Kettering Health, a major healthcare provider in Ohio, is currently facing a widespread technology outage due to a cybersecurity incident…
Development
It takes just one email to compromise an entire system. A single well-crafted message can bypass filters, trick employees, and…
Continuous Integration and Continuous Delivery/Deployment (CI/CD) refers to practices that automate how code is developed and released to different environments.…
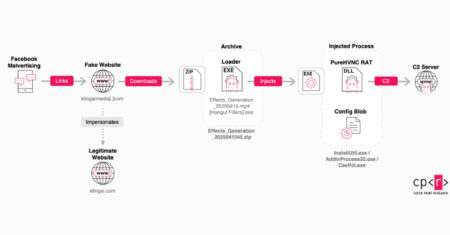
Counterfeit Facebook pages and sponsored ads on the social media platform are being employed to direct users to fake websites…
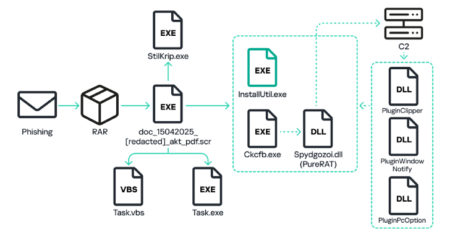
Russian organizations have become the target of a phishing campaign that distributes malware called PureRAT, according to new findings from…
Agent Development Kit (ADK) is an open-source Python framework that helps developers build, manage, and deploy multi-agent systems. It’s designed…
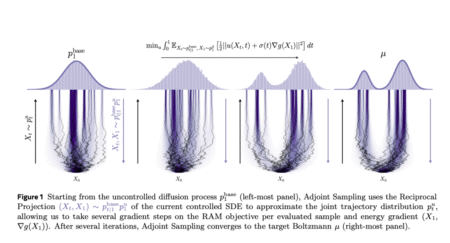
Data Scarcity in Generative Modeling Generative models traditionally rely on large, high-quality datasets to produce samples that replicate the underlying…
Setting up and tearing down test environments can be a repetitive and error-prone process in end-to-end testing. This is especially true when dealing with complex workflows or multiple test configurations. Enter Playwright Fixtures a built-in feature of Playwright Test that allows testers to define modular, reusable, and maintainable setup and teardown logic. Fixtures streamline your
The post Playwright Fixtures in Action : Create Reusable and Maintainable Tests appeared first on Codoid.
The static ClipboardItem.supports() function to determine support for a given MIME type is now part of Baseline. Source: web.dev: BlogÂ
Iterator helpers became Baseline Newly available as of March 31, 2025. Source: web.dev: BlogÂ
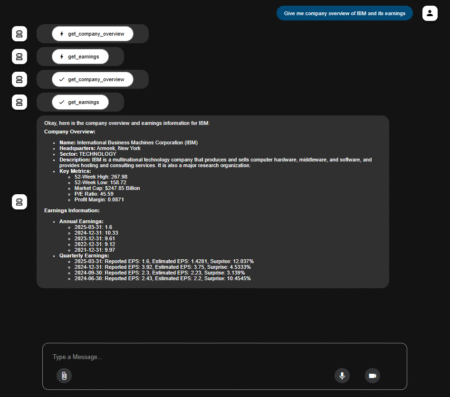
If you’re building conversational AI and tired of messy logic or hard-to-scale workflows, LangGraph makes it easier. It uses graphs…
Introducing Veo 3 and Imagen 4, and a new tool for filmmaking called Flow. Source: Read MoreÂ
Gemini 2.5 Pro continues to be loved by developers as the best model for coding, and 2.5 Flash is getting…
We’ve made Gemini 2.5 our most secure model family to date. Source: Read MoreÂ
We’re extending Gemini to become a world model that can make plans and imagine new experiences by simulating aspects of…
Learn about the new SynthID Detector portal we announced at I/O to help people understand how the content they see…
Gemma 3n is a cutting-edge open model designed for fast, multimodal AI on devices, featuring optimized performance, unique flexibility with…
The HCL Commerce v9.1 release saw major changes in features, functionality, and technology. This blog series will focus on each…
In episode 51 of The AI Fix, a Greek man’s marriage is destroyed after ChatGPT reads his coffee, a woman…
An unknown threat actor has been attributed to creating several malicious Chrome Browser extensions since February 2024 that masquerade as…