AWS makes it much easier to deploy containerized applications, and running Kubernetes in the cloud is a powerful way to…
Development
On this week’s episode of the podcast, freeCodeCamp founder Quincy Larson interviews Emmett Naughton. He worked as hospital janitor for…
This blog explains how to install and configure OpenPlatform as the final step in setting up the Total.js IoT platform,…
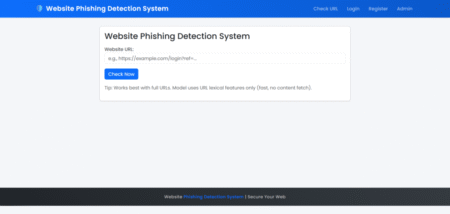
“WEBSITE PHISHING DETECTION SYSTEM” is a web-based application which is aim to address phishing attacks by combining machine learning techniques…
In MongoDB, data is stored in the form of documents (JSON-like objects). These documents are organised within collections, and collections are…
Separating truth from fiction is the first step towards making better parenting decisions. Let’s puncture some of the most common…
How top-tier managed detection and response (MDR) can help organizations stay ahead of increasingly agile and determined adversaries Source: Read…
The Cyber Express, in collaboration with Suraksha Catalyst, is thrilled to announce the launch of Episode 2 of the Black…
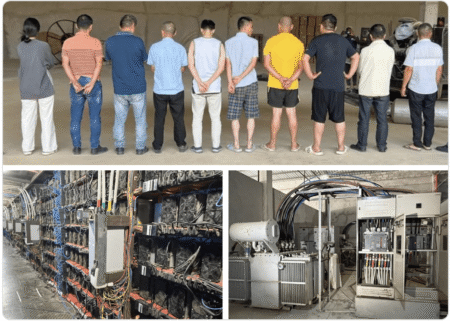
A 55-year-old Chinese national has been sentenced to four years in prison and three years of supervised release for sabotaging…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) have released four new Industrial Control Systems (ICS) advisories. These advisories expose…
A critical security vulnerability, officially tracked as CVE-2025-8592, has been identified in the popular Inspiro WordPress theme. The flaw, affecting…
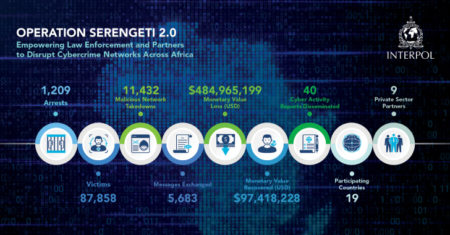
INTERPOL on Friday announced that authorities from 18 countries across Africa have arrested 1,209 cybercriminals who targeted 88,000 victims. “The…
Pentesting remains one of the most effective ways to identify real-world security weaknesses before adversaries do. But as the threat…
Cybersecurity researchers are calling attention to malicious activity orchestrated by a China-nexus cyber espionage group known as Murky Panda that…
An INTERPOL-coordinated operation, dubbed Operation Serengeti 2.0, delivered a telling blow to cybercrime across the African continent. The operation that…
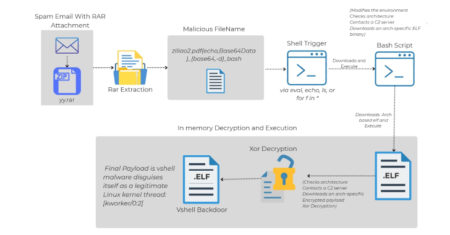
Cybersecurity researchers have shed light on a novel attack chain that employs phishing emails to deliver an open-source backdoor called…
Some cybersecurity news outlets were duped a few days ago by a claim that Europol was offering a $50,000 bounty…
The China-linked advanced persistent threat (APT) group Silk Typhoon has shown a rare ability to compromise trusted relationships in the…
I am trying to find an MQTT broker which is compatible with hive MQ’s Mqtt5AsyncClient, for integration test purposes.
I am writing tests using JUnit, and have tried moquette but that appears (for now) to only support MQTT v3, not v5.
Does anyone know of an embedded (i.e. can be run through java code directly) MQTT broker which I could use in this scenario?
#749 — August 22, 2025 Read on the Web ☀️ We’re back after a week off, though I’m starting to…

![From Hospital Janitor to Developer with Emmett Naughton [Podcast #185]](https://devstacktips.com/wp-content/uploads/2025/08/61d89f03-3b6f-4c86-9f70-695decea0e9d-2eTMjL-450x253.png)