In today’s fast-paced software development world, delivering high-quality web applications quickly and reliably is more critical than ever. Continuous Integration…
Development
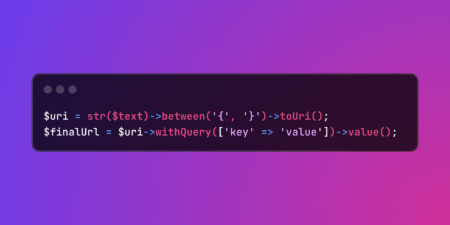
Laravel’s toUri() method converts strings to URI objects supporting fluent query parameter addition and modification. Streamline URL processing from text…
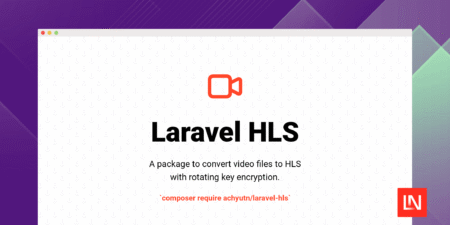
Laravel HLS is a package for generating HTTP Live Streaming (HLS) playlists and segments with AES-128 encryption. Convert your Eloquent…
Louis Vuitton has sent an email to its customers detailing a cyberattack that exposed personal information, making it the third…
A Maryland-based IT firm, Hill ASC Inc., has agreed to fork over at least $14.75 million in a settlement that…
The North Korean threat actors linked to the Contagious Interview campaign have been observed publishing another set of 67 malicious…
The FBI’s Atlanta Field Office has seized several major online platforms involved in video game piracy. These websites offered pirated…
Cybersecurity researchers have charted the evolution of a widely used remote access trojan called AsyncRAT, which was first released on…
AI agents promise to automate everything from financial reconciliations to incident response. Yet every time an AI agent spins up…
Governmental organizations in Southeast Asia are the target of a new campaign that aims to collect sensitive information by means…
Australia just made a significant move to future-proof its critical infrastructure and beef-up its OT Cybersecurity Standard. It has officially…
Thirteen individuals have been arrested in Romania as part of a major international operation targeting tax fraud linked to phishing…
A criminal investigation into Twitter has been initiated by French prosecutors, over allegations that its algorithm is manipulated for the…
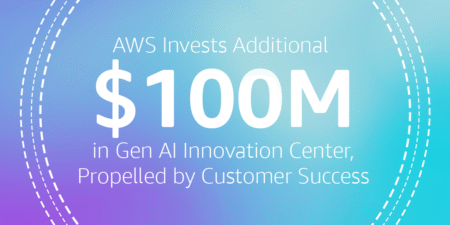
When we launched the AWS Generative AI Innovation Center in 2023, we had one clear goal: help customers turn AI…
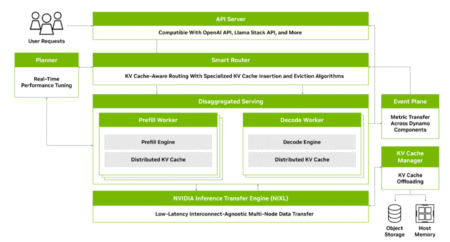
This post is co-written with Kshitiz Gupta, Wenhan Tan, Arun Raman, Jiahong Liu, and Eiluth Triana Isaza from NVIDIA. As…
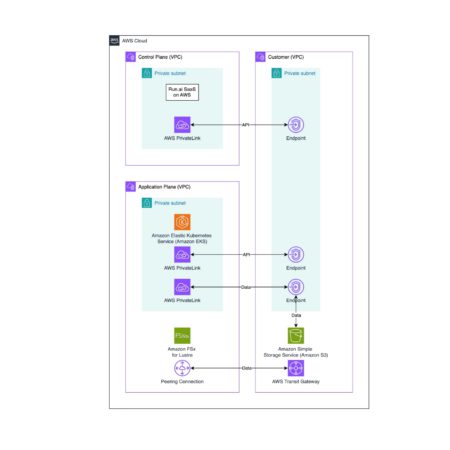
This post is co-written with Andrew Liu, Chelsea Isaac, Zoey Zhang, and Charlie Huang from NVIDIA. DGX Cloud on Amazon…
Cisco has released security updates to address a maximum-severity security flaw in Unified Communications Manager (Unified CM) and Unified Communications…
The French cybersecurity agency on Tuesday revealed that a number of entities spanning governmental, telecommunications, media, finance, and transport sectors…
CVE ID : CVE-2025-53639
Published : July 14, 2025, 8:15 p.m. | 6 hours, 36 minutes ago
Description : MeterSphere is an open source continuous testing platform. Prior to version 3.6.5-lts, the sortField parameter in certain API endpoints is not properly validated or sanitized. An attacker can supply crafted input to inject and execute arbitrary SQL statements through the sorting functionality. This could result in modification or deletion of database contents, with a potential full compromise of the application’s database integrity and availability. Version 3.6.5-lts fixes the issue.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-53101
Published : July 14, 2025, 8:15 p.m. | 6 hours, 36 minutes ago
Description : ImageMagick is free and open-source software used for editing and manipulating digital images. In versions prior to 7.1.2-0 and 6.9.13-26, in ImageMagick’s `magick mogrify` command, specifying multiple consecutive `%d` format specifiers in a filename template causes internal pointer arithmetic to generate an address below the beginning of the stack buffer, resulting in a stack overflow through `vsnprintf()`. Versions 7.1.2-0 and 6.9.13-26 fix the issue.
Severity: 7.4 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…