Google has agreed to pay the U.S. state of Texas nearly $1.4 billion to settle two lawsuits that accused the…
Development
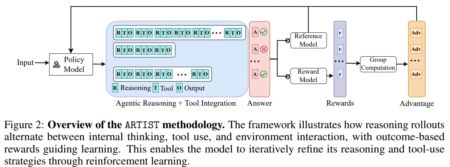
As autonomous systems increasingly rely on large language models (LLMs) for reasoning, planning, and action execution, a critical bottleneck has…
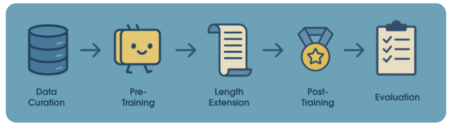
Language processing in enterprise environments faces critical challenges as business workflows increasingly depend on synthesising information from diverse sources, including…
ByteDance has released DeerFlow, an open-source multi-agent framework designed to enhance complex research workflows by integrating the capabilities of large…
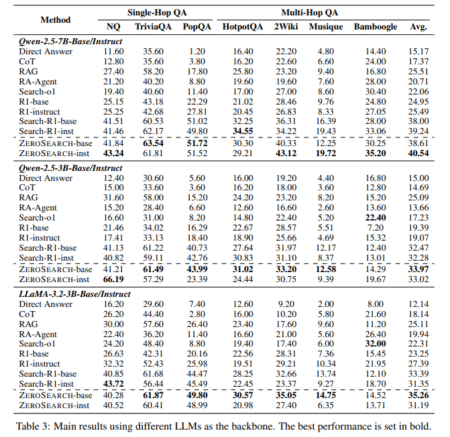
LLMs have made impressive gains in complex reasoning, primarily through innovations in architecture, scale, and training approaches like RL. RL…
Large language models are now central to various applications, from coding to academic tutoring and automated assistants. However, a critical…
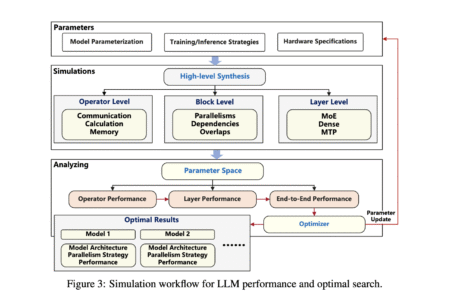
Sparse large language models (LLMs) based on the Mixture of Experts (MoE) framework have gained traction for their ability to…
In this tutorial, we walk you through setting up a fully functional bot in Google Colab that leverages Anthropic’s Claude…
CVE ID : CVE-2025-4514
Published : May 10, 2025, 8:15 p.m. | 4 hours, 9 minutes ago
Description : A vulnerability, which was classified as critical, has been found in Zhengzhou Jiuhua Electronic Technology mayicms up to 5.8E. Affected by this issue is some unknown functionality of the file /javascript.php. The manipulation of the argument Value leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4513
Published : May 10, 2025, 8:15 p.m. | 4 hours, 9 minutes ago
Description : A vulnerability classified as problematic was found in Catalyst User Key Authentication Plugin 20220819 on Moodle. Affected by this vulnerability is an unknown functionality of the file /auth/userkey/logout.php of the component Logout. The manipulation of the argument return leads to open redirect. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 4.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4515
Published : May 10, 2025, 9:15 p.m. | 3 hours, 9 minutes ago
Description : A vulnerability, which was classified as problematic, was found in Zylon PrivateGPT up to 0.6.2. This affects an unknown part of the file settings.yaml. The manipulation of the argument allow_origins leads to permissive cross-domain policy with untrusted domains. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 4.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47817
Published : May 10, 2025, 10:15 p.m. | 2 hours, 9 minutes ago
Description : In BlueWave Checkmate through 2.0.2 before b387eba, a profile edit request can include a role parameter.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47814
Published : May 10, 2025, 10:15 p.m. | 2 hours, 9 minutes ago
Description : libpspp-core.a in GNU PSPP through 2.0.1 allows attackers to cause a heap-based buffer overflow in inflate_read (called indirectly from spv_read_xml_member) in zip-reader.c.
Severity: 4.5 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47815
Published : May 10, 2025, 10:15 p.m. | 2 hours, 9 minutes ago
Description : libpspp-core.a in GNU PSPP through 2.0.1 allows attackers to cause a heap-based buffer overflow in inflate_read (called indirectly from zip_member_read_all) in zip-reader.c.
Severity: 4.5 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47816
Published : May 10, 2025, 10:15 p.m. | 2 hours, 9 minutes ago
Description : libpspp-core.a in GNU PSPP through 2.0.1 allows attackers to cause an spvxml-helpers.c spvxml_parse_attributes out-of-bounds read, related to extra content at the end of a document.
Severity: 2.9 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4525
Published : May 10, 2025, 11:15 p.m. | 1 hour, 9 minutes ago
Description : A vulnerability, which was classified as critical, has been found in Discord 1.0.9188 on Windows. Affected by this issue is some unknown functionality in the library WINSTA.dll. The manipulation leads to uncontrolled search path. The attack needs to be approached locally. The complexity of an attack is rather high. The exploitation is known to be difficult. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 7.0 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4507
Published : May 10, 2025, 5:15 p.m. | 3 hours, 8 minutes ago
Description : A vulnerability classified as critical has been found in Campcodes Online Food Ordering System 1.0. This affects an unknown part of the file /routers/add-item.php. The manipulation of the argument price leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4508
Published : May 10, 2025, 5:15 p.m. | 3 hours, 8 minutes ago
Description : A vulnerability classified as critical was found in PHPGurukul e-Diary Management System 1.0. This vulnerability affects unknown code of the file /my-profile.php. The manipulation of the argument fname leads to sql injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. Other parameters might be affected as well.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4509
Published : May 10, 2025, 6:15 p.m. | 2 hours, 8 minutes ago
Description : A vulnerability, which was classified as critical, has been found in PHPGurukul e-Diary Management System 1.0. This issue affects some unknown processing of the file /manage-notes.php. The manipulation of the argument ID leads to sql injection. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4510
Published : May 10, 2025, 6:15 p.m. | 2 hours, 8 minutes ago
Description : A vulnerability was found in Changjietong UFIDA CRM 1.0. It has been declared as critical. This vulnerability affects unknown code of the file /optnty/optntyday.php. The manipulation of the argument gblOrgID leads to sql injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…