CVE ID : CVE-2025-58163
Published : Sept. 3, 2025, 2:15 a.m. | 29 minutes ago
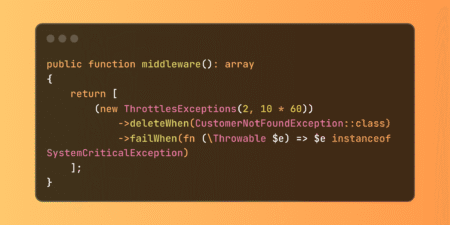
Description : FreeScout is a free help desk and shared inbox built with PHP’s Laravel framework. In versions 1.8.185 and below, the application performs deserialization of data that can allow authenticated attackers with knowledge of the application’s APP_KEY to achieve remote code execution. The vulnerability can be exploited via endpoint: `/help/{mailbox_id}/auth/{customer_id}/{hash}/{timestamp}` where the `customer_id` and `timestamp` parameters are processed through the decrypt function in `app/Helper.php` without proper validation. The vulnerable code performs decryption using Laravel’s built-in encryption functions, which subsequently deserializes the decrypted payload without sanitization. This is fixed in version 1.8.186.
Severity: 8.6 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…