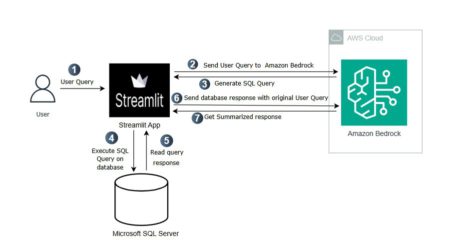
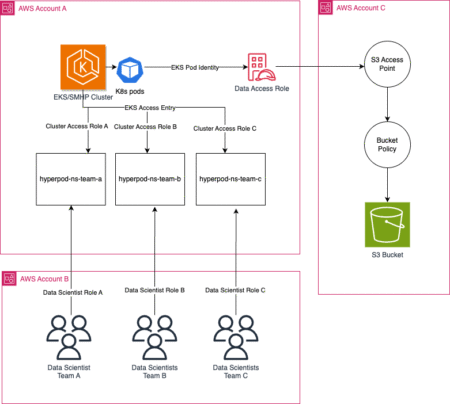
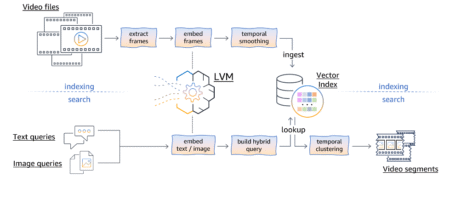
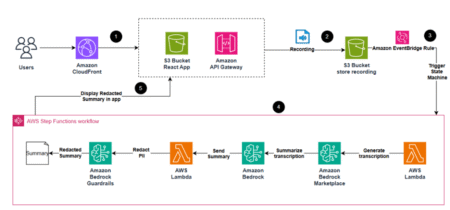
Businesses rely on precise, real-time insights to make critical decisions. However, enabling non-technical users to access proprietary or organizational data…
Development
GPUs are a precious resource; they are both short in supply and much more costly than traditional CPUs. They are…
As companies and individual users deal with constantly growing amounts of video content, the ability to perform low-effort search to…
Introduction: The Limits of Traditional AI Systems Conventional artificial intelligence systems are limited by their static architectures. These models operate…
Recordings of business meetings, interviews, and customer interactions have become essential for preserving important information. However, transcribing and summarizing these…
In this tutorial, we demonstrate how to combine the power of SerpAPI’s Google search capabilities with Google’s Gemini-1.5-Flash model to…
CVE ID : CVE-2025-5799
Published : June 6, 2025, 8:15 p.m. | 1 hour, 59 minutes ago
Description : A vulnerability was found in Tenda AC8 16.03.34.09. It has been declared as critical. Affected by this vulnerability is the function fromSetWirelessRepeat of the file /goform/WifiExtraSet. The manipulation of the argument wpapsk_crypto leads to stack-based buffer overflow. The attack can be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5798
Published : June 6, 2025, 8:15 p.m. | 1 hour, 59 minutes ago
Description : A vulnerability was found in Tenda AC8 16.03.34.09. It has been classified as critical. Affected is the function fromSetSysTime of the file /goform/SetSysTimeCfg. The manipulation of the argument timeType leads to stack-based buffer overflow. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-49127
Published : June 6, 2025, 9:15 p.m. | 2 hours, 34 minutes ago
Description : Kafbat UI is a web user interface for managing Apache Kafka clusters. An unsafe deserialization vulnerability in version 1.0.0 allows any unauthenticated user to execute arbitrary code on the server. Version 1.1.0 fixes the issue.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-49128
Published : June 6, 2025, 10:15 p.m. | 1 hour, 34 minutes ago
Description : Jackson-core contains core low-level incremental (“streaming”) parser and generator abstractions used by Jackson Data Processor. Starting in version 2.0.0 and prior to version 2.13.0, a flaw in jackson-core’s `JsonLocation._appendSourceDesc` method allows up to 500 bytes of unintended memory content to be included in exception messages. When parsing JSON from a byte array with an offset and length, the exception message incorrectly reads from the beginning of the array instead of the logical payload start. This results in possible information disclosure in systems using pooled or reused buffers, like Netty or Vert.x. This issue was silently fixed in jackson-core version 2.13.0, released on September 30, 2021, via PR #652. All users should upgrade to version 2.13.0 or later. If upgrading is not immediately possible, applications can mitigate the issue by disabling exception message exposure to clients to avoid returning parsing exception messages in HTTP responses and/or disabling source inclusion in exceptions to prevent Jackson from embedding any source content in exception messages, avoiding leakage.
