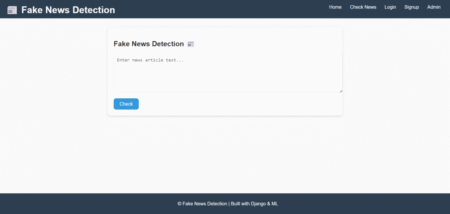
“Fake News Detection System Project using Python ML” is a web-based application aimed at combating the growing challenge of online…
Development
Comments Source: Read MoreÂ
CVE ID : CVE-2024-32832
Published : Aug. 31, 2025, 4:15 a.m. | 23 hours ago
Description : Missing Authorization vulnerability in Hamid Alinia Login with phone number.This issue affects Login with phone number: from n/a through 1.6.93.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-31100
Published : Aug. 31, 2025, 4:15 a.m. | 23 hours ago
Description : Unrestricted Upload of File with Dangerous Type vulnerability in Mojoomla School Management allows Upload a Web Shell to a Web Server.This issue affects School Management: from n/a through 1.93.1 (02-07-2025).
Severity: 9.9 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47696
Published : Aug. 31, 2025, 4:15 a.m. | 23 hours ago
Description : Improper Control of Filename for Include/Require Statement in PHP Program (‘PHP Remote File Inclusion’) vulnerability in Solwin Blog Designer PRO.This issue affects Blog Designer PRO: from n/a through 3.4.7.
Severity: 8.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9727
Published : Aug. 31, 2025, 12:15 p.m. | 13 hours, 12 minutes ago
Description : A weakness has been identified in D-Link DIR-816L 206b01. Affected by this issue is the function soapcgi_main of the file /soap.cgi. This manipulation of the argument service causes os command injection. Remote exploitation of the attack is possible. The exploit has been made available to the public and could be exploited. This vulnerability only affects products that are no longer supported by the maintainer.
Severity: 6.5 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9728
Published : Aug. 31, 2025, 12:15 p.m. | 13 hours, 12 minutes ago
Description : A security vulnerability has been detected in givanz Vvveb 1.0.7.2. This affects an unknown part of the file app/template/user/login.tpl. Such manipulation of the argument Email/Password leads to cross site scripting. The attack can be executed remotely. The name of the patch is bbd4c42c66ab818142240348173a669d1d2537fe. Applying a patch is advised to resolve this issue.
Severity: 5.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9729
Published : Aug. 31, 2025, 1:15 p.m. | 12 hours, 12 minutes ago
Description : A vulnerability was detected in PHPGurukul Online Course Registration 3.1. This vulnerability affects unknown code of the file /admin/student-registration.php. Performing manipulation of the argument studentname results in sql injection. The attack is possible to be carried out remotely. The exploit is now public and may be used.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9730
Published : Aug. 31, 2025, 1:15 p.m. | 12 hours, 12 minutes ago
Description : A vulnerability was found in itsourcecode Apartment Management System 1.0. The affected element is an unknown function of the file /ajax/updateProfile.php. The manipulation of the argument user_id results in sql injection. It is possible to launch the attack remotely. The exploit has been made public and could be used.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9731
Published : Aug. 31, 2025, 2:15 p.m. | 11 hours, 12 minutes ago
Description : A vulnerability was determined in Tenda AC9 15.03.05.19. The impacted element is an unknown function of the file /etc_ro/shadow of the component Administrative Interface. This manipulation causes hard-coded credentials. It is possible to launch the attack on the local host. The attack’s complexity is rated as high. The exploitability is regarded as difficult. The exploit has been publicly disclosed and may be utilized.
Severity: 2.5 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9732
Published : Aug. 31, 2025, 2:15 p.m. | 11 hours, 12 minutes ago
Description : A vulnerability was identified in DCMTK up to 3.6.9. This affects an unknown function in the library dcmimage/include/dcmtk/dcmimage/diybrpxt.h of the component dcm2img. Such manipulation leads to memory corruption. Local access is required to approach this attack. The name of the patch is 7ad81d69b. It is best practice to apply a patch to resolve this issue.
