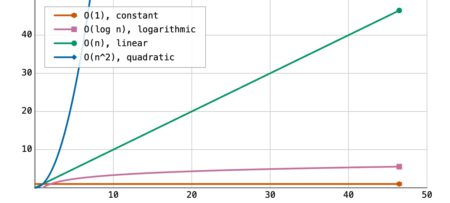
#750 — August 29, 2025 Read on the Web JavaScript Weekly An Illustrated Guide to Big O and Time Complexity…
Development
Comments Source: Read MoreÂ
CVE ID : CVE-2025-39247
Published : Aug. 29, 2025, 3:15 a.m. | 23 hours, 54 minutes ago
Description : There is an Access Control Vulnerability in some HikCentral Professional versions. This could allow an unauthenticated user to obtain the admin permission.
Severity: 8.6 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9605
Published : Aug. 29, 2025, 3:15 a.m. | 23 hours, 54 minutes ago
Description : A security vulnerability has been detected in Tenda AC21 and AC23 16.03.08.16. Affected is the function GetParentControlInfo of the file /goform/GetParentControlInfo. Such manipulation of the argument mac leads to stack-based buffer overflow. The attack can be launched remotely. The exploit has been disclosed publicly and may be used.
Severity: 10.0 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-8857
Published : Aug. 29, 2025, 4:15 a.m. | 22 hours, 54 minutes ago
Description : Clinic Image System developed by Changing contains hard-coded Credentials, allowing unauthenticated remote attackers to log into the system using administrator credentials embedded in the source code.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-8858
Published : Aug. 29, 2025, 4:15 a.m. | 22 hours, 54 minutes ago
Description : Clinic Image System developed by Changing has a SQL Injection vulnerability, allowing unauthenticated remote attackers to inject arbitrary SQL commands to read database contents.
Severity: 8.7 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-8861
Published : Aug. 29, 2025, 4:15 a.m. | 22 hours, 54 minutes ago
Description : TSA developed by Changing has a Missing Authentication vulnerability, allowing unauthenticated remote attackers to read, modify, and delete database contents.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9639
Published : Aug. 29, 2025, 4:16 a.m. | 22 hours, 54 minutes ago
Description : The QbiCRMGateway developed by Ai3 has an Arbitrary File Reading vulnerability, allowing unauthenticated remote attackers to exploit Relative Path Traversal to download arbitrary system files.
Severity: 8.7 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-53508
Published : Aug. 29, 2025, 5:15 a.m. | 21 hours, 54 minutes ago
Description : Multiple products provided by iND Co.,Ltd contain an OS command injection vulnerability. If exploited, an arbitrary OS command may be executed and sensitive information may be obtained. As for the details of affected product names and versions, refer to the information under [Product Status].
Severity: 8.6 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2024-13342
Published : Aug. 29, 2025, 11:15 a.m. | 15 hours, 54 minutes ago
Description : The Booster for WooCommerce plugin for WordPress is vulnerable to arbitrary file uploads due to missing file type validation in the ‘add_files_to_order’ function in all versions up to, and including, 7.2.4. This makes it possible for unauthenticated attackers to upload arbitrary files with double extensions on the affected site’s server which may make remote code execution possible. This is only exploitable on select instances where the configuration will execute the first extension present.
Severity: 8.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2024-46916
Published : Aug. 29, 2025, 4:15 p.m. | 10 hours, 54 minutes ago
Description : Diebold Nixdorf Vynamic Security Suite through 4.3.0 SR06 contains functionality that allows the removal of critical system files before the filesystem is properly mounted (e.g., leveraging a delete call in /etc/rc.d/init.d/mountfs to remove the /etc/fstab file). This can allow code execution and, in some versions, enable recovery of TPM Disk Encryption keys and decryption of the Windows system partition.
Severity: 8.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2024-46917
Published : Aug. 29, 2025, 4:15 p.m. | 10 hours, 54 minutes ago
Description : Diebold Nixdorf Vynamic Security Suite through 4.3.0 SR01 does not validate file attributes or the contents of /root during integrity validation. This allows code execution, recovery of TPM Disk Encryption keys, decryption of the Windows system partition, and full control of the Windows OS, e.g., through ~/.profile changes.
