Learn how Actuated, Ampere, and Equinix collaborated to solve ARM64 CI/CD challenges for CNCF projects, enabling native builds that replaced…
Development
Explore the fundamentals of Node.js streams for efficient I/O operations. Learn how readable, writable, and transform streams work with practical…
This tutorial walks you through building and using the Ampere Porting Advisor and how to mitigate any issues. Continue reading…
Unlock the best practices for building scalable React apps. Explore strategies for performance, maintainability, state management, code splitting, and real-world…
Read Best Crypto Payments Gateways in 2025 and learn Web with SitePoint. Our web development and design tutorials, courses, and…
Learn how to build scalable WordPress sites with proper site structure planning. Discover key strategies for handling growth, traffic spikes,…
Best Crypto Payment Gateway for High Risk. Accept cryptocurrency payments with the best crypto payment gateway. Find reliable cryptocurrency payment…
Looking for Ahrefs alternatives? Click to find a detailed overview of the top 10 Ahrefs competitors and pick a tool…
Developers building learning platforms like Udemy can save time and scale faster with a specialized file infrastructure. Here’s how it…
Overview the top-tier Semrush competitors and learn how each platform can revamp your business with its tools, features, and unique…
Learn how developers can use Socialprofiler to analyze potential partners, investors, and collaborators before making critical business decisions. Continue reading…
Explore SSL certificate reselling: market growth, common challenges, auto-validation methods, and centralized lifecycle management. Continue reading Cost Effective Reseller Platforms…
Learn how OpenTelemetry achieved 15% cost savings and improved reliability by adding Arm64 support with Ampere processors. Discover how cross-architecture…
Learn what ArgoCD is and why it’s a leading GitOps tool for Kubernetes. This guide covers core concepts, architecture, and…
Your ultimate guide to the 5 best payment gateways for SaaS. Choose the best SaaS payment gateway to optimize your…
Traditional WordPress builders are outdated. See how Droip’s modern visual builder delivers true design freedom, clean code, and powerful features…
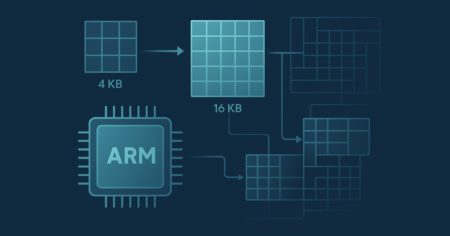
Optimize ARM64 performance with larger memory page sizes. Learn when 64K pages benefit databases, AI, and I/O workloads plus Linux…
Transform your daily work grind by automating emails, presentations, and data analysis with Google’s Gemini in Workspace. Continue reading Gemini…
White-label payment gateway guide: Unlock payment solutions with our white-label payment processing overview. Customize your payment gateway today! Continue reading…
Discover how Angular Signals revolutionize data flow with reactive variables, not streams. Learn production gotchas, when to choose Signals over…