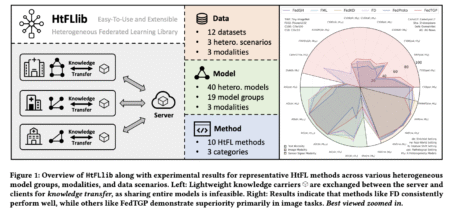
AI institutions develop heterogeneous models for specific tasks but face data scarcity challenges during training. Traditional Federated Learning (FL) supports…
Development
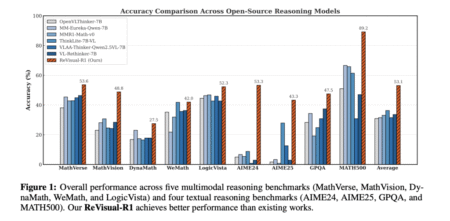
The Challenge of Multimodal Reasoning Recent breakthroughs in text-based language models, such as DeepSeek-R1, have demonstrated that RL can aid…
OpenAI has open-sourced a new multi-agent customer service demo on GitHub, showcasing how to build domain-specialized AI agents using its…
Automation testing has long been a cornerstone of efficient software development and quality assurance processes. Selenium, as a widely adopted automation testing tool, has empowered testers to perform web application testing effectively. However, with the integration of Artificial Intelligence (AI) and Machine Learning (ML), Selenium testing is undergoing a paradigm shift, enabling smarter, faster, and more accurate test automation.
This blog explores how AI and ML are transforming Selenium testing, their benefits, use cases, and the future of automation testing.
Understanding AI and Machine Learning in Testing
Artificial Intelligence (AI): The simulation of human intelligence in machines, enabling them to perform tasks like reasoning, learning, and problem-solving.
Machine Learning (ML): A subset of AI that allows systems to learn and improve from experience without explicit programming.
When applied to Selenium testing, AI and ML enable automated test scripts to adapt to changes, predict outcomes, and enhance decision-making processes.
Challenges in Traditional Selenium Testing
While Selenium is a powerful tool, traditional testing methods face several challenges:
Dynamic Web Elements: Modern web applications frequently use dynamic elements, making locators brittle and prone to failure.
High Maintenance: Frequent application updates require constant updates to test scripts.
Limited Test Coverage: Manually writing scripts for edge cases is time-intensive and error-prone.
Debugging Complex Scenarios: Debugging errors in lengthy test scripts can be tedious.
Data Handling: Handling large volumes of test data efficiently is often challenging.
AI and ML are designed to address these issues, making automation more intelligent and adaptive.
How AI and ML Enhance Selenium Testing
1. Self-Healing Tests
AI-powered frameworks can detect changes in the application’s UI and automatically update locators, reducing test failures caused by dynamic elements.
Example: AI identifies changes in button attributes (e.g., id, class) and adapts the XPath or CSS selectors dynamically.
Code Example:from selenium.webdriver.common.by import By
from selenium.webdriver.support.ui import WebDriverWait
from selenium.webdriver.support import expected_conditions as EC
def self_healing_test(driver, locator_type, locator_value):
try:
element = WebDriverWait(driver, 10).until(
EC.presence_of_element_located((locator_type, locator_value))
)
return element
except Exception as e:
print(“Locator needs adjustment”, e)
# AI adjustment logic can be implemented here
2. Predictive Analytics
ML algorithms analyze historical test data to predict potential failures or high-risk areas in the application.
Example: Identifying modules with higher bug recurrence rates for targeted testing.
3. Smart Test Case Prioritization
AI algorithms prioritize test cases based on factors like code changes, user behavior, and defect history.
Benefit: Focus on high-risk areas first, optimizing testing efforts.
Code Example:from sklearn.ensemble import RandomForestClassifier
import pandas as pd
# Sample dataset with test case details
data = pd.DataFrame({
‘test_case_id’: [1, 2, 3, 4],
‘recent_failures’: [3, 0, 1, 2],
‘execution_time’: [5, 2, 3, 4],
‘priority_score’: [0, 0, 0, 0]
})
# ML model to predict priority
model = RandomForestClassifier()
data[‘priority_score’] = model.predict(data[[‘recent_failures’, ‘execution_time’]])
data = data.sort_values(by=’priority_score’, ascending=False)
print(data)
4. Enhanced Test Coverage
AI generates additional test cases by analyzing user behavior, covering edge cases that may not have been considered.
