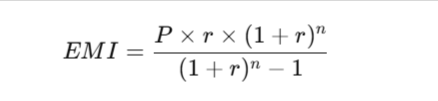A security weakness has been disclosed in the artificial intelligence (AI)-powered code editor Cursor that could trigger code execution when…
Development
UEFI copycat of Petya/NotPetya exploiting CVE-2024-7344 discovered on VirusTotal Source: Read More
The U.S. Federal Bureau of Investigation (FBI) has issued a flash alert to release indicators of compromise (IoCs) associated with…
When large language models like ChatGPT first became widely available, a lot of us developers felt like we’d been handed…
When users interact with a website or application, the first thing they notice isn’t the code. Instead, it’s the design…
For this week’s interview, we’ve got a special treat. Quincy Larson talking with two legends in the self-taught developer community.…
If you’ve ever used Google Translate, skimmed through a quick summary, or asked a chatbot for help, then you’ve definitely…
Drawing from over a decade of experience in digital marketing, where I’ve helped countless businesses boost their customer base through…
Chapter 1 My name is Danny Marsh, and I’m here to tell you the most terrifying story of my life.…
The power grid had been failing for three days straight, but tonight felt different. It wasn’t the oppressive silence of…
The Mind That Defies All Logic: Meet the Real-Life Neo from The Matrix What if I told you that somewhere…
Learning from PHP Log to File Example By van Gato Logging is a common activity that most applications must perform…
In this tutorial, we will learn how to create an EMI calculator Project using PHP. How Online EMI Calculator works:…
#752 — September 12, 2025 Read on the Web If you have any interest in music and being able to…
The financial services industry stands at the edge of the largest wealth transfer in history. Over the coming decades, an…
The financial services industry is undergoing significant change. While there’s real opportunity for growth and innovation, firms also face tough…
Over half of insider cyber incidents in UK schools are being caused by students—a trend raising alarms across education, regulation,…
The U.S. Federal Trade Commission has opened a formal inquiry into AI chatbots that act like companions—designed to mimic emotions,…
The security landscape for cloud-native applications is undergoing a profound transformation. Containers, Kubernetes, and serverless technologies are now the default…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a critical security flaw impacting Dassault Systèmes DELMIA Apriso…


![Playing the Developer Job Search Game to Win in 2025 with Danny Thompson & Leon Noel [Podcast #188]](https://devstacktips.com/wp-content/uploads/2025/09/bcea7147-b14c-4093-8d15-5c2115bd8c8d-aPnXJP-450x253.png)