We propose a distillation scaling law that estimates distilled model performance based on a compute budget and its allocation between…
Development
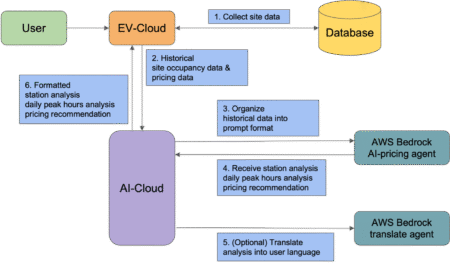
Noodoe is a global leader in EV charging innovation, offering advanced solutions that empower operators to optimize their charging station…
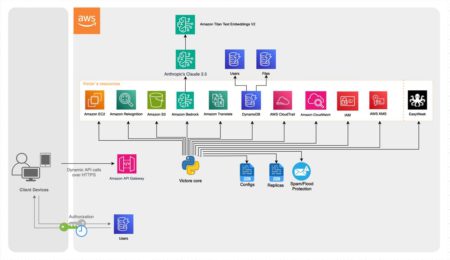
This post is co-written with Taras Tsarenko, Vitalil Bozadzhy, and Vladyslav Horbatenko. As organizations worldwide seek to use AI for…
We’ve witnessed remarkable advances in model capabilities as generative AI companies have invested in developing their offerings. Language models such…
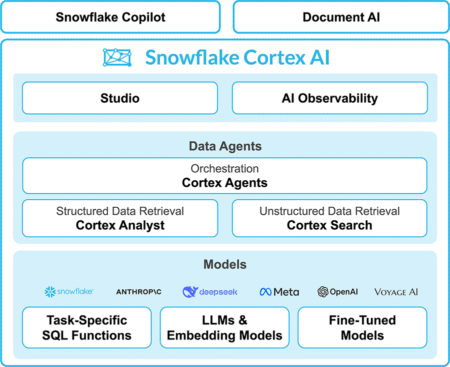
San Francisco, CA – The data cloud landscape is buzzing as Snowflake, a heavyweight in data warehousing and analytics, today…
Recent advances in reasoning-centric large language models (LLMs) have expanded the scope of reinforcement learning (RL) beyond narrow, task-specific applications,…
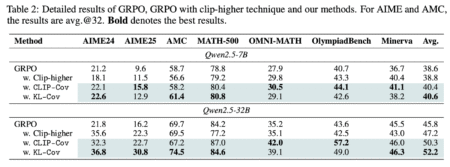
Despite recent progress in robotic control via large-scale vision-language-action (VLA) models, real-world deployment remains constrained by hardware and data requirements.…
OpenAI has announced a set of targeted updates to its AI agent development stack, aimed at expanding platform compatibility, improving…
Cross-lingual transfer is a popular approach to increase the amount of training data for NLP tasks in a low-resource context.…
Google quietly pushes emergency fix for Chrome 0-day as exploit runs wild
Google revealed Monday that it had quietly deployed a configuration change last week to block active exploitation of a Chrome zero-day.
Google Threat Analysis Group (TAG) team members Clement Lecigne …
Read more
Published Date:
Jun 03, 2025 (4 hours, 13 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-5419
CVE-2025-5068
CVE-2025-4664
CVE-2025-2783
Hewlett Packard Enterprise warns of critical StoreOnce auth bypass
Hewlett Packard Enterprise (HPE) has issued a security bulletin to warn about eight vulnerabilities impacting StoreOnce, its disk-based backup and deduplication solution.
