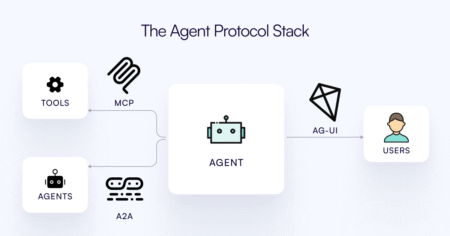
Introduction AI agents are increasingly moving from pure backend automators to visible, collaborative elements within modern applications. However, making agents…
Development
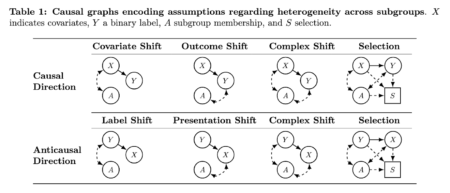
Understanding Subgroup Fairness in Machine Learning ML Evaluating fairness in machine learning often involves examining how models perform across different…
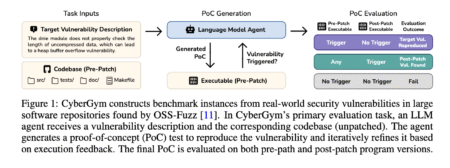
Cybersecurity has become a significant area of interest in artificial intelligence, driven by the increasing reliance on large software systems…
In this tutorial, we’ll build a powerful and interactive Streamlit application that brings together the capabilities of LangChain, the Google…
IBM QRadar SIEM Vulnerabilities Allows Attackers to Execute Arbitrary Commands
Multiple high-severity vulnerabilities in IBM QRadar SIEM could allow attackers to execute arbitrary commands and access sensitive data.
The most critical flaw, tracked as CVE-2025-33117, carries a CV …
Read more
Published Date:
Jun 20, 2025 (4 hours, 42 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-36050
CVE-2025-33121
CVE-2025-33117
Urgent WordPress Alert: Motors Theme Flaw (CVE-2025-4322) Actively Exploited for Site Takeover
Last month, a critical vulnerability was reported to Wordfence that now threatens more than 22,000 WordPress websites using the popular Motors automotive dealership theme. Tracked as CVE-2025-4322 and …
Read more
Published Date:
Jun 20, 2025 (3 hours, 33 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-4322
CVE-2024-50623
Apache SeaTunnel Vulnerability Allows Unauthorized Users to Perform Deserialization Attack
Apache SeaTunnel, the widely used distributed data integration platform, has disclosed a significant security vulnerability that enables unauthorized users to execute arbitrary file read operations an …
Read more
Published Date:
Jun 20, 2025 (1 hour, 44 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-32896
ClamAV 1.4.3 and 1.0.9 Released With Fix for Vulnerabilities that Enable Remote Code Execution
Multiple high-severity vulnerabilities, including a dangerous buffer overflow capable of remote code execution, have been fixed in critical security updates released by the ClamAV team for versions 1. …
Read more
Published Date:
Jun 20, 2025 (1 hour, 29 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-20260
CVE-2025-20234
CVE ID : CVE-2025-50054
Published : June 20, 2025, 7:15 a.m. | 3 hours, 27 minutes ago
Description : Buffer overflow in OpenVPN ovpn-dco-win version 1.3.0 and earlier and version 2.5.8 and earlier allows a local user process to send a too large control message buffer to the kernel driver resulting in a system crash
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6313
Published : June 20, 2025, 7:15 a.m. | 3 hours, 27 minutes ago
Description : A vulnerability was found in Campcodes Sales and Inventory System 1.0 and classified as critical. This issue affects some unknown processing of the file /pages/cat_add.php. The manipulation of the argument Category leads to sql injection. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6314
Published : June 20, 2025, 7:15 a.m. | 3 hours, 27 minutes ago
Description : A vulnerability was found in Campcodes Sales and Inventory System 1.0. It has been classified as critical. Affected is an unknown function of the file /pages/cat_update.php. The manipulation of the argument ID leads to sql injection. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6315
Published : June 20, 2025, 7:15 a.m. | 3 hours, 27 minutes ago
Description : A vulnerability was found in code-projects Online Shoe Store 1.0. It has been declared as critical. Affected by this vulnerability is an unknown functionality of the file /cart2.php. The manipulation of the argument ID leads to sql injection. The attack can be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6316
Published : June 20, 2025, 7:15 a.m. | 3 hours, 27 minutes ago
Description : A vulnerability was found in code-projects Online Shoe Store 1.0. It has been rated as critical. Affected by this issue is some unknown functionality of the file /admin/admin_running.php. The manipulation of the argument qty leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6317
Published : June 20, 2025, 8:15 a.m. | 2 hours, 27 minutes ago
Description : A vulnerability classified as critical has been found in code-projects Online Shoe Store 1.0. This affects an unknown part of the file /admin/confirm.php. The manipulation of the argument ID leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6318
Published : June 20, 2025, 8:15 a.m. | 2 hours, 27 minutes ago
Description : A vulnerability classified as critical was found in PHPGurukul Pre-School Enrollment System 1.0. This vulnerability affects unknown code of the file /admin/check_availability.php. The manipulation of the argument Username leads to sql injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6319
Published : June 20, 2025, 8:15 a.m. | 2 hours, 27 minutes ago
Description : A vulnerability, which was classified as critical, has been found in PHPGurukul Pre-School Enrollment System 1.0. This issue affects some unknown processing of the file /admin/add-teacher.php. The manipulation of the argument tsubject leads to sql injection. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6257
Published : June 20, 2025, 9:15 a.m. | 1 hour, 27 minutes ago
Description : The Euro FxRef Currency Converter plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin’s currency shortcode in all versions up to, and including, 2.0.2 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Severity: 6.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6320
Published : June 20, 2025, 9:15 a.m. | 1 hour, 27 minutes ago
Description : A vulnerability, which was classified as critical, was found in PHPGurukul Pre-School Enrollment System 1.0. Affected is an unknown function of the file /admin/add-class.php. The manipulation of the argument classname leads to sql injection. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6321
Published : June 20, 2025, 9:15 a.m. | 1 hour, 27 minutes ago
Description : A vulnerability has been found in PHPGurukul Pre-School Enrollment System 1.0 and classified as critical. Affected by this vulnerability is an unknown functionality of the file /admin/add-subadmin.php. The manipulation of the argument sadminusername leads to sql injection. The attack can be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6322
Published : June 20, 2025, 9:15 a.m. | 1 hour, 27 minutes ago
Description : A vulnerability was found in PHPGurukul Pre-School Enrollment System 1.0 and classified as critical. Affected by this issue is some unknown functionality of the file /visit.php. The manipulation of the argument gname leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…