Severity: 5.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9733
Published : Aug. 31, 2025, 3:15 p.m. | 10 hours, 12 minutes ago
Description : A security flaw has been discovered in code-projects Human Resource Integrated System 1.0. This impacts an unknown function of the file /login_timeee.php. Performing manipulation of the argument emp_id results in sql injection. The attack may be initiated remotely. The exploit has been released to the public and may be exploited.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9734
Published : Aug. 31, 2025, 3:15 p.m. | 10 hours, 12 minutes ago
Description : A security flaw has been discovered in O2OA up to 10.0-410. The impacted element is an unknown function of the file /x_query_assemble_designer/jaxrs/stat of the component Personal Profile Page. The manipulation of the argument name/alias/description/applicationName results in cross site scripting. The attack can be launched remotely. The exploit has been released to the public and may be exploited. The vendor replied in the GitHub issue (translated from simplified Chinese): “This issue will be fixed in the new version.”
Severity: 5.1 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9735
Published : Aug. 31, 2025, 4:15 p.m. | 9 hours, 12 minutes ago
Description : A weakness has been identified in O2OA up to 10.0-410. This affects an unknown function of the file /x_query_assemble_designer/jaxrs/table of the component Personal Profile Page. This manipulation of the argument description/applicationName/queryName causes cross site scripting. The attack may be initiated remotely. The exploit has been made available to the public and could be exploited. The vendor replied in the GitHub issue (translated from simplified Chinese): “This issue will be fixed in the new version.”
Severity: 5.1 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9736
Published : Aug. 31, 2025, 4:15 p.m. | 9 hours, 12 minutes ago
Description : A security vulnerability has been detected in O2OA up to 10.0-410. This impacts an unknown function of the file /x_query_assemble_designer/jaxrs/statement of the component Personal Profile Page. Such manipulation of the argument description/queryName leads to cross site scripting. The attack may be launched remotely. The exploit has been disclosed publicly and may be used. The vendor replied in the GitHub issue (translated from simplified Chinese): “This issue will be fixed in the new version.”
Severity: 5.1 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9737
Published : Aug. 31, 2025, 5:15 p.m. | 8 hours, 12 minutes ago
Description : A vulnerability was detected in O2OA up to 10.0-410. Affected is an unknown function of the file /x_query_assemble_designer/jaxrs/importmodel of the component Personal Profile Page. Performing manipulation of the argument description/applicationName/queryName results in cross site scripting. Remote exploitation of the attack is possible. The exploit is now public and may be used. The vendor replied in the GitHub issue (translated from simplified Chinese): “This issue will be fixed in the new version.”
Severity: 5.1 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9738
Published : Aug. 31, 2025, 5:15 p.m. | 8 hours, 12 minutes ago
Description : A flaw has been found in Portabilis i-Educar up to 2.10. Affected by this vulnerability is an unknown functionality of the file /intranet/educar_tipo_ensino_cad.php. Executing manipulation of the argument nm_tipo can lead to cross site scripting. The attack can be executed remotely. The exploit has been published and may be used.
Severity: 5.1 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9740
Published : Aug. 31, 2025, 6:15 p.m. | 7 hours, 12 minutes ago
Description : A vulnerability was found in code-projects Human Resource Integrated System 1.0. This affects an unknown part of the file /log_query.php. The manipulation of the argument ID results in sql injection. The attack may be performed from remote. The exploit has been made public and could be used.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9739
Published : Aug. 31, 2025, 6:15 p.m. | 7 hours, 12 minutes ago
Description : A vulnerability has been found in Campcodes Online Water Billing System 1.0. Affected by this issue is some unknown functionality of the file /process.php. The manipulation of the argument Username leads to sql injection. The attack is possible to be carried out remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9741
Published : Aug. 31, 2025, 7:15 p.m. | 6 hours, 12 minutes ago
Description : A vulnerability was determined in code-projects Human Resource Integrated System 1.0. This vulnerability affects unknown code of the file /login_query12.php. This manipulation of the argument ID causes sql injection. It is possible to initiate the attack remotely. The exploit has been publicly disclosed and may be utilized.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…