Severity: 8.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-55177
Published : Aug. 29, 2025, 4:15 p.m. | 10 hours, 54 minutes ago
Description : Incomplete authorization of linked device synchronization messages in WhatsApp for iOS prior to v2.25.21.73, WhatsApp Business for iOS v2.25.21.78, and WhatsApp for Mac v2.25.21.78 could have allowed an unrelated user to trigger processing of content from an arbitrary URL on a target’s device. We assess that this vulnerability, in combination with an OS-level vulnerability on Apple platforms (CVE-2025-43300), may have been exploited in a sophisticated attack against specific targeted users.
Severity: 8.0 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-30277
Published : Aug. 29, 2025, 6:15 p.m. | 8 hours, 54 minutes ago
Description : An improper certificate validation vulnerability has been reported to affect Qsync Central. If a remote attacker gains a user account, they can then exploit the vulnerability to compromise the security of the system.
We have already fixed the vulnerability in the following version:
Qsync Central 4.5.0.7 ( 2025/04/23 ) and later
Severity: 8.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-30278
Published : Aug. 29, 2025, 6:15 p.m. | 8 hours, 54 minutes ago
Description : An improper certificate validation vulnerability has been reported to affect Qsync Central. If a remote attacker gains a user account, they can then exploit the vulnerability to compromise the security of the system.
We have already fixed the vulnerability in the following version:
Qsync Central 4.5.0.7 ( 2025/04/23 ) and later
Severity: 8.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44033
Published : Aug. 29, 2025, 6:15 p.m. | 8 hours, 54 minutes ago
Description : SQL injection vulnerability in oa_system oasys v.1.1 allows a remote attacker to execute arbitrary code via the allDirector() method declaration in src/main/java/cn/gson/oasys/mappers/AddressMapper.java
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-52856
Published : Aug. 29, 2025, 6:15 p.m. | 8 hours, 54 minutes ago
Description : An improper authentication vulnerability has been reported to affect VioStor. If a remote attacker, they can then exploit the vulnerability to compromise the security of the system.
We have already fixed the vulnerability in the following version:
VioStor 5.1.6 build 20250621 and later
Severity: 9.3 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-58158
Published : Aug. 29, 2025, 6:15 p.m. | 8 hours, 54 minutes ago
Description : Harness Open Source is an end-to-end developer platform with Source Control Management, CI/CD Pipelines, Hosted Developer Environments, and Artifact Registries. Prior to version 3.3.0, Open Source Harness git LFS server (Gitness) exposes api to retrieve and upload files via git LFS. Implementation of upload git LFS file api is vulnerable to arbitrary file write. Due to improper sanitization for upload path, a malicious authenticated user who has access to Harness Gitness server api can use a crafted upload request to write arbitrary file to any location on file system, may even compromise the server. Users using git LFS are vulnerable. This issue has been patched in version 3.3.0.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9377
Published : Aug. 29, 2025, 6:15 p.m. | 8 hours, 54 minutes ago
Description : The authenticated remote command execution (RCE) vulnerability exists in the Parental Control page on TP-Link Archer C7(EU) V2 and TL-WR841N/ND(MS) V9.
This issue affects Archer C7(EU) V2: before 241108 and TL-WR841N/ND(MS) V9: before 241108.
Both products have reached the status of EOL (end-of-life).
It’s recommending to
purchase the new
product to ensure better performance and security. If replacement is not
an option in the short term, please use the second reference link to
download and install the patch(es).
Severity: 8.6 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9669
Published : Aug. 29, 2025, 7:15 p.m. | 6 hours, 12 minutes ago
Description : A vulnerability has been found in Jinher OA 1.0. This issue affects some unknown processing of the file GetTreeDate.aspx. The manipulation of the argument ID leads to sql injection. Remote exploitation of the attack is possible. The exploit has been disclosed to the public and may be used.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…