5. Visual Regression Testing
AI compares screenshots of application versions to identify visual discrepancies, ensuring UI consistency.
Code Example:from PIL import ImageChops, Image
def compare_images(image1_path, image2_path):
img1 = Image.open(image1_path)
img2 = Image.open(image2_path)
diff = ImageChops.difference(img1, img2)
if diff.getbbox():
diff.show()
else:
print(“Images are identical”)
6. Natural Language Processing (NLP)
NLP-powered tools enable writing test cases in plain English, bridging the gap between technical and non-technical stakeholders.
Popular AI-Powered Tools for Selenium Testing
Testim
Features self-healing capabilities and AI-driven insights.
Simplifies test creation with a visual interface.
Applitools
Specializes in visual testing and visual AI.
Provides automated layout checks for responsive design.
Mabl
Combines Selenium with ML to create adaptive and reliable tests.
Focuses on continuous testing.
Functionize
AI-based automation testing tool with NLP capabilities.
Creates codeless tests from natural language instructions.
Sauce Labs
Offers AI-enhanced analytics for test performance and issue identification.
Use Cases of AI and ML in Selenium Testing
1. E-Commerce Testing
Automating cart workflows, payment gateways, and personalized recommendations.
Visual regression testing for product display consistency.
2. Healthcare Applications
Validating dynamic forms and user flows.
Ensuring compliance with regulatory standards like HIPAA.
3. Banking and Financial Systems
Testing multi-factor authentication workflows.
Predictive analytics for risk-based testing.
4. Social Media Platforms
Ensuring seamless user interaction across various browsers and devices.
Testing dynamic and personalized content feeds.
5. IoT and Smart Devices
Validating web interfaces controlling IoT devices.
Testing integrations with voice assistants using NLP.
Benefits of AI and ML in Selenium Testing
Reduced Maintenance Effort: Self-healing capabilities minimize the need for manual intervention in script updates.
Faster Test Execution: Intelligent prioritization and optimization save time.
Enhanced Accuracy: AI-driven locators and insights reduce false positives and negatives.
Broader Test Coverage: Generates edge cases and automates complex workflows.
Improved ROI: Faster releases with fewer bugs increase the return on investment in testing.
Future of AI and ML in Selenium Testing
The integration of AI and ML in Selenium is still evolving, but the possibilities are immense:
Fully Autonomous Testing: Test scripts that generate, execute, and adapt without human intervention.
Real-Time Learning: Systems that learn from live user data to improve test cases continuously.
Cross-Domain Applications: Expanded use cases in AR/VR, blockchain, and IoT testing.
Codeless Automation: More robust and intuitive tools for non-technical testers.
AI-Driven Reporting: Detailed insights into application health and testing efficiency.
Conclusion
AI and ML are revolutionizing Selenium testing, making it smarter, faster, and more reliable. By integrating AI-powered tools and frameworks, organizations can overcome traditional testing challenges, achieve higher accuracy, and accelerate software delivery cycles. As the technology evolves, the future of Selenium testing looks brighter than ever, with AI and ML leading the way.
Ready to embrace AI in your Selenium testing? Start exploring these innovations and transform your automation strategy today!
Keywords: Selenium, AI in testing, machine learning in Selenium, self-healing tests, automation testing, AI-powered tools for Selenium, intelligent test automation.
Behavior-Driven Development (BDD) is a methodology that bridges the gap between business and technical teams by emphasizing collaboration. It uses plain language to define application behavior, making it easier for non-technical stakeholders to contribute to the development process. Selenium and Cucumber are widely used together in BDD to automate web application testing.
This blog provides a detailed guide to implementing BDD using Selenium and Cucumber, including coding examples to help you get started.
What is BDD?
BDD focuses on the behavior of an application from the end user’s perspective. It uses scenarios written in Gherkin, a domain-specific language with a simple syntax:
Given: Precondition or context.
When: Action or event.
Then: Outcome or result.
