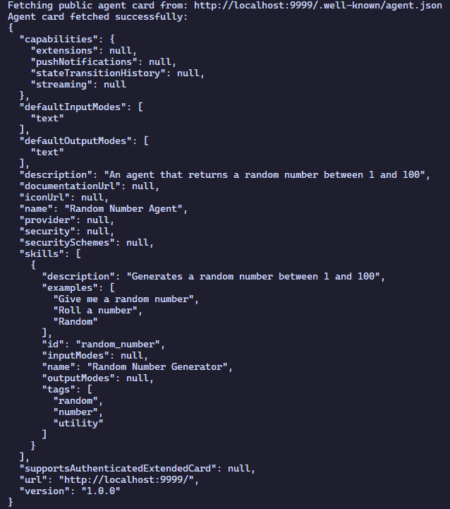
The Agent-to-Agent (A2A) protocol is a new standard by Google that enables AI agents—regardless of their underlying framework or developer—to…
Development
CVE ID : CVE-2025-5034
Published : June 21, 2025, 6:15 a.m. | 4 hours, 33 minutes ago
Description : The wp-file-download WordPress plugin before 6.2.6 does not sanitise and escape a parameter before outputting it back in the page, leading to a Reflected Cross-Site Scripting
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6400
Published : June 21, 2025, 6:15 a.m. | 3 hours, 14 minutes ago
Description : A vulnerability was found in TOTOLINK N300RH 6.1c.1390_B20191101 and classified as critical. Affected by this issue is some unknown functionality of the file /boafrm/formPortFw of the component HTTP POST Message Handler. The manipulation of the argument service_type leads to buffer overflow. The attack may be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5143
Published : June 21, 2025, 7:15 a.m. | 3 hours, 33 minutes ago
Description : The TableOn – WordPress Posts Table Filterable plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin’s tableon_popup_iframe_button shortcode in all versions up to, and including, 1.0.4.1 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Severity: 6.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6401
Published : June 21, 2025, 7:15 a.m. | 3 hours, 33 minutes ago
Description : A vulnerability was found in TOTOLINK N300RH 6.1c.1390_B20191101. It has been classified as problematic. This affects an unknown part of the file /boafrm/formFilter of the component HTTP POST Message Handler. The manipulation of the argument url leads to denial of service. The exploit has been disclosed to the public and may be used.
Severity: 3.5 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6402
Published : June 21, 2025, 9:15 a.m. | 1 hour, 33 minutes ago
Description : A vulnerability was found in TOTOLINK X15 1.0.0-B20230714.1105. It has been declared as critical. This vulnerability affects unknown code of the file /boafrm/formIpv6Setup of the component HTTP POST Request Handler. The manipulation of the argument submit-url leads to buffer overflow. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
Critical Mattermost Flaw (CVE-2025-4981, CVSS 9.9) Allows RCE Via Path Traversal
Open-source collaboration platform Mattermost is exposed to a severe vulnerability that threatens the integrity of its deployments worldwide. Tracked as CVE-2025-4981, this critical flaw (CVSS 9.9) al …
Read more
Published Date:
Jun 21, 2025 (4 hours, 54 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-4981
CVE-2025-25279
CVE-2025-24490
CVE-2025-20051
CVE ID : CVE-2025-52556
Published : June 21, 2025, 2:15 a.m. | 4 hours ago
Description : rfc3161-client is a Python library implementing the Time-Stamp Protocol (TSP) described in RFC 3161. Prior to version 1.0.3, there is a flaw in the timestamp response signature verification logic. In particular, chain verification is performed against the TSR’s embedded certificates up to the trusted root(s), but fails to verify the TSR’s own signature against the timestamping leaf certificates. Consequently, vulnerable versions perform insufficient signature validation to properly consider a TSR verified, as the attacker can introduce any TSR signature so long as the embedded leaf chains up to some root TSA. This issue has been patched in version 1.0.3. There is no workaround for this issue.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6394
Published : June 21, 2025, 2:15 a.m. | 4 hours ago
Description : A vulnerability was found in code-projects Simple Online Hotel Reservation System 1.0. It has been declared as critical. Affected by this vulnerability is an unknown functionality of the file /add_reserve.php. The manipulation of the argument firstname leads to sql injection. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. Other parameters might be affected as well.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-52557
Published : June 21, 2025, 2:15 a.m. | 4 hours ago
Description : Mail-0’s Zero is an open-source email solution. In version 0.8 it’s possible for an attacker to craft an email that executes javascript leading to session hijacking due to improper sanitization. This issue has been patched in version 0.81.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-52485
Published : June 21, 2025, 3:15 a.m. | 3 hours ago
