To fight against cybercrime, Japan’s National Police Agency (NPA) has released a free decryption tool for victims of the Phobos…
Development
Cybersecurity researchers have disclosed a novel attack technique that allows threat actors to downgrade Fast IDentity Online (FIDO) key protections…
Microsoft has issued a warning about active cyberattacks targeting on-premises SharePoint servers widely used by government agencies and businesses. The…
Indian cryptocurrency exchange CoinDCX has confirmed a cyberattack that resulted in a loss of approximately $44 million. The CoinDCX cyberattack,…
A new zero-day vulnerability in CrushFTP file transfer servers is being actively exploited by cybercriminals, compromising systems around the world.…
The hacking group NoName057(16) has been operating since 2022, launching cyber attacks on government organisations, media bodies, critical infrastructure, and…
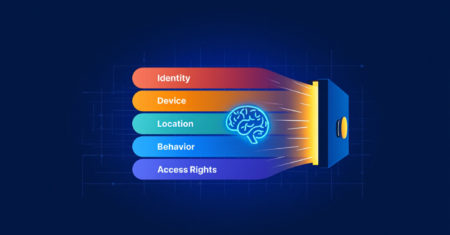
By 2025, Zero Trust has evolved from a conceptual framework into an essential pillar of modern security. No longer merely…
Even in well-secured environments, attackers are getting in—not with flashy exploits, but by quietly taking advantage of weak settings, outdated…
The China-linked cyber espionage group tracked as APT41 has been attributed to a new campaign targeting government IT services in…
Cybersecurity researchers have unearthed new Android spyware artifacts that are likely affiliated with the Iranian Ministry of Intelligence and Security…
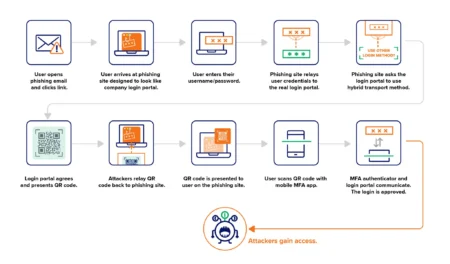
A phishing campaign is bypassing FIDO key authentication by exploiting cross-device sign-in features, a managed detection and response (MDR) provider…
This paper was accepted at the 2nd AI for Math Workshop at ICML 2025. We introduce Boolformer, a Transformer-based model…
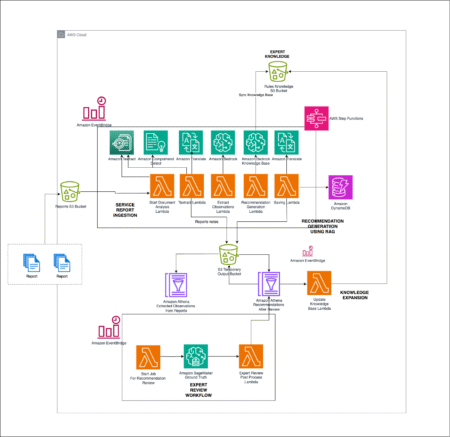
In the manufacturing world, valuable insights from service reports often remain underutilized in document storage systems. This post explores how…
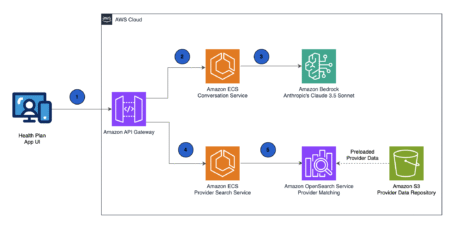
This post was written with Zach Heath of Kyruus Health. When health plan members need care, they shouldn’t need a…
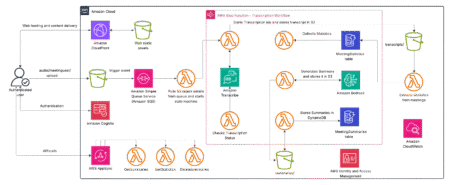
Extracting meaningful insights from unstructured data presents significant challenges for many organizations. Meeting recordings, customer interactions, and interviews contain invaluable…
Aligned representations across languages is a desired property in multilingual large language models (mLLMs), as alignment can improve performance in…
The ever-increasing parameter counts of deep learning models necessitate effective compression techniques for deployment on resource-constrained devices. This paper explores…
Latest PEAR Releases: Text_LanguageDetect 1.0.2 Text_LanguageDetect 1.0.1 Archive_Tar 1.6.0 Source: Read MoreÂ
The blog discusses how AI is leveling up the QA outsourcing industry by enhancing efficiency, improving code quality, and reducing costs. You will learn how to choose the right AI-driven QA partner and see how intelligent testing strategies can help you stay competitive in the digital age.
The post Lead with Intelligence: Rethink QA Outsourcing for the AI Age first appeared on TestingXperts.
CVE ID : CVE-2025-7913
Published : July 21, 2025, 12:15 a.m. | 23 hours, 59 minutes ago
Description : A vulnerability, which was classified as critical, was found in TOTOLINK T6 4.1.5cu.748_B20211015. Affected is the function updateWifiInfo of the component MQTT Service. The manipulation of the argument serverIp leads to buffer overflow. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…