Example:Feature: Login Functionality
Scenario: Valid user logs in successfully
Given the user is on the login page
When the user enters valid credentials
Then the user is redirected to the dashboard
Tools Used
Selenium: Automates web browsers to test web applications.
Cucumber: Enables writing tests in plain English (Gherkin syntax).
Java: Programming language for writing test automation scripts.
JUnit/TestNG: Test framework to execute Cucumber tests.
Setting Up Your Project
Create a Maven Project:
Add dependencies in pom.xml:<dependencies>
<dependency>
<groupId>io.cucumber</groupId>
<artifactId>cucumber-java</artifactId>
<version>7.11.0</version>
</dependency>
<dependency>
<groupId>io.cucumber</groupId>
<artifactId>cucumber-junit</artifactId>
<version>7.11.0</version>
</dependency>
<dependency>
<groupId>org.seleniumhq.selenium</groupId>
<artifactId>selenium-java</artifactId>
<version>4.10.0</version>
</dependency>
</dependencies>
Directory Structure:
src/test/java: For step definitions.
src/test/resources: For feature files.
Writing a Feature File
Save this file as login.feature in src/test/resources/features:Feature: Login Functionality
Scenario: Valid user logs in successfully
Given the user is on the login page
When the user enters valid credentials
Then the user is redirected to the dashboard
Scenario: Invalid user cannot log in
Given the user is on the login page
When the user enters invalid credentials
Then an error message is displayed
Creating Step Definitions
Create a Java file LoginSteps.java in src/test/java/stepdefinitions:package stepdefinitions;
import org.openqa.selenium.By;
import org.openqa.selenium.WebDriver;
import org.openqa.selenium.WebElement;
import org.openqa.selenium.chrome.ChromeDriver;
import io.cucumber.java.en.*;
public class LoginSteps {
WebDriver driver;
@Given(“the user is on the login page”)
public void userIsOnLoginPage() {
System.setProperty(“webdriver.chrome.driver”, “path_to_chromedriver”);
driver = new ChromeDriver();
driver.get(“https://example.com/login”);
}
@When(“the user enters valid credentials”)
public void userEntersValidCredentials() {
WebElement username = driver.findElement(By.id(“username”));
WebElement password = driver.findElement(By.id(“password”));
WebElement loginButton = driver.findElement(By.id(“login”));
username.sendKeys(“validUser”);
password.sendKeys(“validPassword”);
loginButton.click();
}
@Then(“the user is redirected to the dashboard”)
public void userIsRedirectedToDashboard() {
String expectedUrl = “https://example.com/dashboard”;
assert driver.getCurrentUrl().equals(expectedUrl);
driver.quit();
}
@When(“the user enters invalid credentials”)
public void userEntersInvalidCredentials() {
WebElement username = driver.findElement(By.id(“username”));
WebElement password = driver.findElement(By.id(“password”));
WebElement loginButton = driver.findElement(By.id(“login”));
username.sendKeys(“invalidUser”);
password.sendKeys(“invalidPassword”);
loginButton.click();
}
@Then(“an error message is displayed”)
public void errorMessageIsDisplayed() {
WebElement error = driver.findElement(By.id(“error”));
assert error.isDisplayed();
driver.quit();
}
}
Configuring the Runner Class
Create a Java file TestRunner.java in src/test/java/runners:package runners;
import org.junit.runner.RunWith;
import io.cucumber.junit.Cucumber;
import io.cucumber.junit.CucumberOptions;
@RunWith(Cucumber.class)
@CucumberOptions(
features = “src/test/resources/features”,
glue = “stepdefinitions”,
plugin = {“pretty”, “html:target/cucumber-reports”},
monochrome = true
)
public class TestRunner {
}
Running Your Tests
Open a terminal.
Navigate to your project directory.
Run the following command:mvn test
This will execute all scenarios defined in the login.feature file.
Best Practices for BDD with Selenium and Cucumber
Keep Scenarios Simple: Use concise and descriptive steps in Gherkin.
Reuse Step Definitions: Avoid duplicating code by reusing steps where possible.
Parameterize Steps: Handle multiple inputs by parameterizing your Gherkin steps.