Description : DNN (formerly DotNetNuke) is an open-source web content management platform (CMS) in the Microsoft ecosystem. In versions 6.0.0 to before 10.0.1, DNN.PLATFORM allows a specially crafted request to inject scripts in the Activity Feed Attachments endpoint which will then render in the feed. This issue has been patched in version 10.0.1.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-52486
Published : June 21, 2025, 3:15 a.m. | 3 hours ago
Description : DNN (formerly DotNetNuke) is an open-source web content management platform (CMS) in the Microsoft ecosystem. In versions 6.0.0 to before 10.0.1, DNN.PLATFORM allows specially crafted content in URLs to be used with TokenReplace and not be properly sanitized by some SkinObjects. This issue has been patched in version 10.0.1.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-52488
Published : June 21, 2025, 3:15 a.m. | 3 hours ago
Description : DNN (formerly DotNetNuke) is an open-source web content management platform (CMS) in the Microsoft ecosystem. In versions 6.0.0 to before 10.0.1, DNN.PLATFORM allows a specially crafted series of malicious interaction to potentially expose NTLM hashes to a third party SMB server. This issue has been patched in version 10.0.1.
Severity: 8.6 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-52487
Published : June 21, 2025, 3:15 a.m. | 3 hours ago
Description : DNN (formerly DotNetNuke) is an open-source web content management platform (CMS) in the Microsoft ecosystem. In versions 7.0.0 to before 10.0.1, DNN.PLATFORM allows a specially crafted request or proxy to be created that could bypass the design of DNN Login IP Filters allowing login attempts from IP Addresses not in the allow list. This issue has been patched in version 10.0.1.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-52552
Published : June 21, 2025, 3:15 a.m. | 3 hours ago
Description : FastGPT is an AI Agent building platform. Prior to version 4.9.12, the LastRoute Parameter on login page is vulnerable to open redirect and DOM-based XSS. Improper validation and lack of sanitization of this parameter allows attackers execute malicious JavaScript or redirect them to attacker-controlled sites. This issue has been patched in version 4.9.12.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6399
Published : June 21, 2025, 4:15 a.m. | 2 hours ago
Description : A vulnerability, which was classified as critical, was found in TOTOLINK X15 1.0.0-B20230714.1105. Affected is an unknown function of the file /boafrm/formIPv6Addr of the component HTTP POST Request Handler. The manipulation of the argument submit-url leads to buffer overflow. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
IBM QRadar SIEM Exposed by Trio of Security Flaws, Including Critical Command Execution Bug
IBM has issued a security bulletin addressing three critical vulnerabilities in its QRadar SIEM platform, a widely used solution for security information and event management. The flaws—ranging from l …
Read more
Published Date:
Jun 21, 2025 (2 hours, 43 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-36050
CVE-2025-33121
CVE-2025-33117
CVE ID : CVE-2025-6371
Published : June 20, 2025, 11:15 p.m. | 2 hours, 31 minutes ago
Description : A vulnerability, which was classified as critical, has been found in D-Link DIR-619L 2.06B01. Affected by this issue is the function formSetEnableWizard of the file /goform/formSetEnableWizard. The manipulation of the argument curTime leads to stack-based buffer overflow. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. This vulnerability only affects products that are no longer supported by the maintainer.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6372
Published : June 20, 2025, 11:15 p.m. | 1 hour, 44 minutes ago
Description : A vulnerability, which was classified as critical, was found in D-Link DIR-619L 2.06B01. This affects the function formSetWizard1 of the file /goform/formSetWizard1. The manipulation of the argument curTime leads to stack-based buffer overflow. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. This vulnerability only affects products that are no longer supported by the maintainer.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6373
Published : June 21, 2025, 12:15 a.m. | 44 minutes ago
Description : A vulnerability has been found in D-Link DIR-619L 2.06B01 and classified as critical. This vulnerability affects the function formSetWizard1 of the file /goform/formWlSiteSurvey. The manipulation of the argument curTime leads to stack-based buffer overflow. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. This vulnerability only affects products that are no longer supported by the maintainer.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…