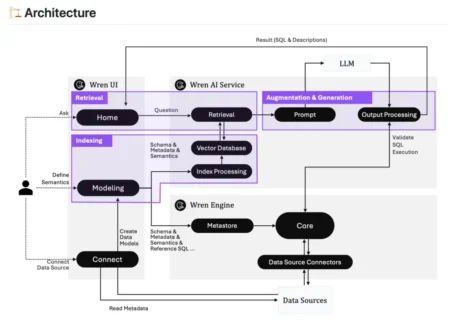
WrenAI is an open-source Generative Business Intelligence (GenBI) agent developed by Canner, designed to enable seamless, natural-language interaction with structured…
Development
Table of contents Introduction The Surge of Vibe Coding: Data and Adoption Trends How Vibe Coding Works: Workflow Innovations Key…
The global proxy market is experiencing rapid expansion in 2025, with the industry estimated to be valued at $2.5billion and…
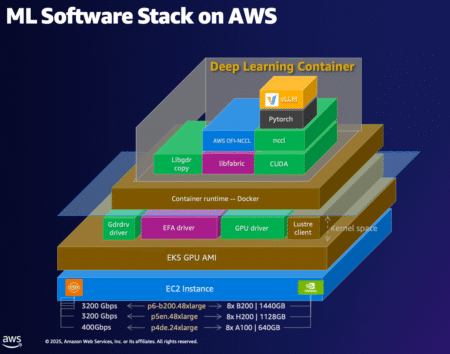
Data science teams working with artificial intelligence and machine learning (AI/ML) face a growing challenge as models become more complex.…
In 2024, the Ministry of Economy, Trade and Industry (METI) launched the Generative AI Accelerator Challenge (GENIAC)—a Japanese national program…
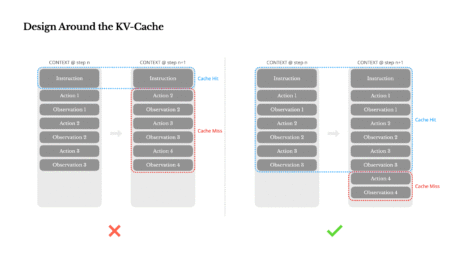
Building effective AI agents means more than just picking a powerful language model. As the Manus project discovered, how you…
In this tutorial, we begin by setting up a compact yet capable AI agent that runs smoothly, leveraging Hugging Face transformers.…
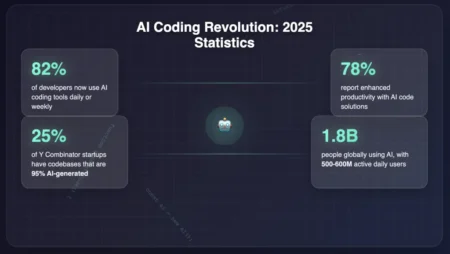
The Allure and The Hype Vibe coding—constructing applications through conversational AI rather than writing traditional code—has surged in popularity, with…
This work evaluates the potential of large language models (LLMs) to power digital assistants capable of complex action execution. These…
This paper was accepted at the Workshop on Large Language Model Memorization (L2M2) 2025. Large Language Models (LLMs) have quickly…
AI is transforming accessibility testing by automating audits and reducing effort, but it can’t replace human judgment. This blog explores why a hybrid approach—AI-powered tools plus human-in-the-loop validation—is essential for reliable, inclusive digital experiences. Learn how Tx leverages this synergy to deliver accurate, scalable, and regulation-compliant accessibility testing solutions.
The post Win the Accessibility Game: Combining AI with Human Judgment first appeared on TestingXperts.
Artificial Intelligence is no longer a distant dream; it’s rapidly reshaping how we build, test, and release software. And just when we thought GPT-4o was groundbreaking, OpenAI is gearing up to launch its next leap: GPT-5. For software testers, QA engineers, and automation experts, this isn’t merely another version upgrade; it’s a complete transformation. GPT-5
The post GPT-5 is Coming: Revolutionizing Software Testing appeared first on Codoid.
CVE ID : CVE-2025-44658
Published : July 21, 2025, 4:15 p.m. | 1 day, 8 hours ago
Description : In Netgear RAX30 V1.0.10.94, a PHP-FPM misconfiguration vulnerability is caused by not following the specification to only limit FPM to .php extensions. An attacker may exploit this by uploading malicious scripts disguised with alternate extensions and tricking the web server into executing them as PHP, bypassing security mechanisms based on file extension filtering. This may lead to remote code execution (RCE), information disclosure, or full system compromise.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7393
Published : July 21, 2025, 5:15 p.m. | 1 day, 7 hours ago
Description : Improper Restriction of Excessive Authentication Attempts vulnerability in Drupal Mail Login allows Brute Force.This issue affects Mail Login: from 3.0.0 before 3.2.0, from 4.0.0 before 4.2.0.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-44654
Published : July 21, 2025, 6:15 p.m. | 1 day, 6 hours ago
Description : In Linksys E2500 3.0.04.002, the chroot_local_user option is enabled in the vsftpd configuration file. This could lead to unauthorized access to system files, privilege escalation, or use of the compromised server as a pivot point for internal network attacks.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-52362
Published : July 21, 2025, 8:15 p.m. | 1 day, 4 hours ago
Description : Server-Side Request Forgery (SSRF) vulnerability exists in the URL processing functionality of PHProxy version 1.1.1 and prior. The input validation for the _proxurl parameter can be bypassed, allowing a remote, unauthenticated attacker to submit a specially crafted URL
Severity: 9.1 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2012-10020
Published : July 22, 2025, 2:15 a.m. | 22 hours, 29 minutes ago
Description : The FoxyPress plugin for WordPress is vulnerable to arbitrary file uploads due to missing file type validation in the uploadify.php file in versions up to, and including, 0.4.2.1. This makes it possible for unauthenticated attackers to upload arbitrary files on the affected sites server which may make remote code execution possible.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2015-10137
Published : July 22, 2025, 2:15 a.m. | 22 hours, 29 minutes ago
Description : The Website Contact Form With File Upload plugin for WordPress is vulnerable to arbitrary file uploads due to missing file type validation in the ‘upload_file()’ function in versions up to, and including, 1.3.4. This makes it possible for unauthenticated attackers to upload arbitrary files on the affected sites server which may make remote code execution possible.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6585
Published : July 22, 2025, 5:15 a.m. | 19 hours, 29 minutes ago
Description : The WP JobHunt plugin for WordPress is vulnerable to Insecure Direct Object Reference in all versions up to, and including, 7.2 via the cs_remove_profile_callback() function due to missing validation on a user controlled key. This makes it possible for authenticated attackers, with Subscriber-level access and above, to delete accounts of other users including admins.
Severity: 8.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7645
Published : July 22, 2025, 7:15 a.m. | 17 hours, 29 minutes ago
Description : The Extensions For CF7 (Contact form 7 Database, Conditional Fields and Redirection) plugin for WordPress is vulnerable to arbitrary file deletion due to insufficient file path validation in the ‘delete-file’ field in all versions up to, and including, 3.2.8. This makes it possible for unauthenticated attackers to delete arbitrary files on the server, when an administrator deletes the submission, which can easily lead to remote code execution when the right file is deleted (such as wp-config.php).
Severity: 8.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…