Chaotic systems, such as fluid dynamics or brain activity, are highly sensitive to initial conditions, making long-term predictions difficult. Even…
Development
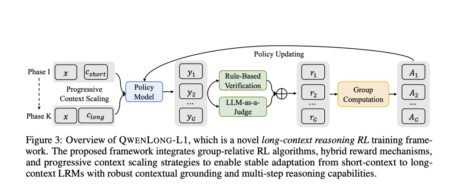
While large reasoning models (LRMs) have shown impressive capabilities in short-context reasoning through reinforcement learning (RL), these gains do not…
This blog discusses how voice AI and conversational interfaces transform insurance by enabling faster, more personalized customer interactions. From claim filing to 24/7 support, these tools enhance customer satisfaction and reduce operational burdens.
The post Voice AI and Conversational Interfaces: The Next Frontier in Insurance CX first appeared on TestingXperts.
Neural networks have long been powerful tools for handling complex data-driven tasks. Still, they often struggle to make discrete decisions…
Top News The 15 biggest announcements at Google I/O 2025 Google’s I/O 2025 conference included a ton of exciting new…
Latest PEAR Releases: Crypt_GPG 1.6.11 Source: Read MoreÂ
Laravel’s existsOr method enables elegant handling of non-existent model queries by executing closures when no results are found. This feature…
Volet is an extensible customer feedback widget for Laravel The post Volet is a Customer Feedback Widget for Laravel appeared…
Five major banking associations have formally petitioned the U.S. Securities and Exchange Commission (SEC) to repeal a rule that mandates…
Cyber threats don’t show up one at a time anymore. They’re layered, planned, and often stay hidden until it’s too…
Are your web privacy controls protecting your users, or just a box-ticking exercise? This CISO’s guide provides a practical roadmap…
Nova Scotia Power has confirmed it was the victim of a ransomware attack, weeks after initially alerting customers to a…
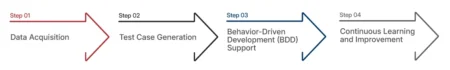
Tx-GPT is an in-house AI Agent by Txlabs that up-scales software testing by converting user stories into detailed, actionable test cases. Designed for QA modernization, it enhances test coverage, automates repetitive tasks, and integrates seamlessly with ALM tools like Azure Test Plans.
The post Tx-GPT: Turning User Stories into QA Action Using AI first appeared on TestingXperts.
The frontiers of artificial intelligence are expanding at a pace that often feels like science fiction becoming reality. At the…
Comments Source: Read MoreÂ
Cybersecurity researchers have disclosed a malware campaign that uses fake software installers masquerading as popular tools like LetsVPN and QQ…
Many websites lack accessible and cost-effective ways to integrate natural language interfaces, making it difficult for users to interact with…
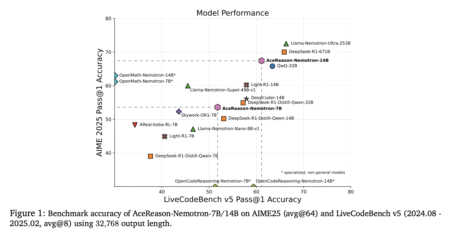
Reasoning capabilities represent a fundamental component of AI systems. The introduction of OpenAI o1 sparked significant interest in building reasoning…
In this tutorial, we will discover how to harness the power of an advanced AI Agent, augmented with both Python…
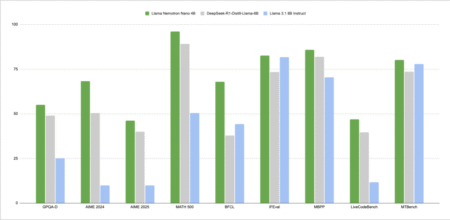
NVIDIA has released Llama Nemotron Nano 4B, an open-source reasoning model designed to deliver strong performance and efficiency across scientific…