Organize Files: Maintain a clear structure for features, steps, and configurations.
Continuous Integration: Integrate Cucumber tests with CI/CD pipelines for automated execution.
Conclusion
BDD with Selenium and Cucumber is a powerful combination for creating readable, maintainable, and effective test automation suites. By leveraging this approach, teams can foster collaboration, improve test coverage, and ensure high-quality software delivery. Start implementing BDD in your projects today and experience its benefits firsthand!
Keywords: BDD, Selenium, Cucumber, Automation Testing, Behavior-Driven Development, Gherkin, Step Definitions, Test Automation Framework.
If software projects still followed a “code everything first, test at the end” model, modern teams would be drowning in last-minute bugs, missed launch dates, and emergency hot-fixes. Customers have little patience for broken features, and competitors ship improvements weekly sometimes daily. To keep pace, engineering leaders have embraced Shift Left Testing: moving software testing
The post Shift Left Testing Principles: Catch Bugs Early, Deliver Faster appeared first on Codoid.
Data-driven testing is a robust testing methodology that focuses on testing the functionality of an application using multiple sets of data. Instead of hardcoding input values and expected results, this approach separates test logic from the test data, enhancing reusability and maintainability. Selenium, being a popular automation tool, supports data-driven testing seamlessly when integrated with testing frameworks like TestNG or JUnit.
In this blog, we’ll delve into the concept of data-driven testing, explore its benefits, and demonstrate how to implement it using Selenium with detailed coding examples.
What is Data-Driven Testing?
Data-driven testing involves executing test scripts multiple times with different sets of input data. The test data is typically stored in external sources such as:
Excel files
CSV files
Databases
JSON or XML files
This approach is particularly useful for validating applications where the same functionality needs to be tested with various input combinations.
Benefits of Data-Driven Testing
Reusability: Test scripts are reusable for different data sets.
Maintainability: Test logic is separated from test data, making maintenance easier.
Scalability: Allows extensive test coverage with diverse data.
Efficiency: Reduces redundancy in writing test scripts.
Tools Required
Selenium WebDriver: For browser automation.
Apache POI: To read/write data from Excel files.
TestNG/JUnit: For test execution and data provider functionality.
Setting Up Your Project
Add Dependencies
Include the following dependencies in your pom.xml if you’re using Maven:<dependencies>
<dependency>
<groupId>org.seleniumhq.selenium</groupId>
<artifactId>selenium-java</artifactId>
<version>4.10.0</version>
</dependency>
<dependency>
<groupId>org.apache.poi</groupId>
<artifactId>poi</artifactId>
<version>5.2.3</version>
</dependency>
<dependency>
<groupId>org.apache.poi</groupId>
<artifactId>poi-ooxml</artifactId>
<version>5.2.3</version>
</dependency>
<dependency>
<groupId>org.testng</groupId>
<artifactId>testng</artifactId>
<version>7.8.0</version>
</dependency>
</dependencies>
Code Example: Data-Driven Testing Using Excel and TestNG
Step 1: Create the Test Data
Create an Excel file named TestData.xlsx with the following columns:
Username
Password
user1
pass1
user2
pass2
Save this file in the project directory.
