Part 1: The Shadowless King The first rain of the monsoon came not as a blessing, but as a warning.…
Development
At PHPGurukul, we know the importance of your final year project—both as an assignment, but also as a genuine portrayal…
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
AnyCable is a broadcasting adapter for Laravel similar to Reverb The post AnyCable Laravel Broadcaster appeared first on Laravel News.…
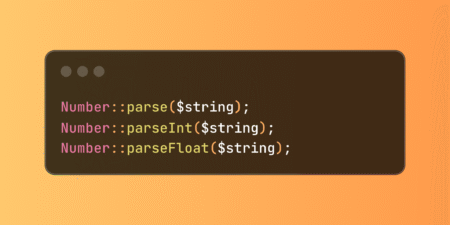
Laravel’s Number class provides locale-aware parsing methods that handle international number formats using PHP’s Intl extension. These utilities automatically convert…
Threat hunters are calling attention to a new variant of a remote access trojan (RAT) called Chaos RAT that has…
Cisco has released security patches to address a critical security flaw impacting the Identity Services Engine (ISE) that, if successfully…
Cybersecurity researchers have discovered a malicious package on the Python Package Index (PyPI) repository that’s capable of harvesting sensitive developer-related…
Introduction The cybersecurity landscape is evolving rapidly, and so are the cyber needs of organizations worldwide. While businesses face mounting…
Navigating the dense urban canyons of cities like San Francisco or New York can be a nightmare for GPS systems.…
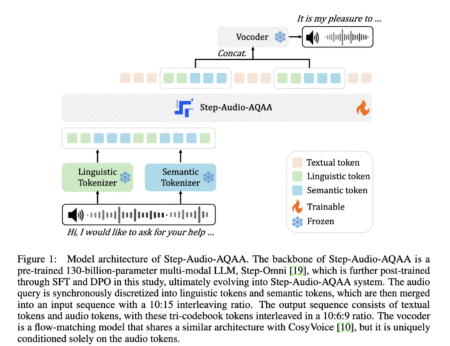
Rethinking Audio-Based Human-Computer Interaction Machines that can respond to human speech with equally expressive and natural audio have become a…
The blog discusses how AI-native product development redefines how digital solutions are built. It focuses on intelligence, automation, and real-time user value. This blog breaks down core pillars like AI-first design, MLOps, data analytics, and governance. Learn how best practices and frameworks like Tx-DevSecOps and Tx-Insights help organizations create scalable, ethical, and innovation-driven products ready for the AI-powered future.
The post AI-Native Product Development: 5 Pillars That Matter first appeared on TestingXperts.
LibreOffice 25.8 Beta 2 Drops Support for Windows 7/8/8.1 and All 32-bit Systems
The renowned open-source and free office suite, LibreOffice, has recently released version 25.8 Beta 2. According to the update changelog, this version officially discontinues support for Windows 7, W …
Read more
Published Date:
Jun 16, 2025 (3 hours, 23 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2023-6186
CVE-2023-6185
IBM Backup Services Vulnerability Let Attackers Escalate Privileges
A critical security vulnerability in IBM Backup, Recovery, and Media Services for the i platform that could allow attackers to gain elevated privileges and execute malicious code with component-level …
Read more
Published Date:
Jun 16, 2025 (3 hours, 23 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-33108
YouTube Expands 30-Second Non-Skippable Ads: Prepare for More Interruptions
At present, YouTube offers a wide array of advertising formats, including two sets of skippable ads, two sets of non-skippable ads, individual skippable ads, and extended 30-second non-skippable comme …
Read more
Published Date:
Jun 16, 2025 (3 hours, 12 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2024-47901
CVE ID : CVE-2025-6108
Published : June 16, 2025, 6:15 a.m. | 4 hours, 4 minutes ago
Description : A vulnerability was found in hansonwang99 Spring-Boot-In-Action up to 807fd37643aa774b94fd004cc3adbd29ca17e9aa. It has been declared as critical. Affected by this vulnerability is the function watermarkTest of the file /springbt_watermark/src/main/java/cn/codesheep/springbt_watermark/service/ImageUploadService.java of the component File Upload. The manipulation of the argument filename leads to path traversal. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. This product takes the approach of rolling releases to provide continious delivery. Therefore, version details for affected and updated releases are not available. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6110
Published : June 16, 2025, 7:15 a.m. | 3 hours, 4 minutes ago
Description : A vulnerability classified as critical has been found in Tenda FH1201 1.2.0.14(408). This affects an unknown part of the file /goform/SafeMacFilter. The manipulation of the argument page leads to stack-based buffer overflow. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6109
Published : June 16, 2025, 6:15 a.m. | 4 hours, 4 minutes ago
Description : A vulnerability was found in javahongxi whatsmars 2021.4.0. It has been rated as problematic. Affected by this issue is the function initialize of the file /whatsmars-archetypes/whatsmars-initializr/src/main/java/org/hongxi/whatsmars/initializr/controller/InitializrController.java. The manipulation of the argument artifactId leads to path traversal. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 4.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…