In today’s digital age, the integration of technology into education has become essential for improving learning experiences and administrative efficiency.…
Development
#745 — July 18, 2025 Read on the Web JavaScript Weekly The JavaScript Date Quiz — Prepare to get irritated?…
You can think of the Model Context Protocol (MCP) as USB for large language models (LLMs), allowing an LLM to…
In a rare and urgent late-night address, a senior Singapore official confirmed that the country is currently facing a sophisticated…
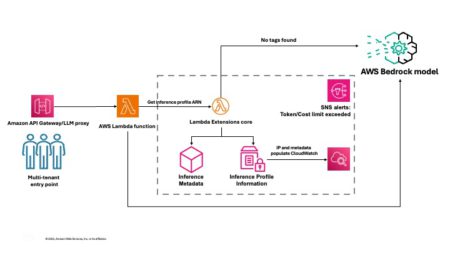
Successful generative AI software as a service (SaaS) systems require a balance between service scalability and cost management. This becomes…
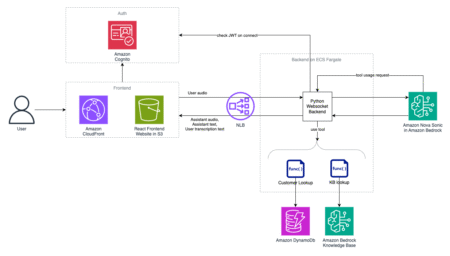
AI-powered speech solutions are transforming contact centers by enabling natural conversations between customers and AI agents, shortening wait times, and…
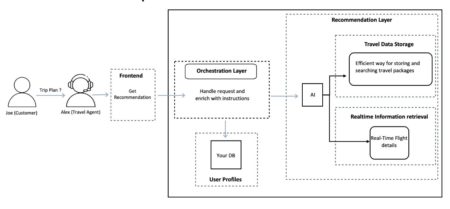
Generative AI is transforming how businesses deliver personalized experiences across industries, including travel and hospitality. Travel agents are enhancing their…
Signal-kloon TeleMessage SGNL gebruikte kwetsbare Spring Boot Actuator
Bepaalde versies van TeleMessage SGNL, een versleutelde berichtenapp die specifiek is ontworpen voor overheidsorganisaties en grote bedrijven, zijn kwetsbaar voor cyberaanvallen. Een oude versie van S …
Read more
Published Date:
Jul 18, 2025 (2 hours, 28 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-48927
CVE-2025-4892
Fancy Bear Hackers Attacking Governments, Military Entities With New Sophisticated Tools
The notorious Russian cyberespionage group Fancy Bear, also known as APT28, has intensified its operations against governments and military entities worldwide using an arsenal of sophisticated new too …
Read more
Published Date:
Jul 18, 2025 (2 hours, 4 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2023-38831
CVE-2023-23397
CVE-2023-20085
CVE ID : CVE-2025-6227
Published : July 18, 2025, 12:15 p.m. | 2 hours, 47 minutes ago
Description : Mattermost versions 10.5.x
Severity: 2.2 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7785
Published : July 18, 2025, 12:15 p.m. | 2 hours, 47 minutes ago
Description : A vulnerability classified as problematic was found in thinkgem JeeSite up to 5.12.0. This vulnerability affects the function sso of the file src/main/java/com/jeesite/modules/sys/web/SsoController.java. The manipulation of the argument redirect leads to open redirect. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. The patch is identified as 3d06b8d009d0267f0255acc87ea19d29d07cedc3. It is recommended to apply a patch to fix this issue.
Severity: 4.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2024-13175
Published : July 18, 2025, 2:15 p.m. | 47 minutes ago
Description : Authorization Bypass Through User-Controlled Key vulnerability in Vidco Software VOC TESTER allows Forceful Browsing.This issue affects VOC TESTER: before 12.41.0.
Severity: 5.5 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-46001
Published : July 18, 2025, 2:15 p.m. | 47 minutes ago
Description : An arbitrary file upload vulnerability in the is_allowed_file_type() function of Filemanager v2.3.0 allows attackers to execute arbitrary code via uploading a crafted PHP file.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-46002
Published : July 18, 2025, 2:15 p.m. | 47 minutes ago
Description : An issue in Filemanager v2.5.0 and below allows attackers to execute a directory traversal via sending a crafted HTTP request to the filemanager.php endpoint.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7784
Published : July 18, 2025, 2:15 p.m. | 47 minutes ago
Description : A flaw was found in the Keycloak identity and access management system when Fine-Grained Admin Permissions(FGAPv2) are enabled. An administrative user with the manage-users role can escalate their privileges to realm-admin due to improper privilege enforcement. This vulnerability allows unauthorized elevation of access rights, compromising the intended separation of administrative duties and posing a security risk to the realm.
Severity: 6.5 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7786
Published : July 18, 2025, 2:15 p.m. | 47 minutes ago
Description : A vulnerability, which was classified as problematic, has been found in Gnuboard g6 up to 6.0.10. This issue affects some unknown processing of the file /bbs/scrap_popin_update/qa/ of the component Post Reply Handler. The manipulation leads to cross site scripting. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 3.5 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
Artificial Intelligence (AI) continues to revolutionize industries, driving unprecedented productivity and efficiency. One of its most transformative effects is on the field of automation testing, where AI tools are helping QA teams write test scripts, identify bugs, and optimize test coverage faster than ever. Among today’s standout AI tools are GitHub Copilot vs Microsoft Copilot.
The post GitHub Copilot vs Microsoft Copilot: What’s the Real Difference? appeared first on Codoid.
Openbaar Ministerie koppelt digitale omgeving los van internet vanwege kwetsbaarheid
De digitale omgeving van het Openbaar Ministerie is gisteravond uit voorzorg losgekoppeld van het internet. Aanleiding hiervoor is een kwetsbaarheid in Citrix NetScaler.
Dit meldt minister Van Weel va …
Read more
Published Date:
Jul 18, 2025 (5 hours, 33 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-5777
Signal App Clone TeleMessage Vulnerability May Leak Passwords; Hackers Exploiting It
A critical security vulnerability in TeleMessageTM SGNL, an enterprise messaging system modeled after Signal, has been actively exploited by cybercriminals seeking to extract sensitive user credential …
Read more
Published Date:
Jul 18, 2025 (4 hours, 43 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-48927
CISA Releases 3 ICS Advisories Covering Vulnerabilities and Exploits
CISA issued three significant Industrial Control Systems (ICS) advisories on July 17, 2025, addressing critical vulnerabilities affecting energy monitoring, healthcare imaging, and access control syst …
Read more
Published Date:
Jul 18, 2025 (4 hours, 34 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-6185
CVE-2024-32861
CVE-2024-22774