Well well well, in news that will shock absolutely no-one it has been confirmed that Ingram Micro was hit by…
Development
A threat actor with suspected ties to India has been observed targeting a European foreign affairs ministry with malware capable…
The AiLock ransomware gang gives its victims just 72 hours to respond and five days to pay up… or else.…
As Texas reels from devastating floods, conspiracy theorists are hard at work. Source: Read More
The Initial Access Broker (IAB) known as Gold Melody has been attributed to a campaign that exploits leaked ASP.NET machine…
In episode 425 of “Smashing Security”, Graham reveals how “Call of Duty: WWII” has been weaponised – allowing hackers to…
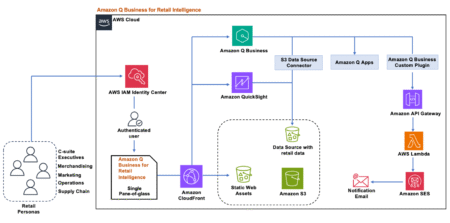
Generative AI continues to reshape how businesses approach innovation and problem-solving. Customers are moving from experimentation to scaling generative AI…
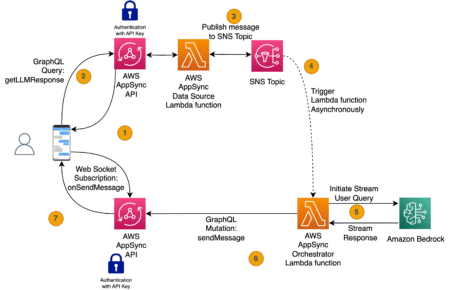
Many enterprises are using large language models (LLMs) in Amazon Bedrock to gain insights from their internal data sources. Amazon…
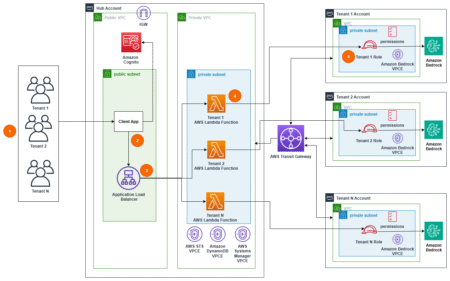
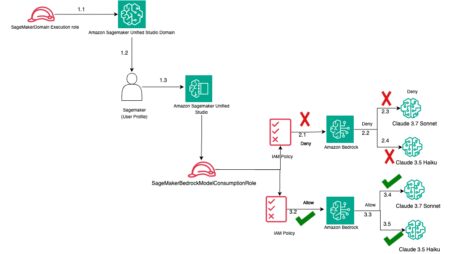
Enterprises adopting advanced AI solutions recognize that robust security and precise access control are essential for protecting valuable data, maintaining…
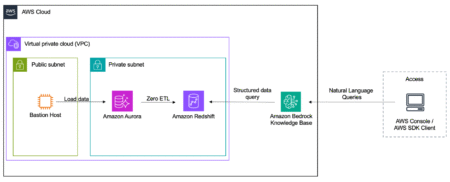
Amazon Bedrock Knowledge Bases offers a fully managed Retrieval Augmented Generation (RAG) feature that connects large language models (LLMs) to…
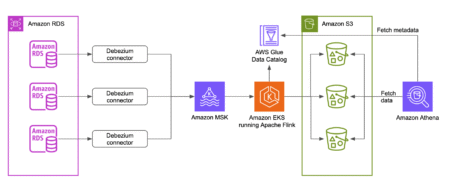
This post was co-written with Le Vy from Parcel Perform. Access to accurate data is often the true differentiator of…
Businesses often face challenges in managing and deriving value from their data. According to McKinsey, 78% of organizations now use…
Imagine a system that can explore multiple approaches to complex problems, drawing on its understanding of vast amounts of data,…
This paper was accepted at the Workshop on Reliable and Responsible Foundation Models (RRFMs) Workshop at ICML 2025. Uncertainty quantification…
The success of large language models in text processing has inspired their adaptation to speech modeling. However, since speech is…
Discrete diffusion is a promising framework for modeling and generating discrete data. In this work, we present Target Concrete Score…
Large Language Models (LLMs) are increasingly used in applications requiring long context lengths, but the key-value (KV) cache often becomes…
The adoption of text-to-image diffusion models raises concerns over reliability, drawing scrutiny under the lens of various metrics like calibration,…
Let’s be real for a second—Viber doesn’t get the spotlight like WhatsApp or Telegram. But you know what? That’s exactly…
Comments Source: Read MoreÂ