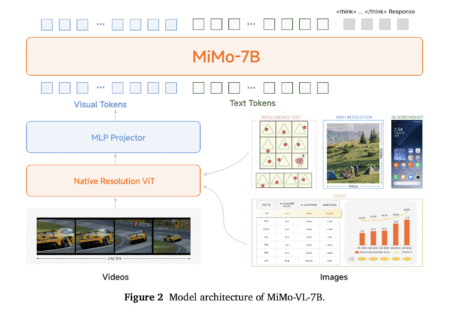
Vision-language models (VLMs) have become foundational components for multimodal AI systems, enabling autonomous agents to understand visual environments, reason over…
Development
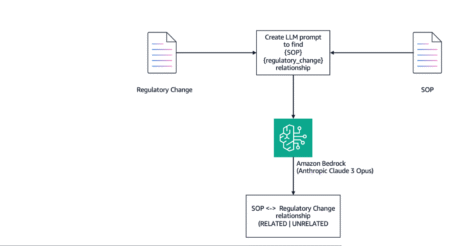
Standard operating procedures (SOPs) are essential documents in the context of regulations and compliance. SOPs outline specific steps for various…
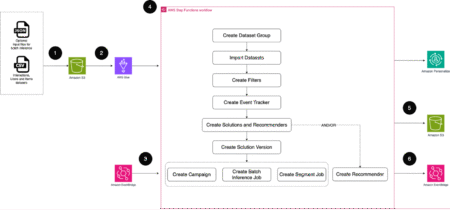
Crafting unique, customized experiences that resonate with customers is a potent strategy for boosting engagement and fostering brand loyalty. However,…
In these days, it is more common to companies adopting AI-first strategy to stay competitive and more efficient. As generative…
In this tutorial, we demonstrate how to leverage ScrapeGraph’s powerful scraping tools in combination with Gemini AI to automate the…
*Equal Contributors Identifying mistakes (i.e., miscues) made while reading aloud is commonly approached post-hoc by comparing automatic speech recognition (ASR)…
⚡ Weekly Recap: APT Intrusions, AI Malware, Zero-Click Exploits, Browser Hijacks and More
Cybersecurity / Hacking News
If this had been a security drill, someone would’ve said it went too far. But it wasn’t a drill—it was real. The access? Everything looked normal. The tools? Easy to find. …
Read more
Published Date:
Jun 02, 2025 (12 hours, 6 minutes ago)
Vulnerabilities has been mentioned in this article.
Exploitation Risk Grows for Critical Cisco Bug
Source: Sergiy Palamarchuk via ShutterstockThe risk of attackers exploiting a recently disclosed maximum severity vulnerability in Cisco’s IOS XE Wireless Controller software has increased significant …
Read more
Published Date:
Jun 02, 2025 (2 hours, 8 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-20188
CVE-2014-2120
Google Fights Back: Appeals Order to Sell Chrome Browser
In response to the U.S. Department of Justice’s directive that Google must divest and sell its Chrome browser business, the company announced its intention to appeal the decision, asserting that the p …
Read more
Published Date:
Jun 02, 2025 (5 hours, 43 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-3619
CVE-2024-10488
CVE-2024-10487
MediaTek Vulnerabilities Let Attackers Escalate Privileges Without User Interaction
Multiple critical security vulnerabilities affecting MediaTek smartphones, tablets, and IoT chipsets could allow attackers to escalate privileges and compromise device security without requiring any u …
Read more
Published Date:
Jun 02, 2025 (3 hours, 57 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-20678
CVE-2025-20677
CVE-2025-20676
CVE-2025-20675
CVE-2025-20674
CVE-2025-20673
CVE-2025-20672
Vulnerabilities in Preinstalled Android Apps Expose PIN Codes and Allow Command Injection
Significant vulnerabilities were uncovered in pre-installed applications on Ulefone and Krüger&Matz Android smartphones that expose users to significant risks, including unauthorized factory resets, P …
Read more
Published Date:
Jun 02, 2025 (3 hours, 43 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2024-13917
CVE-2024-13916
CVE-2024-13915
Critical Bugs Could Spark Takeover of Widely Used Fire Safety OT/ICS Platform
Source: Ivan Kmit via Alamy Stock PhotoTwo critical, unpatched security flaws in technology widely used in operational technology (OT) and industrial control systems (ICS) that monitor fire safety cou …
Read more
Published Date:
Jun 02, 2025 (3 hours, 42 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-46352
CVE-2025-41438
Qualcomm Adreno GPU 0-Day Vulnerabilities Exploited to Attack Android Users
Mobile chipmaker Qualcomm has issued urgent security patches for three critical zero-day vulnerabilities in its Adreno GPU drivers that are actively being exploited in targeted attacks against Android …
Read more
Published Date:
Jun 02, 2025 (3 hours, 3 minutes ago)
Vulnerabilities has been mentioned in this article.
Attackers breached ConnectWise, compromised customer ScreenConnect instances
A suspected “sophisticated nation state actor” has compromised ScreenConnect cloud instances of a “very small number” of ConnectWise customers, the company has revealed on Wednesday.
“We have not obse …
Read more
Published Date:
Jun 02, 2025 (2 hours, 23 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-3935
CVE-2025-30406
CVE-2024-1709
Linux Crash Reporting Flaws (CVE-2025-5054, 4598) Expose Password Hashes
Qualys details CVE-2025-5054 and CVE-2025-4598, critical vulnerabilities affecting Linux crash reporting tools like Apport and systemd-coredump. Learn how to protect your Ubuntu, Red Hat, and Fedora s …
Read more
Published Date:
Jun 02, 2025 (1 hour, 6 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-5054
CVE-2025-4598
CVE-2024-27443
Qualcomm fixes three Adreno GPU zero-days exploited in attacks
Qualcomm has released security patches for three zero-day vulnerabilities in the Adreno Graphics Processing Unit (GPU) driver that impact dozens of chipsets and are actively exploited in targeted atta …
Read more
Published Date:
Jun 02, 2025 (4 hours, 15 minutes ago)
Vulnerabilities has been mentioned in this article.
Qualcomm waarschuwt voor misbruik van GPU-lekken in Androidtelefoons
Chipfabrikant Qualcomm waarschuwt vandaag voor drie actief aangevallen GPU-lekken in Androidtelefoons. De kwetsbaarheden (CVE-2025-21479, CVE-2025-21480 en CVE-2025-27038) bevinden zich in de Adreno G …
Read more
Published Date:
Jun 02, 2025 (3 hours, 16 minutes ago)
Vulnerabilities has been mentioned in this article.
Bluetooth HCI Adaptor Realtek Vulnerability Let Attackers Delete Arbitrary Files
A high-severity vulnerability has been discovered in Realtek’s Bluetooth HCI Adaptor that allows local attackers to delete arbitrary files and potentially escalate privileges on affected systems.
The …
Read more
Published Date:
Jun 02, 2025 (1 hour, 56 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2024-11857
A quick overview of all changes and news from the entire Total.js Platform. Read more about our work. Source: Read…
Comments Source: Read MoreÂ