Severity: 4.0 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE-2025-4318 Critical RCE in AWS Amplify Codegen UI
CVE-2025-4318 is a critical remote code execution (RCE) vulnerability identified in the @aws-amplify/codegen-ui NPM package—a core component used by AWS Amplify Studio for generating UI components bas …
Read more
Published Date:
Jun 06, 2025 (3 hours, 44 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-20286
CVE-2025-4318
Microsoft shares script to restore inetpub folder you shouldn’t delete
Microsoft has released a PowerShell script to help restore an empty ‘inetpub’ folder created by the April 2025 Windows security updates if deleted. As Microsoft previously warned, this folder helps mi …
Read more
Published Date:
Jun 06, 2025 (2 hours, 24 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-21204
DragonForce Ransomware Claimed To Compromise Over 120 Victims in The Past Year
DragonForce, a sophisticated ransomware operation that emerged in fall 2023, has established itself as a formidable threat in the cybercriminal landscape by claiming over 120 victims across the past y …
Read more
Published Date:
Jun 06, 2025 (1 hour, 18 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2024-21412
CVE-2024-21893
CVE-2024-21887
CVE ID : CVE-2025-5747
Published : June 6, 2025, 4:15 p.m. | 1 hour, 44 minutes ago
Description : WOLFBOX Level 2 EV Charger MCU Command Parsing Misinterpretation of Input Remote Code Execution Vulnerability. This vulnerability allows network-adjacent attackers to execute arbitrary code on affected installatons of WOLFBOX Level 2 EV Charger devices. Authentication is required to exploit this vulnerability.
The specific flaw exists within the handling of command frames received by the MCU. When parsing frames, the process does not properly detect the start of a frame, which can lead to misinterpretation of input. An attacker can leverage this in conjunction with other vulnerabilities to execute arbitrary code in the context of the device. Was ZDI-CAN-26501.
Severity: 8.0 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5748
Published : June 6, 2025, 4:15 p.m. | 1 hour, 44 minutes ago
Description : WOLFBOX Level 2 EV Charger LAN OTA Exposed Dangerous Method Remote Code Execution Vulnerability. This vulnerability allows network-adjacent attackers to execute arbitrary code on affected installations of WOLFBOX Level 2 EV Charger. Although authentication is required to exploit this vulnerability, the existing authentication mechanism can be bypassed.
The specific flaw exists within the Tuya communications module software. The issue results from the exposure of a method allowing the upload of crafted software images to the module. An attacker can leverage this vulnerability to execute code in the context of the device. Was ZDI-CAN-26349.
Severity: 8.0 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5750
Published : June 6, 2025, 4:15 p.m. | 3 hours, 33 minutes ago
Description : WOLFBOX Level 2 EV Charger tuya_svc_devos_activate_result_parse Heap-based Buffer Overflow Remote Code Execution Vulnerability. This vulnerability allows network-adjacent attackers to execute arbitrary code on affected installations of WOLFBOX Level 2 EV Charger. Authentication is not required to exploit this vulnerability.
The specific flaw exists within the handling of the secKey, localKey, stdTimeZone and devId parameters. The issue results from the lack of proper validation of the length of user-supplied data prior to copying it to a fixed-length heap-based buffer. An attacker can leverage this vulnerability to execute code in the context of the device. Was ZDI-CAN-26294.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5751
Published : June 6, 2025, 4:15 p.m. | 3 hours, 33 minutes ago
Description : WOLFBOX Level 2 EV Charger Management Card Hard-coded Credentials Authentication Bypass Vulnerability. This vulnerability allows physically present attackers to bypass authentication on affected installations of WOLFBOX Level 2 EV Charger. Authentication is not required to exploit this vulnerability.
The specific flaw exists within the handling of management cards. The issue results from the lack of personalization of management cards. An attacker can leverage this vulnerability to bypass authentication on the system. Was ZDI-CAN-26292.
Severity: 4.6 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5783
Published : June 6, 2025, 4:15 p.m. | 3 hours, 33 minutes ago
Description : A vulnerability, which was classified as critical, was found in PHPGurukul Employee Record Management System 1.3. This affects an unknown part of the file /editmyexp.php. The manipulation of the argument emp3workduration leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5784
Published : June 6, 2025, 4:15 p.m. | 3 hours, 33 minutes ago
Description : A vulnerability has been found in PHPGurukul Employee Record Management System 1.3 and classified as critical. This vulnerability affects unknown code of the file /myexp.php. The manipulation of the argument emp3ctc leads to sql injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5785
Published : June 6, 2025, 4:15 p.m. | 3 hours, 33 minutes ago
Description : A vulnerability was found in TOTOLINK X15 1.0.0-B20230714.1105 and classified as critical. This issue affects some unknown processing of the file /boafrm/formWirelessTbl of the component HTTP POST Request Handler. The manipulation of the argument submit-url leads to buffer overflow. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…