My 30-year technology career has taught me many things…and one big thing: the companies that treat technology as a cost…
Development
Cybersecurity researchers have disclosed details of a new campaign that leverages ConnectWise ScreenConnect, a legitimate Remote Monitoring and Management (RMM)…
As bad actors often simply waltz through companies’ digital front doors with a key, here’s how to keep your own…
Cybersecurity researchers have disclosed two new campaigns that are serving fake browser extensions using malicious ads and fake websites to…
CISOs know their field. They understand the threat landscape. They understand how to build a strong and cost-effective security stack.…
Threat actors affiliated with the Akira ransomware group have continued to target SonicWall devices for initial access. Cybersecurity firm Rapid7…
The Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC) has issued an urgent alert regarding active exploitation of a…
A fresh firestorm has erupted over Microsoft’s handling of cybersecurity risks, with U.S. Senator Ron Wyden (D-OR) calling on the…
SAP has released a new security update addressing a broad range of vulnerabilities across its product ecosystem. Among the most…
U.S. Senator Ron Wyden has called on the Federal Trade Commission (FTC) to probe Microsoft and hold it responsible for…
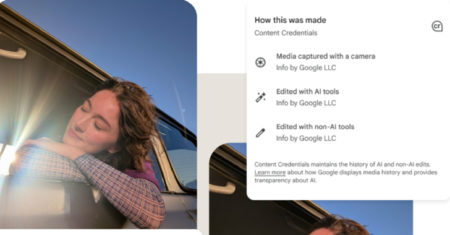
Google on Tuesday announced that its new Google Pixel 10 phones support the Coalition for Content Provenance and Authenticity (C2PA)…
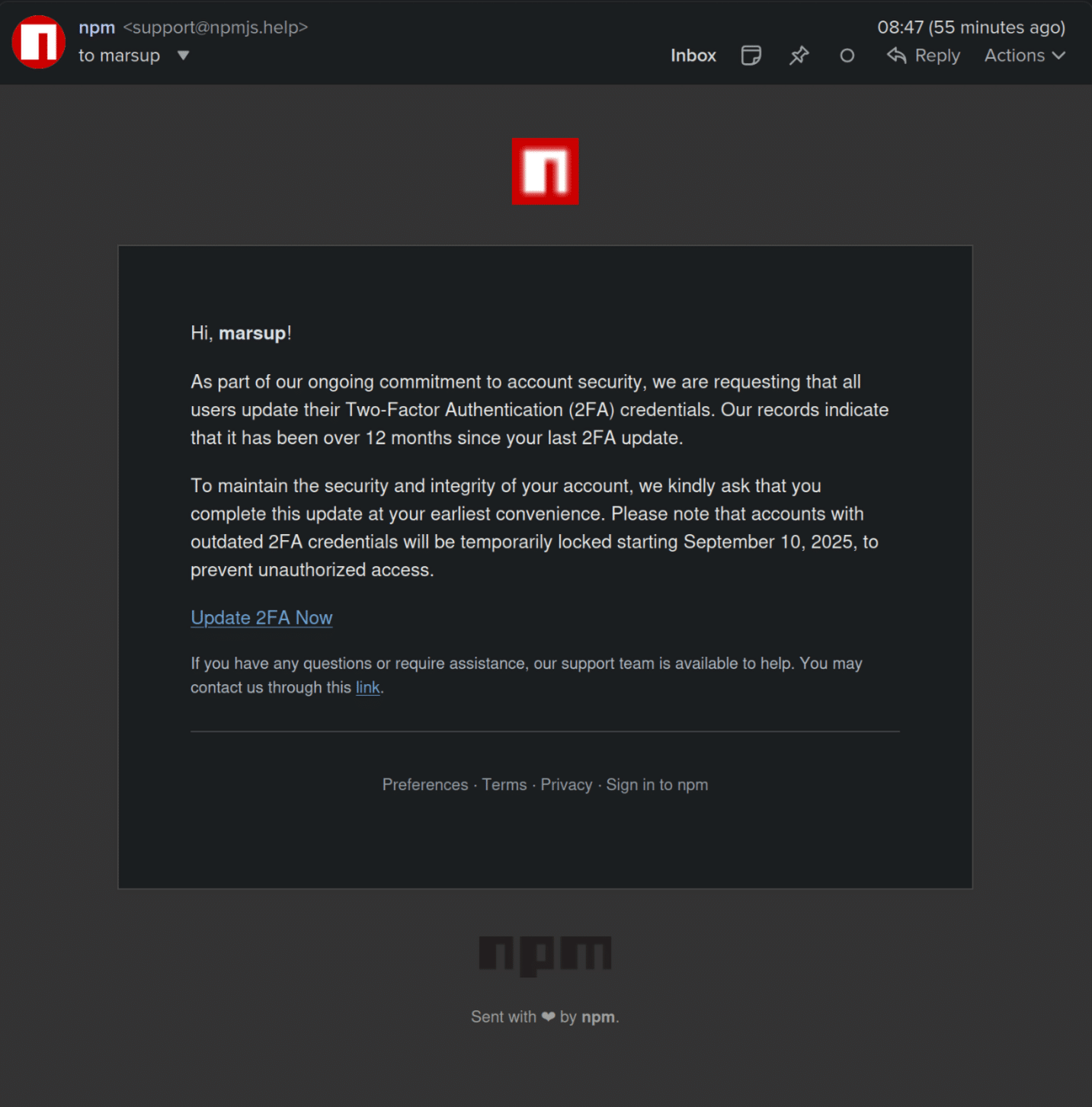
A massive NPM supply chain attack that hit about 10% of all cloud environments yielded little for the hackers who…
A massive NPM supply chain attack that hit about 10% of all cloud environments yielded little for the hackers who…
Building a browser extension is easy, but ensuring that it’s accessible to everyone takes deliberate care and skill. Your extension…
Ever wanted to build your own video game but felt overwhelmed by where to start? We just published a course…
Most developers are introduced to databases and APIs through a simple pattern: CRUD—Create, Read, Update, Delete. It seems like the…
After graduation, I noticed many fresh grads struggling to land jobs. It wasn’t because they lacked effort or qualifications. The…
YouTube playlists have become one of the most powerful ways to organize, promote, and binge-watch content. In India, trending playlists…
The U.S. Department of Energy’s National Nuclear Security Administration (DOE/NNSA) recently announced that it has selected MIT to establish a new…
Top News Judge puts Anthropic’s $1.5 billion book piracy settlement on hold A federal judge has paused Anthropic’s proposed $1.5…