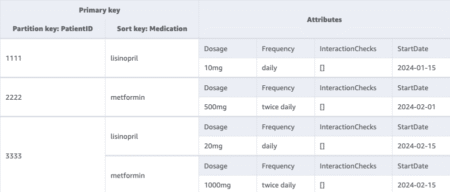
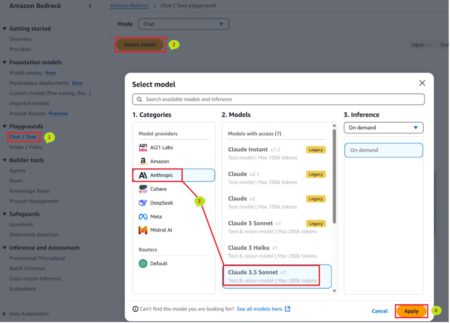
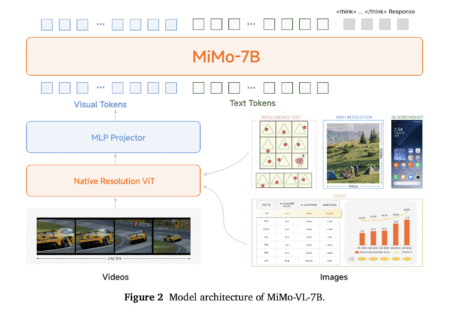
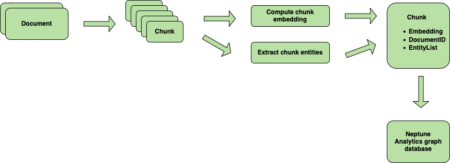
Healthcare providers manage an ever-growing volume of patient data and medication information to help ensure safe, effective treatment. Although traditional…
Development
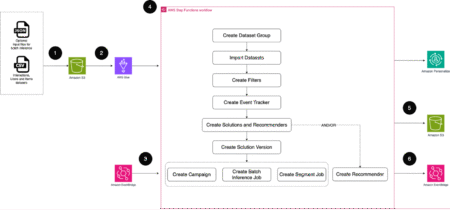
Organizations are increasingly seeking to modernize their database infrastructure by migrating from legacy database engines such as Microsoft SQL Server…
Some features mentioned below have been sunset since this paper was originally written. Visit our docs to learn more. At…
Vision-language models (VLMs) have become foundational components for multimodal AI systems, enabling autonomous agents to understand visual environments, reason over…
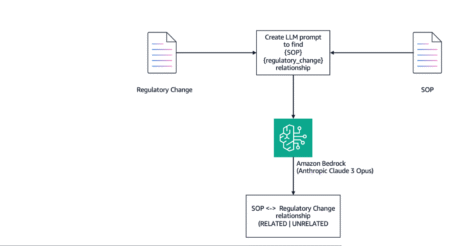
Standard operating procedures (SOPs) are essential documents in the context of regulations and compliance. SOPs outline specific steps for various…
Crafting unique, customized experiences that resonate with customers is a potent strategy for boosting engagement and fostering brand loyalty. However,…
In these days, it is more common to companies adopting AI-first strategy to stay competitive and more efficient. As generative…
In this tutorial, we demonstrate how to leverage ScrapeGraph’s powerful scraping tools in combination with Gemini AI to automate the…
*Equal Contributors Identifying mistakes (i.e., miscues) made while reading aloud is commonly approached post-hoc by comparing automatic speech recognition (ASR)…
⚡ Weekly Recap: APT Intrusions, AI Malware, Zero-Click Exploits, Browser Hijacks and More
Cybersecurity / Hacking News
If this had been a security drill, someone would’ve said it went too far. But it wasn’t a drill—it was real. The access? Everything looked normal. The tools? Easy to find. …
Read more
Published Date:
Jun 02, 2025 (12 hours, 6 minutes ago)
Vulnerabilities has been mentioned in this article.
