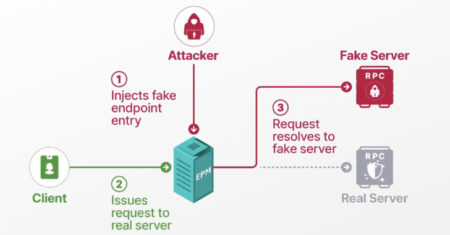
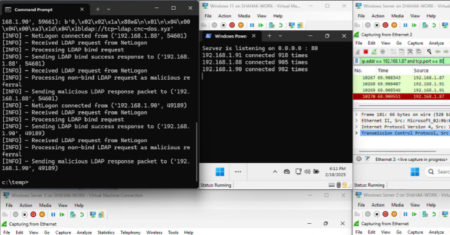
Cybersecurity researchers have presented new findings related to a now-patched security issue in Microsoft’s Windows Remote Procedure Call (RPC) communication…
Development
A novel attack technique could be weaponized to rope thousands of public domain controllers (DCs) around the world to create…
Staying one step ahead of cyber-criminals has never felt more urgent. According to CERT-IN, India recorded over 3 million cybersecurity incidents in 2024 alone, a figure that continues to climb as organisations accelerate their cloud, mobile, and IoT roll-outs. Meanwhile, compliance demands from the Personal Data Protection Act (PDPA) to PCI DSS are tightening every
The post VAPT in 2025: A Step‑by‑Step Guide appeared first on Codoid.
Comments Source: Read MoreÂ
Send Laravel errors to Flare Source: Read MoreÂ
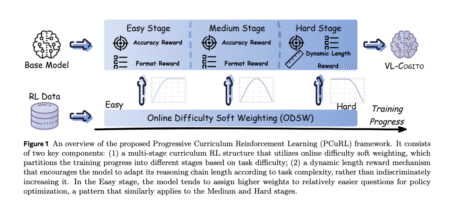
Multimodal reasoning, where models integrate and interpret information from multiple sources such as text, images, and diagrams, is a frontier…
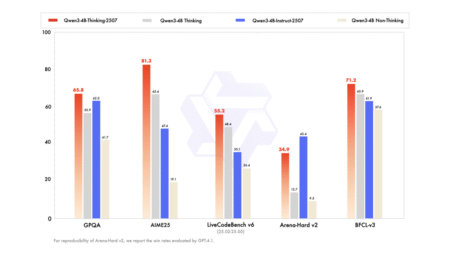
Smaller Models with Smarter Performance and 256K Context Support Alibaba’s Qwen team has introduced two powerful additions to its small…
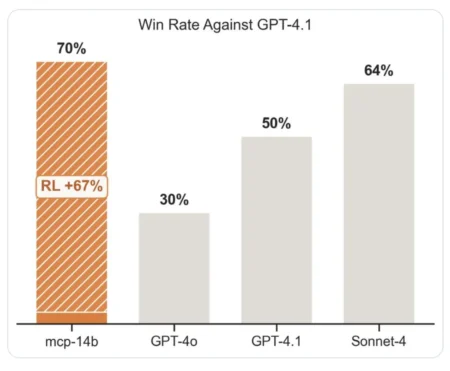
Table of contents Introduction What Is MCP- RL? ART: The Agent Reinforcement Trainer Code Walkthrough: Specializing LLMs with MCP- RL…
Table of contents TL;DR 1) What is an AI agent (2025 definition)? 2) What can agents do reliably today? 3)…
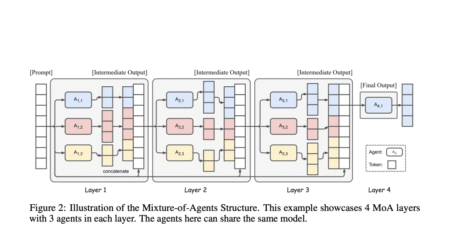
The Mixture-of-Agents (MoA) architecture is a transformative approach for enhancing large language model (LLM) performance, especially on complex, open-ended tasks…
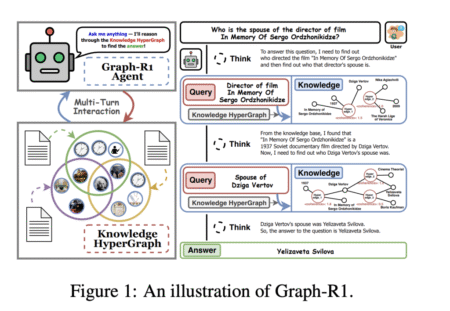
Introduction Large Language Models (LLMs) have set new benchmarks in natural language processing, but their tendency for hallucination—generating inaccurate outputs—remains…
In this tutorial, we walk through building an advanced PaperQA2 AI Agent powered by Google’s Gemini model, designed specifically for…
Table of contents Why Classic AI Agent Workflows Fail The 9 Agentic Workflow Patterns for 2025 Sequential Intelligence Parallel Processing…
Is your phone suddenly flooded with aggressive ads, slowing down performance or leading to unusual app behavior? Here’s what to…
A sky-high premium may not always reflect your company’s security posture Source: Read More
Cybersecurity researchers have discovered over a dozen vulnerabilities in enterprise secure vaults from CyberArk and HashiCorp that, if successfully exploited,…
Cybersecurity researchers have uncovered a jailbreak technique to bypass ethical guardrails erected by OpenAI in its latest large language model…
Cybersecurity researchers have disclosed vulnerabilities in select model webcams from Lenovo that could turn them into BadUSB attack devices. “This…
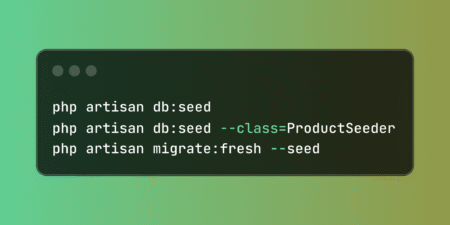
Establish reliable database foundations with Laravel’s comprehensive seeding system that enables consistent data environments across development stages. These tools support…
The yasin_tgh/laravel-postman Composer package generates Postman collections from your Laravel routes with intelligent organization and rich documentation capabilities. The post…