Writing documentation looks easy, but it is one of the most critical parts of your customer support and growth strategy.…
Development
Imagine this. A machine with no education. No equations. No Newton. No relativity. Nothing. And yet… it sat, observed reality,…
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
In existence since just July of 2019, the Pan African Payment and Settlement System (PAPSS) has in many ways surpassed…
Can you believe it’s already June? As we move further into 2025, it’s a perfect time to reflect on the…
Angular Signals State Management is a new, built-in approach that simplifies state handling in Angular. Unlike RxJS or NgRx, Signals…
The Great Marketing Evolution Marketing today is no longer about sending the right message—it’s about delivering that message at the…
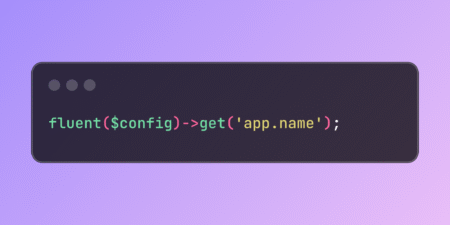
Laravel’s fluent() helper function simplifies multi-dimensional array handling by providing intuitive access to nested data structures. This utility enables dot…
Quite often I see people searching for “cron” in the Laravel context. The framework has a mechanism on top of…
Have you ever tried to import 1 million rows from CSV into the DB? It’s a tricky task that can…
Adobe on Tuesday pushed security updates to address a total of 254 security flaws impacting its software products, a majority…
Microsoft has released patches to fix 67 security flaws, including one zero-day bug in Web Distributed Authoring and Versioning (WebDAV)…
Cybersecurity researchers have exposed the inner workings of an Android malware called AntiDot that has compromised over 3,775 devices as…
The U.S. Department of Justice has filed a civil forfeiture complaint to seize more than $225.3 million in cryptocurrency that…
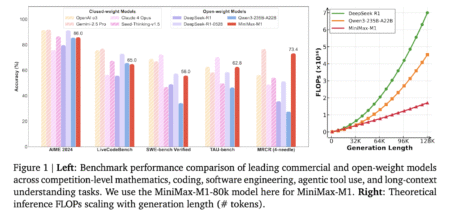
The Challenge of Long-Context Reasoning in AI Models Large reasoning models are not only designed to understand language but are…
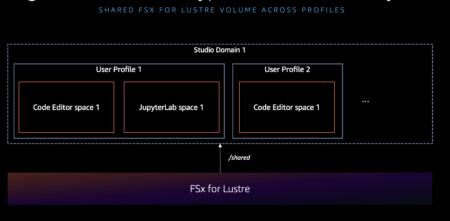
Modern generative AI model providers require unprecedented computational scale, with pre-training often involving thousands of accelerators running continuously for days,…