Step 2: Utility Class to Read Excel Data
Create a utility class ExcelUtils.java:import java.io.FileInputStream;
import java.io.IOException;
import org.apache.poi.ss.usermodel.*;
public class ExcelUtils {
private static Workbook workbook;
private static Sheet sheet;
public static void loadExcel(String filePath) throws IOException {
FileInputStream fis = new FileInputStream(filePath);
workbook = WorkbookFactory.create(fis);
}
public static String getCellData(int row, int column) {
sheet = workbook.getSheetAt(0);
Row rowData = sheet.getRow(row);
Cell cell = rowData.getCell(column);
return cell.toString();
}
public static int getRowCount() {
return sheet.getLastRowNum();
}
}
Step 3: Test Class with Data Provider
Create a test class LoginTest.java:import org.openqa.selenium.By;
import org.openqa.selenium.WebDriver;
import org.openqa.selenium.WebElement;
import org.openqa.selenium.chrome.ChromeDriver;
import org.testng.annotations.*;
public class LoginTest {
WebDriver driver;
@BeforeClass
public void setup() {
System.setProperty(“webdriver.chrome.driver”, “path_to_chromedriver”);
driver = new ChromeDriver();
driver.get(“https://example.com/login”);
}
@DataProvider(name = “loginData”)
public Object[][] loginData() throws Exception {
ExcelUtils.loadExcel(“TestData.xlsx”);
int rowCount = ExcelUtils.getRowCount();
Object[][] data = new Object[rowCount][2];
for (int i = 1; i <= rowCount; i++) {
data[i – 1][0] = ExcelUtils.getCellData(i, 0);
data[i – 1][1] = ExcelUtils.getCellData(i, 1);
}
return data;
}
@Test(dataProvider = “loginData”)
public void testLogin(String username, String password) {
WebElement usernameField = driver.findElement(By.id(“username”));
WebElement passwordField = driver.findElement(By.id(“password”));
WebElement loginButton = driver.findElement(By.id(“login”));
usernameField.sendKeys(username);
passwordField.sendKeys(password);
loginButton.click();
// Add assertions here to verify login success or failure
}
@AfterClass
public void teardown() {
driver.quit();
}
}
Best Practices for Data-Driven Testing
Use External Data: Store test data in external files to reduce script changes.
Parameterize Test Cases: Avoid hardcoding data in test scripts.
Error Handling: Implement robust error handling for file operations.
Optimize Performance: Load test data only once if possible.
Clear Test Data: Ensure the test environment is reset before each run.
Advantages of Data-Driven Testing with Selenium
Flexibility: Easily test multiple scenarios by changing input data.
Enhanced Coverage: Test edge cases by providing varied data sets.
Reduced Redundancy: Write fewer scripts for multiple test cases.
Conclusion
Data-driven testing is a vital strategy for efficient and thorough test automation. By combining Selenium with tools like Apache POI and TestNG, you can create scalable and maintainable test suites that cover a wide range of scenarios. Implement this approach to enhance your testing process and ensure high-quality software delivery.
Keywords: Data-Driven Testing, Selenium, TestNG, Apache POI, Automation Testing, Excel Integration, Test Automation Framework.
API testing has become an integral part of software quality assurance. Automating REST APIs ensures the robustness and reliability of web applications by validating backend functionality. In this blog, we will explore how Selenium and Postman can be used to automate REST APIs, providing both flexibility and scalability in your testing processes.
Why Automate REST APIs?
Automating REST APIs brings several benefits, including:
Speed: Automated tests execute faster compared to manual testing.
Accuracy: Minimizes human error in repetitive tasks.
Efficiency: Allows simultaneous testing of multiple endpoints.
Integration: Fits seamlessly into CI/CD pipelines.
Key Concepts in REST API Automation
Before diving into automation, let’s understand some key concepts:
API Endpoint: A URL that specifies where an API resource is located.
HTTP Methods: Common methods include GET, POST, PUT, DELETE.
Status Codes: Responses like 200 (OK), 404 (Not Found), 500 (Server Error).
Request Payload: The data sent with a request, often in JSON format.
Response: Data received from the server, including status and body.
Tools Overview: Selenium and Postman
Selenium: Best suited for UI testing but can complement API testing by validating front-end integration with APIs.
Postman: A powerful API testing tool that supports request creation, test scripting, and automation through Newman CLI.
Practical Applications of API Testing
Authentication: Validating login and token-based authentication mechanisms.
Data Integrity: Ensuring the correctness of data returned by APIs.
Error Handling: Checking proper error messages and status codes.
Load Testing: Simulating multiple users accessing APIs simultaneously.
