geojson_import() function in versions 0.3.4 to 0.3.5. This makes it possible for authenticated attackers, with Subscriber-level access and above, to elevate their privileges to that of an administrator.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4595
Published : May 31, 2025, 7:15 a.m. | 2 hours, 27 minutes ago
Description : The FastSpring plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin’s ‘fastspring/block-fastspringblocks-complete-product-catalog’ block in all versions up to, and including, 3.0.1 due to insufficient input sanitization and output escaping on the ‘color’ attribute. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Severity: 6.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4590
Published : May 31, 2025, 7:15 a.m. | 2 hours, 27 minutes ago
Description : The Daisycon prijsvergelijkers plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin’s ‘daisycon_uitvaart’ shortcode in all versions up to, and including, 4.8.4 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Severity: 6.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4672
Published : May 31, 2025, 7:15 a.m. | 44 minutes ago
Description : The Offsprout Page Builder plugin for WordPress is vulnerable to Privilege Escalation due to improper authorization placed on the permission_callback() function in versions 2.2.1 to 2.15.2. This makes it possible for authenticated attackers, with Contributor-level access and above, to read, create, update or delete any user meta, including flipping their own wp_capabilities to administrator and fully escalate their privileges.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4631
Published : May 31, 2025, 7:15 a.m. | 44 minutes ago
Description : The Profitori plugin for WordPress is vulnerable to Privilege Escalation due to a missing capability check on the stocktend_object endpoint in versions 2.0.6.0 to 2.1.1.3. This makes it possible to trigger the save_object_as_user() function for objects whose ‘_datatype’ is set to ‘users’,. This allows unauthenticated attackers to write arbitrary strings straight into the user’s wp_capabilities meta field, potentially elevating the privileges of an existing user account or a newly created one to that of an administrator.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…