Accordion menus are everywhere on the web because users want fast answers and smooth navigation. They help create clean, organized,…
Development
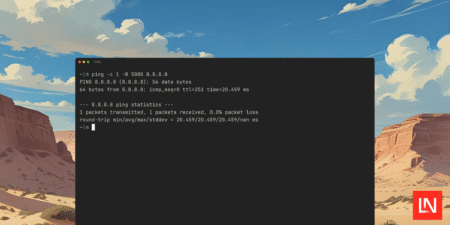
The spatie/ping PHP package provides a simple way to execute Internet Control Message Protocol (ICMP) ping commands and parse the…
Welcome to the first entry in our new series exploring the synergy between Agile methodologies and Accessibility practices, and how…
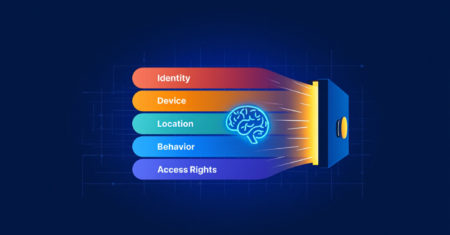
Zero Trust & Cybersecurity Mesh: The New Security Paradigm Traditional cybersecurity methods have fallen apart under their own presumptions in…
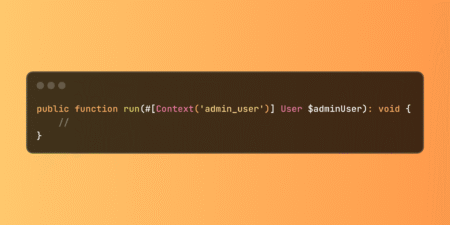
Laravel’s Context system enables clean data sharing between database seeders through the Context facade and attribute-based injection. Eliminates redundant queries…
A new attack campaign has compromised more than 3,500 websites worldwide with JavaScript cryptocurrency miners, marking the return of browser-based…
Hewlett-Packard Enterprise (HPE) has released security updates to address a critical security flaw affecting Instant On Access Points that could…
Microsoft on Sunday released security patches for an actively exploited security flaw in SharePoint and also disclosed details of another…
To fight against cybercrime, Japan’s National Police Agency (NPA) has released a free decryption tool for victims of the Phobos…
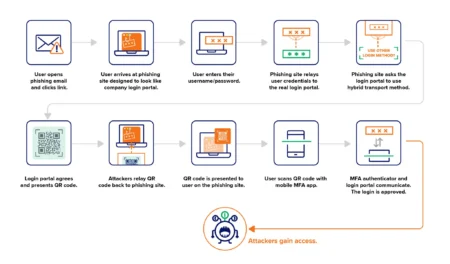
Cybersecurity researchers have disclosed a novel attack technique that allows threat actors to downgrade Fast IDentity Online (FIDO) key protections…
Microsoft has issued a warning about active cyberattacks targeting on-premises SharePoint servers widely used by government agencies and businesses. The…
Indian cryptocurrency exchange CoinDCX has confirmed a cyberattack that resulted in a loss of approximately $44 million. The CoinDCX cyberattack,…
A new zero-day vulnerability in CrushFTP file transfer servers is being actively exploited by cybercriminals, compromising systems around the world.…
The hacking group NoName057(16) has been operating since 2022, launching cyber attacks on government organisations, media bodies, critical infrastructure, and…
By 2025, Zero Trust has evolved from a conceptual framework into an essential pillar of modern security. No longer merely…
Even in well-secured environments, attackers are getting in—not with flashy exploits, but by quietly taking advantage of weak settings, outdated…
The China-linked cyber espionage group tracked as APT41 has been attributed to a new campaign targeting government IT services in…
Cybersecurity researchers have unearthed new Android spyware artifacts that are likely affiliated with the Iranian Ministry of Intelligence and Security…
A phishing campaign is bypassing FIDO key authentication by exploiting cross-device sign-in features, a managed detection and response (MDR) provider…
This paper was accepted at the 2nd AI for Math Workshop at ICML 2025. We introduce Boolformer, a Transformer-based model…