CVE ID : CVE-2025-53539
Published : July 7, 2025, 8:15 p.m. | 2 hours, 29 minutes ago
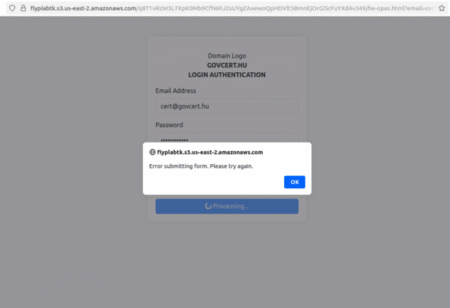
Description : FastAPI Guard is a security library for FastAPI that provides middleware to control IPs, log requests, and detect penetration attempts. fastapi-guard’s penetration attempts detection uses regex to scan incoming requests. However, some of the regex patterns used in detection are extremely inefficient and can cause polynomial complexity backtracks when handling specially crafted inputs. This vulnerability is fixed in 3.0.1.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…