The reconnaissance activity targeting American cybersecurity company SentinelOne was part of a broader set of partially-related intrusions into several targets…
Development
Iran has throttled internet access in the country in a purported attempt to hamper Israel’s ability to conduct covert cyber…
A former U.S. Central Intelligence Agency (CIA) analyst has been sentenced to little more than three years in prison for…
Cybersecurity researchers have exposed a previously unknown threat actor known as Water Curse that relies on weaponized GitHub repositories to…
For organizations eyeing the federal market, FedRAMP can feel like a gated fortress. With strict compliance requirements and a notoriously…
The Israel-Iran conflict that began with Israeli attacks on Iranian nuclear and military targets on June 13 has sparked a…
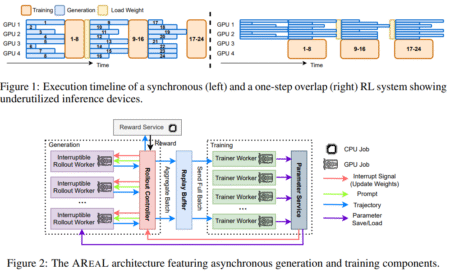
Introduction: The Need for Efficient RL in LRMs Reinforcement Learning RL is increasingly used to enhance LLMs, especially for reasoning…
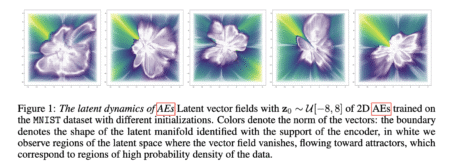
Autoencoders and the Latent Space Neural networks are designed to learn compressed representations of high-dimensional data, and autoencoders (AEs) are…
Kernel-level container insights: Utilizing eBPF with Cilium, Tetragon, and SBOMs for security
As applications become more distributed, traditional monitoring and security tools are failing to keep pace. This article explores how eBPF, when utilized by the graduated CNCF Cilium and its sub-proj …
Read more
Published Date:
Jun 18, 2025 (4 hours, 33 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2021-44228
Critical Linux Privilege Escalation Vulnerabilities Let Attackers Gain Full Root Access
Two critical, interconnected flaws, CVE-2025-6018 and CVE-2025-6019, enable unprivileged attackers to achieve root access on major Linux distributions.
Affecting millions worldwide, these vulnerabilit …
Read more
Published Date:
Jun 18, 2025 (4 hours, 1 minute ago)
Vulnerabilities has been mentioned in this article.
CSG waarschuwt voor kritiek beveiligingslek in NetScaler Gateway en ADC
De Cloud Software Group (CSG) waarschuwt voor een kritieke kwetsbaarheid in NetScaler ADC en NetScaler Gateway die tot een “memory overread” kan leiden. Een aanvaller zou zo vertrouwelijke informatie …
Read more
Published Date:
Jun 18, 2025 (2 hours, 58 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-5777
CISA Warns of Linux Kernel Improper Ownership Management Vulnerability Exploited in Attacks
CISA has added a critical Linux kernel vulnerability to its Known Exploited Vulnerabilities (KEV) catalog, warning that CVE-2023-0386 is being actively exploited in real-world attacks.
This improper o …
Read more
Published Date:
Jun 18, 2025 (2 hours, 57 minutes ago)
Vulnerabilities has been mentioned in this article.
Chrome Vulnerabilities Let Attackers Execute Arbitrary Code – Update Now!
Google has released an urgent security update for Chrome browsers across all desktop platforms, addressing critical vulnerabilities that could allow attackers to execute arbitrary code on users’ syste …
Read more
Published Date:
Jun 18, 2025 (2 hours, 54 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE ID : CVE-2025-1562
Published : June 18, 2025, 8:15 a.m. | 1 hour, 14 minutes ago
Description : The Recover WooCommerce Cart Abandonment, Newsletter, Email Marketing, Marketing Automation By FunnelKit plugin for WordPress is vulnerable to unauthorized arbitrary plugin installation due to a missing capability check on the install_or_activate_addon_plugins() function and a weak nonce hash in all versions up to, and including, 3.5.3. This makes it possible for unauthenticated attackers to install arbitrary plugins on the site that can be leveraged to further infect a vulnerable site.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5981
Published : June 18, 2025, 9:15 a.m. | 14 minutes ago
Description : Arbitrary file write as the OSV-SCALIBR user on the host system via a path traversal vulnerability when using OSV-SCALIBR’s unpack() function for container images. Particularly, when using the CLI flag –remote-image on untrusted container images.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
The “Infinite Workday” is Here: Microsoft Warns of Never-Ending Work Driven by Hybrid Models & AI
Microsoft recently released a new study titled “2025 Work Trend Index Annual Report,” in which it issues a warning about the rise of the “infinite workday.” The report describes this phenomenon as a p …
Read more
Published Date:
Jun 18, 2025 (3 hours, 30 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2024-24787
CVE-2023-34966
Mastodon Cracks Down: New Terms Ban Unauthorized AI Data Scraping
The decentralized social networking platform Mastodon has recently issued an email to its users, notifying them of an update to its Terms of Service. The most significant change introduced is a formal …
Read more
Published Date:
Jun 18, 2025 (3 hours, 14 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2024-23832
CVE-2023-36460
Linux Kernel Flaw (CVE-2023-0386) Actively Exploited for Root Privilege Escalation, PoC Available
A dangerous Linux privilege escalation vulnerability, CVE-2023-0386, has officially entered the CISA Known Exploited Vulnerabilities (KEV) Catalog amid confirmed reports of active exploitation in the …
Read more
Published Date:
Jun 18, 2025 (3 hours, 51 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2023-0386
Trinper Backdoor Exploiting Chrome Zero-Day CVE-2025-2783
A critical vulnerability in Google Chrome, tracked as CVE-2025-2783, has been exploited in cyberattacks deploying the Trinper backdoor. The flaw, a sandbox escape vulnerability, enables attackers to e …
Read more
Published Date:
Jun 18, 2025 (3 hours, 13 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-26685
CVE-2025-2783
KimJongRAT Returns: New PE & PowerShell Variants Steal Crypto and Browser Data via CDNs
Unit 42 has uncovered two newly evolved variants of the KimJongRAT malware, one using traditional PE (Portable Executable) files and the other employing PowerShell-based scripts to infiltrate systems, …
Read more
Published Date:
Jun 18, 2025 (2 hours, 21 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2023-2530