A new large-scale campaign has been observed exploiting over 100 compromised WordPress sites to direct site visitors to fake CAPTCHA…
Development
A suspected hacker, believed to be the mastermind behind an organised campaign of attacks that stole millions of dollars worth…
Cybersecurity researchers are calling attention to a sophisticated social engineering campaign that’s targeting supply chain-critical manufacturing companies with an in-memory…
In episode 65 of The AI Fix, a pigeon gives a PowerPoint presentation, Mark plays Graham a song about the…
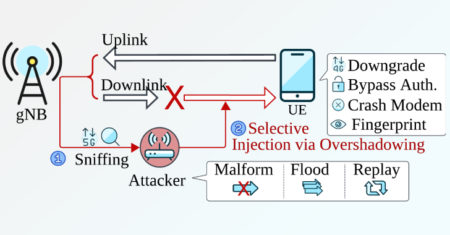
A team of academics has devised a novel attack that can be used to downgrade a 5G connection to a…
Citrix has released fixes to address three security flaws in NetScaler ADC and NetScaler Gateway, including one that it said…
The U.S. Cybersecurity and Information Security Agency (CISA) has added two Citrix vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog…
Currently I am checking a website.
In the website I need to check spelling errors and broken links.
Is there is any software/tool to do this task?
In the fast-moving world of software testing, creating and maintaining test cases is both a necessity and a burden. QA teams know the drill: requirements evolve, user stories multiply, and deadlines shrink. Manual test case creation, while thorough, simply cannot keep pace with today’s agile and DevOps cycles. This is where AI Test Case Generator
The post AI Test Case Generator: The Smarter Choice appeared first on Codoid.
Retail is changing, and AI is leading the transformation. From personalized shopping to smarter inventory and faster decision-making, retailers must adopt AI to stay competitive. This blog explores key strategies, scaling insights, barriers to adoption, and how TestingXperts ensures AI delivers real business impact.
The post AI in Retail: The Playbook for Retail Transformation first appeared on TestingXperts.
CVE ID : CVE-2025-55575
Published : Aug. 25, 2025, 4:15 p.m. | 1 day, 10 hours ago
Description : SQL Injection vulnerability in SMM Panel 3.1 allowing remote attackers to gain sensitive information via a crafted HTTP request with action=service_detail.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9443
Published : Aug. 26, 2025, 3:15 a.m. | 23 hours, 39 minutes ago
Description : A flaw has been found in Tenda CH22 1.0.0.1. This vulnerability affects the function formeditUserName of the file /goform/editUserName. Executing manipulation of the argument new_account can lead to buffer overflow. It is possible to launch the attack remotely. The exploit has been published and may be used.
Severity: 9.0 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5931
Published : Aug. 26, 2025, 5:15 a.m. | 21 hours, 39 minutes ago
Description : The Dokan Pro plugin for WordPress is vulnerable to privilege escalation via account takeover in all versions up to, and including, 4.0.5. This is due to the plugin not properly validating a user’s identity prior to updating their password during a staff password reset. This makes it possible for authenticated attackers, with vendor-level access and above, to elevate their privilege to the level of a staff member and then change arbitrary user passwords, including those of administrators in order to gain access to their accounts. By default, the plugin allows customers to become vendors.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-41702
Published : Aug. 26, 2025, 6:15 a.m. | 20 hours, 39 minutes ago
Description : The JWT secret key is embedded in the egOS WebGUI backend and is readable to the default user. An unauthenticated remote attacker can generate valid HS256 tokens and bypass authentication/authorization due to the use of hard-coded cryptographic key.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-53418
Published : Aug. 26, 2025, 7:15 a.m. | 19 hours, 39 minutes ago
Description : Delta Electronics COMMGR has Stack-based Buffer Overflow vulnerability.
Severity: 8.6 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7775
Published : Aug. 26, 2025, 1:15 p.m. | 13 hours, 39 minutes ago
Description : Memory overflow vulnerability leading to Remote Code Execution and/or Denial of Service in NetScaler ADC and NetScaler Gateway when NetScaler is configured as Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server
(OR)
NetScaler ADC and NetScaler Gateway 13.1, 14.1, 13.1-FIPS and NDcPP: LB virtual servers of type (HTTP, SSL or HTTP_QUIC) bound with IPv6 services or servicegroups bound with IPv6 servers
(OR)
NetScaler ADC and NetScaler Gateway 13.1, 14.1, 13.1-FIPS and NDcPP: LB virtual servers of type (HTTP, SSL or HTTP_QUIC) bound with DBS IPv6 services or servicegroups bound with IPv6 DBS servers
(OR)
CR virtual server with type HDX
Severity: 9.2 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7776
Published : Aug. 26, 2025, 1:15 p.m. | 13 hours, 39 minutes ago
Description : Memory overflow vulnerability leading to unpredictable or erroneous behavior and Denial of Service in NetScaler ADC and NetScaler Gateway when NetScaler is configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) with PCoIP Profile bounded to it
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-8424
Published : Aug. 26, 2025, 2:15 p.m. | 12 hours, 39 minutes ago
Description : Improper access control on the NetScaler Management Interface in NetScaler ADC and NetScaler Gateway when an attacker can get access to the appliance NSIP, Cluster Management IP or local GSLB Site IP or SNIP with Management Access
Severity: 8.7 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9481
Published : Aug. 26, 2025, 2:15 p.m. | 12 hours, 39 minutes ago
Description : A security vulnerability has been detected in Linksys RE6250, RE6300, RE6350, RE6500, RE7000 and RE9000 1.0.013.001/1.0.04.001/1.0.04.002/1.1.05.003/1.2.07.001. This affects the function setIpv6 of the file /goform/setIpv6. The manipulation of the argument tunrd_Prefix leads to stack-based buffer overflow. Remote exploitation of the attack is possible. The exploit has been disclosed publicly and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 9.0 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9482
Published : Aug. 26, 2025, 2:15 p.m. | 12 hours, 39 minutes ago
Description : A vulnerability was detected in Linksys RE6250, RE6300, RE6350, RE6500, RE7000 and RE9000 1.0.013.001/1.0.04.001/1.0.04.002/1.1.05.003/1.2.07.001. This impacts the function portRangeForwardAdd of the file /goform/portRangeForwardAdd. The manipulation of the argument ruleName/schedule/inboundFilter/TCPPorts/UDPPorts results in stack-based buffer overflow. The attack can be executed remotely. The exploit is now public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 9.0 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…