Setting Up Selenium and Postman for API Automation
1. Installing Selenium
Ensure you have Java and Maven installed. Add Selenium dependencies to your pom.xml:<dependency>
<groupId>org.seleniumhq.selenium</groupId>
<artifactId>selenium-java</artifactId>
<version>4.10.0</version>
</dependency>2. Installing Postman
Download Postman from Postman’s official website. For automation, install Newman:
npm install -g newman
Coding Examples: Automating REST APIs with Selenium and Postman
Example 1: Sending API Requests Using Java (RestAssured Library)import io.restassured.RestAssured;
import io.restassured.response.Response;
public class ApiTest {
public static void main(String[] args) {
RestAssured.baseURI = “https://jsonplaceholder.typicode.com”;
// GET Request
Response response = RestAssured.given().get(“/posts/1”);
System.out.println(“Status Code: ” + response.getStatusCode());
System.out.println(“Response Body: ” + response.getBody().asString());
// Assert Status Code
assert response.getStatusCode() == 200;
}
}
Example 2: Running Postman Collections via Newman
Export your Postman collection as a JSON file.
Use Newman CLI to execute the collection:newman run my-collection.json
Example 3: Integrating Selenium with API Responses
This example demonstrates how to combine API testing with UI testing by validating that the data returned from an API call is correctly displayed on a web application’s UI. Here’s a breakdown of the code:import org.openqa.selenium.By;
import org.openqa.selenium.WebDriver;
import org.openqa.selenium.WebElement;
import org.openqa.selenium.chrome.ChromeDriver;
import io.restassured.RestAssured;
public class SeleniumApiIntegration {
public static void main(String[] args) {
// API Call
RestAssured.baseURI = “https://api.example.com”;
String apiData = RestAssured.given().get(“/data”).getBody().asString();
// Selenium Test
WebDriver driver = new ChromeDriver();
driver.get(“https://example.com”);
WebElement element = driver.findElement(By.id(“apiDataField”));
assert element.getText().equals(apiData);
driver.quit();
}
}
1. API Call with RestAssured
The first step involves using RestAssured to interact with the API. A base URL is set, and a GET request is sent to a specific endpoint. The response body is retrieved as a string, which will later be compared with the data displayed on the web page.
2. Selenium Test
The Selenium WebDriver is initialized to open the browser and navigate to the target URL. This ensures that the web page containing the UI element to be validated is loaded and ready for interaction.
3. Finding the Web Element
A specific element on the web page is located using a unique identifier (like an ID attribute). This UI element is expected to display the same data that was fetched from the API.
4. Validating the Data
The text content of the located UI element is retrieved and compared with the API response. If the values match, the test passes, indicating consistency between the API and UI. If they don’t match, it signals a potential bug or data discrepancy.
5. Closing the Browser
Finally, the browser session is terminated to ensure no resources are left open after the test execution.
Use Case
This approach is used to verify the consistency of data between the backend (API response) and the frontend (UI). For example:
Validating that product details provided by an API, such as name or price, are displayed accurately on a webpage.
Benefits
End-to-End Testing: Ensures seamless integration between the backend and frontend.
Early Bug Detection: Detects mismatches between API and UI during testing phases.
Reusable: Can be extended to validate multiple API endpoints and corresponding UI elements.
Step-by-Step Guide to Automate API Testing
Understand API Requirements: Review API documentation to understand endpoints, methods, and payloads.
Create Test Cases: Identify scenarios such as response validation, status codes, and data formats.
Use Postman for Initial Testing: Verify API responses manually.
Automate with Java: Use RestAssured or HttpClient libraries for scripting.
Integrate with Selenium: Combine API data validation with UI testing.
Leverage CI/CD: Incorporate automated tests into Jenkins or GitHub Actions.
Conclusion
By integrating Selenium and Postman, you can create a comprehensive automation suite that tests APIs and ensures seamless integration between backend and frontend systems. API testing not only improves the reliability of web applications but also accelerates the development cycle, allowing teams to deliver high-quality products efficiently.
CTA: Have questions about API testing with Selenium and Postman? Share them in the comments below!
Roundcube: CVE-2025–49113
Roundcube: CVE-2025–49113Who am I?I’m Chetan Chinchulkar (aka omnipresent), a cybersecurity enthusiast, software developer, and security researcher ranked in the top 2% on TryHackMe. Passionate about …
Read more
Published Date:
Jun 19, 2025 (4 hours, 16 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-23121 Critical Veeam Vulnerability: Backup Servers at Risk from Authenticated RCE Flaw
Hunter.howWhat is CVE‑2025-23121?This vulnerability is a critical Remote Code Execution (RCE) flaw in Veeam Backup & Replication, rated 9.9 out of 10 on the CVSS v3 scale. It allows an authenticated d …
Read more
Published Date:
Jun 19, 2025 (4 hours, 12 minutes ago)
Vulnerabilities has been mentioned in this article.