Among the flaws fixed this ti …
Read more
Published Date:
Jun 03, 2025 (2 hours, 42 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-37096
CVE-2025-37095
CVE-2025-37094
CVE-2025-37093
CVE-2025-37092
CVE-2025-37091
CVE-2025-37090
CVE-2025-37089
CVE-2025-3794
CVE ID : CVE-2025-23097
Published : June 3, 2025, 8:15 p.m. | 1 hour, 30 minutes ago
Description : An issue was discovered in Samsung Mobile Processor Exynos 1380. The lack of a length check leads to out-of-bounds writes.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-23098
Published : June 3, 2025, 8:15 p.m. | 1 hour, 30 minutes ago
Description : An issue was discovered in Samsung Mobile Processor Exynos 980, 990, 1080, 2100, 1280, 2200, 1380. A Use-After-Free in the mobile processor leads to privilege escalation.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-23100
Published : June 3, 2025, 8:15 p.m. | 1 hour, 30 minutes ago
Description : An issue was discovered in Samsung Mobile Processor Exynos 1280, 2200, 1380, 1480, 2400. The absence of a NULL check leads to a Denial of Service.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-35036
Published : June 3, 2025, 8:15 p.m. | 1 hour, 30 minutes ago
Description : Hibernate Validator before 6.2.0 and 7.0.0, by default and depending how it is used, may interpolate user-supplied input in a constraint violation message with Expression Language. This could allow an attacker to access sensitive information or execute arbitrary Java code. Hibernate Validator as of 6.2.0 and 7.0.0 no longer interpolates custom constraint violation messages with Expression Language and strongly recommends not allowing user-supplied input in constraint violation messages. CVE-2020-5245 and CVE-2025-4428 are examples of related, downstream vulnerabilities involving Expression Language intepolation of user-supplied data.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5523
Published : June 3, 2025, 8:15 p.m. | 1 hour, 30 minutes ago
Description : A vulnerability classified as problematic has been found in enilu web-flash 1.0. This affects the function fileService.upload of the file src/main/java/cn/enilu/flash/api/controller/FileController/upload of the component File Upload. The manipulation of the argument File leads to cross site scripting. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 3.5 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5525
Published : June 3, 2025, 8:15 p.m. | 1 hour, 30 minutes ago
Description : A vulnerability was found in Jrohy trojan up to 2.15.3. It has been declared as critical. This vulnerability affects the function LogChan of the file trojan/util/linux.go. The manipulation of the argument c leads to os command injection. The attack can be initiated remotely. The complexity of an attack is rather high. The exploitation appears to be difficult. The exploit has been disclosed to the public and may be used.
Severity: 5.6 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48951
Published : June 3, 2025, 9:15 p.m. | 30 minutes ago
Description : Auth0-PHP is a PHP SDK for Auth0 Authentication and Management APIs. Versions 8.0.0-BETA3 prior to 8.14.0 contain a vulnerability due to insecure deserialization of cookie data. If exploited, since SDKs process cookie content without prior authentication, a threat actor could send a specially crafted cookie containing malicious serialized data. Applications using the Auth0-PHP SDK are affected, as are applications using the Auth0/symfony, Auth0/laravel-auth0, or Auth0/wordpress SDKs, because those SDKsrely on the Auth0-PHP SDK versions from 8.0.0-BETA3 until 8.14.0. Version 8.14.0 contains a patch for the issue.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-49002
Published : June 3, 2025, 9:15 p.m. | 30 minutes ago
Description : DataEase is an open source business intelligence and data visualization tool. Versions prior to version 2.10.10 have a flaw in the patch for CVE-2025-32966 that allow the patch to be bypassed through case insensitivity because INIT and RUNSCRIPT are prohibited. The vulnerability has been fixed in v2.10.10. No known workarounds are available.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48999
Published : June 3, 2025, 9:15 p.m. | 30 minutes ago
Description : DataEase is an open source business intelligence and data visualization tool. A bypass of CVE-2025-46566’s patch exists in versions prior to 2.10.10. In a malicious payload, `getUrlType()` retrieves `hostName`. Since the judgment statement returns false, it will not enter the if statement and will not be filtered. The payload can be directly concatenated at the replace location to construct a malicious JDBC statement. Version 2.10.10 contains a patch for the issue.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…