While federated learning (FL) and differential privacy (DP) have been extensively studied, their application to automatic speech recognition (ASR) remains…
Development
CVE ID : CVE-2025-7459
Published : July 11, 2025, 9:15 p.m. | 3 hours, 52 minutes ago
Description : A vulnerability classified as critical was found in code-projects Mobile Shop 1.0. This vulnerability affects unknown code of the file /EditMobile.php. The manipulation of the argument ID leads to sql injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7457
Published : July 11, 2025, 9:15 p.m. | 3 hours, 52 minutes ago
Description : A vulnerability, which was classified as critical, was found in Campcodes Online Movie Theater Seat Reservation System 1.0. This affects an unknown part of the file /admin/manage_movie.php. The manipulation of the argument ID leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-53636
Published : July 11, 2025, 10:15 p.m. | 2 hours, 52 minutes ago
Description : Open OnDemand is an open-source HPC portal. Users can flood logs by interacting with the shell app and generating many errors. Users who flood logs can create very large log files causing a Denial of Service (DoS) to the ondemand system. This vulnerability is fixed in 3.1.14 and 4.0.6.
Severity: 5.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7460
Published : July 11, 2025, 10:15 p.m. | 2 hours, 52 minutes ago
Description : A vulnerability has been found in TOTOLINK T6 4.1.5cu.748_B20211015 and classified as critical. Affected by this vulnerability is the function setWiFiAclRules of the file /cgi-bin/cstecgi.cgi of the component HTTP POST Request Handler. The manipulation of the argument mac leads to buffer overflow. The attack can be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5199
Published : July 12, 2025, 12:15 a.m. | 52 minutes ago
Description : In Canonical Multipass up to and including version 1.15.1 on macOS, incorrect default permissions allow a local attacker to escalate privileges by modifying files executed with administrative privileges by a Launch Daemon during system startup.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
On this week’s episode of the podcast, freeCodeCamp founder Quincy Larson interviews Braydon Coyer. He’s a software engineer who started…
Growth happens when people feel heard, supported, and empowered to lead with purpose. That belief shapes our culture at Perficient,…
Abstract In today’s digital-first world, healthcare organizations face increasing pressure to modernize operations and improve service delivery. Intelligent automation is…
The Distribution Strategy Group recently hosted a webinar exploring the future of B2B distribution, bringing together a panel of industry…
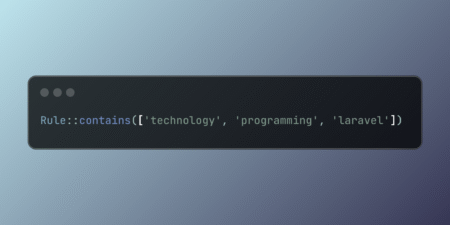
Laravel’s Rule::contains() method provides fluent array validation syntax, replacing string concatenation with clean, readable rules. Maintain consistency with Laravel’s validation…
With PHP 8.5, a new fatal_error_backtraces setting can control whether a backtrace is shown for fatal errors. Learn how this…
Paddy Power and BetFair have warned customers that “an unauthorised third party” gained access to “limited betting account information” relating…
Cybersecurity researchers have discovered a set of four security flaws in OpenSynergy’s BlueSDK Bluetooth stack that, if successfully exploited, could…
A Russian professional basketball player has been arrested for allegedly acting as a negotiator for a ransomware gang… and despite…
Fortinet has released fixes for a critical security flaw impacting FortiWeb that could enable an unauthenticated attacker to run arbitrary…
Apple researchers are advancing AI and ML through fundamental research, and to support the broader research community and help accelerate…
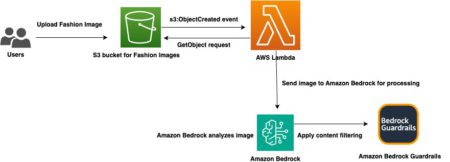
The global fashion industry is estimated to be valued at $1.84 trillion in 2025, accounting for approximately 1.63% of the…
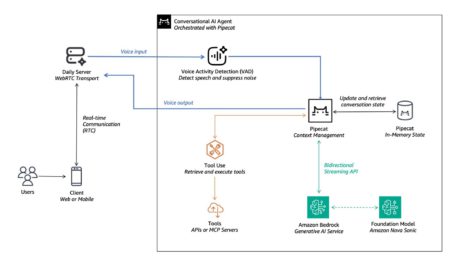
Voice AI is changing the way we use technology, allowing for more natural and intuitive conversations. Meanwhile, advanced AI agents…
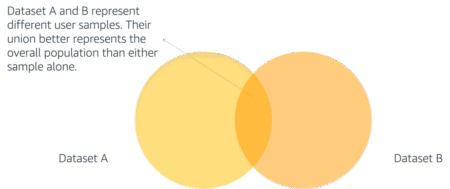
Fraud detection remains a significant challenge in the financial industry, requiring advanced machine learning (ML) techniques to detect fraudulent patterns…
![799 rejections… but he got the job! Braydon Coyer developer interview [Podcast #179]](https://devstacktips.com/wp-content/uploads/2025/07/3b18e2c2-3723-459a-90e2-ef29a2d473c9-MqOPOS-450x253.jpg)