Meta Embraces Passkeys: Facebook & Messenger Get Secure, Passwordless Login
As more online service platforms adopt Passkey technology, Meta has finally followed suit, announcing the introduction of a more secure and convenient login method for both Facebook and Messenger—aime …
Read more
Published Date:
Jun 19, 2025 (2 hours, 20 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-27920
Open Next for Cloudflare SSRF Vulnerability Let Attackers Load Remote Resources from Arbitrary Hosts
A high-severity Server-Side Request Forgery (SSRF) vulnerability has been identified in the @opennextjs/cloudflare package, enabling attackers to exploit the /_next/image endpoint to load remote resou …
Read more
Published Date:
Jun 19, 2025 (1 hour, 49 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-6087
Apache Traffic Server Vulnerability Let Attackers Trigger DoS Attack via Memory Exhaustion
A critical security vulnerability has been discovered in Apache Traffic Server that allows remote attackers to trigger denial-of-service (DoS) attacks through memory exhaustion.
The vulnerability, tra …
Read more
Published Date:
Jun 19, 2025 (1 hour, 46 minutes ago)
Vulnerabilities has been mentioned in this article.
Cisco AnyConnect VPN Server Vulnerability Let Attackers Trigger DoS Attack
A critical security vulnerability affecting Cisco Meraki MX and Z Series devices could allow unauthenticated attackers to launch denial of service (DoS) attacks against AnyConnect VPN services.
The vu …
Read more
Published Date:
Jun 19, 2025 (1 hour, 20 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-20271
CVE ID : CVE-2025-5490
Published : June 19, 2025, 6:15 a.m. | 4 hours, 21 minutes ago
Description : The Football Pool plugin for WordPress is vulnerable to Stored Cross-Site Scripting via admin settings in all versions up to, and including, 2.12.4 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with administrator-level permissions and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. This only affects multi-site installations and installations where unfiltered_html has been disabled.
Severity: 5.5 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4571
Published : June 19, 2025, 7:15 a.m. | 3 hours, 21 minutes ago
Description : The GiveWP – Donation Plugin and Fundraising Platform plugin for WordPress is vulnerable to unauthorized view and modification of data due to an insufficient capability check on the permissionsCheck functions in all versions up to, and including, 4.3.0. This makes it possible for authenticated attackers, with Contributor-level access and above, to view or delete fundraising campaigns, view donors’ data, modify campaign events, etc.
Severity: 5.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4965
Published : June 19, 2025, 7:15 a.m. | 3 hours, 21 minutes ago
Description : The WPBakery Page Builder for WordPress plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin’s Grid Builder feature in all versions up to, and including, 8.4.1 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with author-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Severity: 6.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2016-3399
Published : June 19, 2025, 9:15 a.m. | 1 hour, 21 minutes ago
Description : Rejected reason: This CVE ID has been rejected or withdrawn by its CVE Numbering Authority.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-31698
Published : June 19, 2025, 10:15 a.m. | 21 minutes ago
Description : ACL configured in ip_allow.config or remap.config does not use IP addresses that are provided by PROXY protocol.
Users can use a new setting (proxy.config.acl.subjects) to choose which IP addresses to use for the ACL if Apache Traffic Server is configured to accept PROXY protocol.
This issue affects undefined: from 10.0.0 through 10.0.6, from 9.0.0 through 9.2.10.
Users are recommended to upgrade to version 9.2.11 or 10.0.6, which fixes the issue.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-49763
Published : June 19, 2025, 10:15 a.m. | 21 minutes ago
Description : ESI plugin does not have the limit for maximum inclusion depth, and that allows excessive memory consumption if malicious instructions are inserted.
Users can use a new setting for the plugin (–max-inclusion-depth) to limit it.
This issue affects Apache Traffic Server: from 10.0.0 through 10.0.5, from 9.0.0 through 9.2.10.
Users are recommended to upgrade to version 9.2.11 or 10.0.6, which fixes the issue.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…