Exploitation Risk Grows for Critical Cisco Bug
Source: Sergiy Palamarchuk via ShutterstockThe risk of attackers exploiting a recently disclosed maximum severity vulnerability in Cisco’s IOS XE Wireless Controller software has increased significant …
Read more
Published Date:
Jun 02, 2025 (2 hours, 8 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-20188
CVE-2014-2120
CVE ID : CVE-2025-1051
Published : June 2, 2025, 7:15 p.m. | 2 hours, 59 minutes ago
Description : Sonos Era 300 Heap-based Buffer Overflow Remote Code Execution Vulnerability. This vulnerability allows network-adjacent attackers to execute arbitrary code on affected Sonos Era 300 speakers. Authentication is not required to exploit this vulnerability.
The specific flaw exists within the processing of ALAC data. The issue results from the lack of proper validation of the length of user-supplied data prior to copying it to a heap-based buffer. An attacker can leverage this vulnerability to execute code in the context of the anacapa user. Was ZDI-CAN-25865.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-23099
Published : June 2, 2025, 7:15 p.m. | 4 hours, 10 minutes ago
Description : An issue was discovered in Samsung Mobile Processor Exynos 1480 and 2400. The lack of a length check leads to out-of-bounds writes.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-23105
Published : June 2, 2025, 7:15 p.m. | 4 hours, 10 minutes ago
Description : An issue was discovered in Samsung Mobile Processor Exynos 2200, 1480, and 2400. A Use-After-Free in the mobile processor leads to privilege escalation.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-49069
Published : June 2, 2025, 7:15 p.m. | 4 hours, 10 minutes ago
Description : Cross-Site Request Forgery (CSRF) vulnerability in Cimatti Consulting Contact Forms by Cimatti allows Cross Site Request Forgery.This issue affects Contact Forms by Cimatti: from n/a through 1.9.8.
Severity: 4.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48387
Published : June 2, 2025, 8:15 p.m. | 3 hours, 10 minutes ago
Description : tar-fs provides filesystem bindings for tar-stream. Versions prior to 3.0.9, 2.1.3, and 1.16.5 have an issue where an extract can write outside the specified dir with a specific tarball. This has been patched in versions 3.0.9, 2.1.3, and 1.16.5. As a workaround, use the ignore option to ignore non files/directories.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47585
Published : June 2, 2025, 8:15 p.m. | 3 hours, 10 minutes ago
Description : Missing Authorization vulnerability in Mage people team Booking and Rental Manager allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Booking and Rental Manager: from n/a through 2.3.8.
Severity: 6.5 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48996
Published : June 2, 2025, 8:15 p.m. | 3 hours, 10 minutes ago
Description : HAX open-apis provides microservice apis for HAX webcomponents repo that are shared infrastructure calls. An unauthenticated information disclosure vulnerability exists in the Penn State University deployment of the HAX content management system via the `haxPsuUsage` API endpoint, related to a flat present in open-apis versions up to and including 10.0.2. This allows any remote unauthenticated user to retrieve a full list of PSU websites hosted on HAX CMS. When chained with other authorization issues (e.g., HAX-3), this could assist in targeted attacks such as unauthorized content modification or deletion. Commit 06c2e1fbb7131a8fe66aa0600f38dcacae6b7ac7 patches the vulnerability.
Severity: 5.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
Google Fights Back: Appeals Order to Sell Chrome Browser
In response to the U.S. Department of Justice’s directive that Google must divest and sell its Chrome browser business, the company announced its intention to appeal the decision, asserting that the p …
Read more
Published Date:
Jun 02, 2025 (5 hours, 43 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-3619
CVE-2024-10488
CVE-2024-10487
MediaTek Vulnerabilities Let Attackers Escalate Privileges Without User Interaction
Multiple critical security vulnerabilities affecting MediaTek smartphones, tablets, and IoT chipsets could allow attackers to escalate privileges and compromise device security without requiring any u …
Read more
Published Date:
Jun 02, 2025 (3 hours, 57 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-20678
CVE-2025-20677
CVE-2025-20676
CVE-2025-20675
CVE-2025-20674
CVE-2025-20673
CVE-2025-20672